
Hackers are cloning YubiKeys via new side-channel exploit
Many enterprises rely on the YubiKey as a major part of their identity authentication strategy. It […]

New ALPHV-like ransomware targets VMware ESXi servers
Researchers at Trusec recently discovered a new ransomware-as-a-service group called Cicada3301. The gang provides its affiliates with a […]

‘Unusual’ Voldemort cyberespionage attack impersonates tax authorities
Researchers have identified an attack that impersonates tax authorities from several countries to compromise organizations and […]

Dutch regulator fines Clearview €30 million… or more
The Dutch Data Protection Authority, Autoriteit Persoonsgegevens, is the latest European regulator to crack down on […]

Attackers are exploiting vulnerabilities at a record pace—here’s what to do about it
“Another day, another vulnerability” is a familiar refrain among security teams worldwide. One of the most […]

Thousands of abandoned PyPI projects could be hijacked: Report
A vulnerability in abandoned Python open source repository projects could allow over 20,000 packages of code […]

Building a Culture of Email Security Awareness
Human error remains a significant risk for organizations when it comes to cyber threats. In fact, […]

6 things hackers know that they don’t want security pros to know that they know
Security professionals have good insights into the technical tactics, techniques, and procedures (TTPs) that threat actors […]
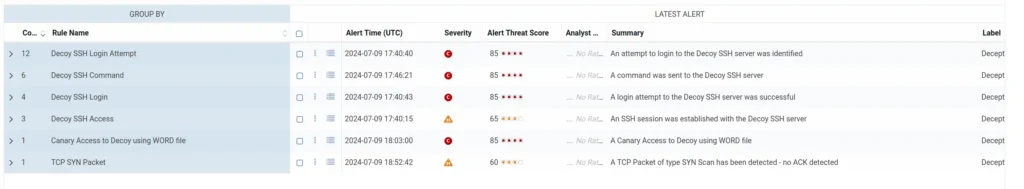
The Role of Deception in Securing Active Directory
Introduction 90% of businesses around the world use Active Directory as their primary Directory Service. It […]
WeSecureApp is Now Strobes: A Message from Our CEO
Hello everyone, I’m excited to share some big news with you today. WeSecureApp is evolving into […]
