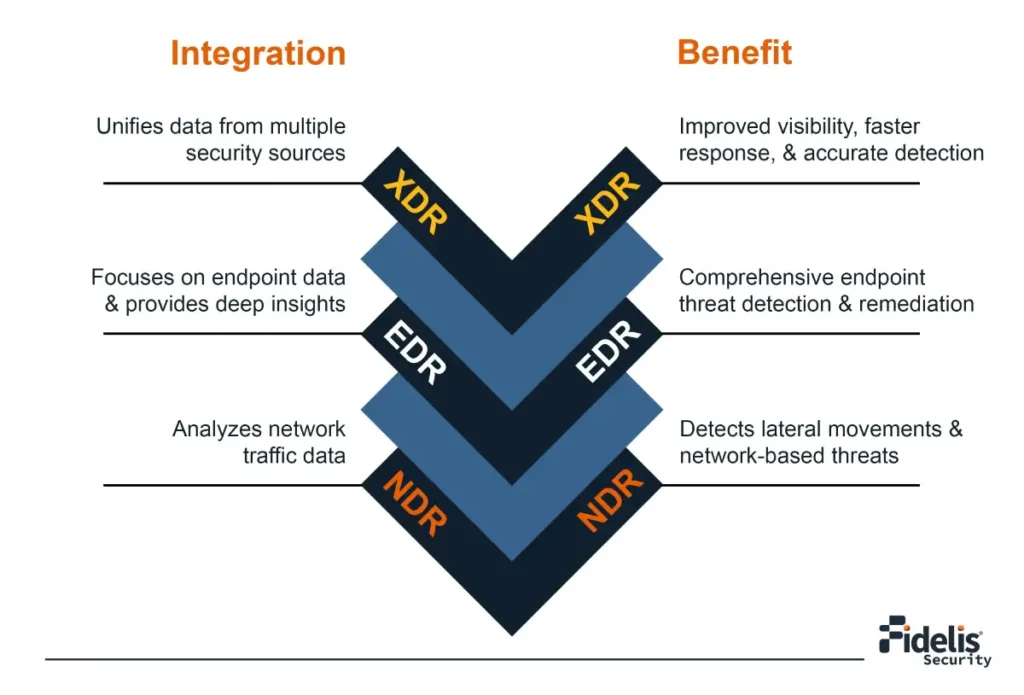
Understanding XDR, NDR, and EDR: A Comprehensive Guide to Modern Cybersecurity Solutions
Cybersecurity leaders should be well-versed with current trends and best practices in security management to effectively […]

Transport for London continues to struggle with cyber attack
Transport for London, which manages public transport for the British capital, continues to experience technical disruptions […]

Application detection and response is the gap-bridging technology we need
The concept of detection and response is far from new in cybersecurity — in fact, it’s […]

The 18 biggest data breaches of the 21st century
In today’s data-driven world, data breaches can affect hundreds of millions or even billions of people […]

5G and SASE: Reimagining WAN Infrastructure
Cellular connectivity was often relegated to a failover connection option. Because of its mobile or remote […]

Oracle adds Zero Trust Packet Routing capability to its cloud platform
Oracle has added a new zero trust capability to its cloud platform which it says prevents […]

TLS security subverted due to CA use of outdated WHOIS servers
WHOIS clients across the internet, including those used by email servers and Certificate Authorities (CAs), are […]

Microsoft warns of bug reversing updates on old Windows 10, patches critical flaws
In a busy Patch Tuesday update, Microsoft addressed over 70 security vulnerabilities across various products, including […]
12 dark web monitoring tools
What is dark web monitoring? Dark web monitoring is a service often offered by cybersecurity vendors […]
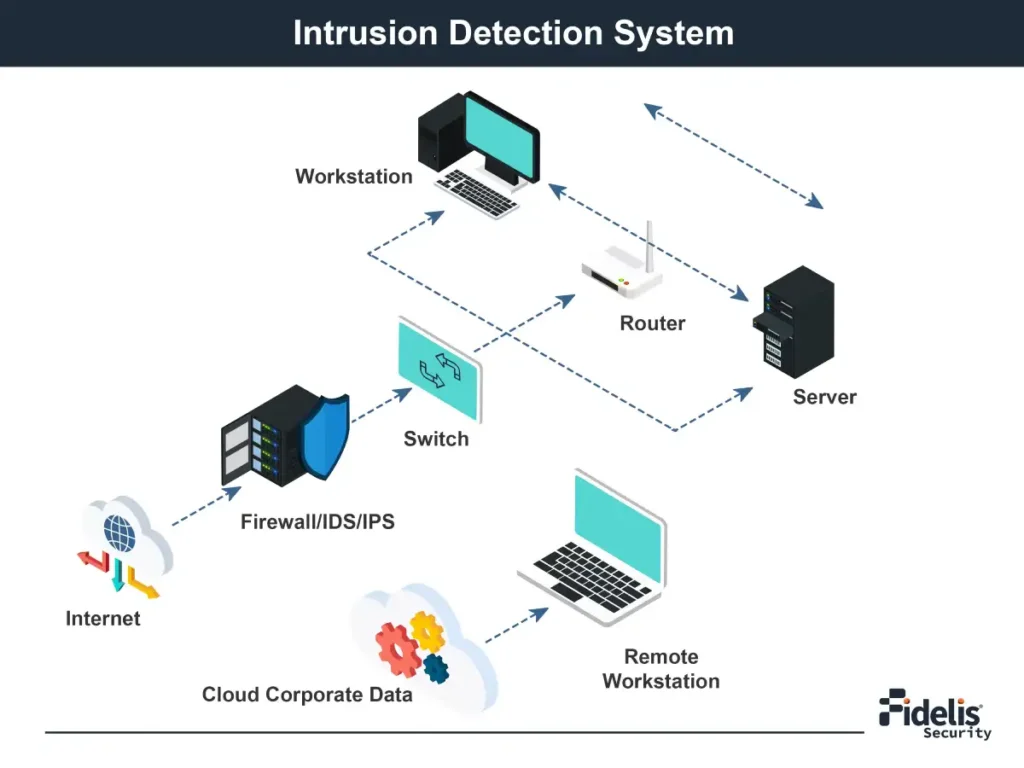
The Evolution of NDR: From IDS to Advanced Threat Detection
“In cybersecurity, the ability to detect threats faster than they evolve is not just an advantage—it’s […]
