Cybersecurity Is Broken And Zero Trust Alone Won’t Fix It
In the dependent world on digital infrastructure, cyber security has become the cornerstone of organizational flexibility. […]

Cybersicherheitsausgaben wachsen langsamer
Die Ausgaben steigen weltweit, in Deutschland aber mit leichter Delle. PeopleImages.com – Yuri A Viele Unternehmen […]

Ermittler stoppen Erpresser-Software von Blacksuit/Royal
Die Angreifer verschlüsseln Daten nicht nur, sondern stehlen diese vorher. AIBooth – shutterstock.com Fast 200 Opfer […]

Nach Flugausfällen sprechen Hacker und Kreml von Angriff
Im Kreml spricht man von alarmierenden Nachrichten. FOTOGRIN – shutterstock.com In Moskau sind nach einem mutmaßlichen […]

The healthcare industry is at a cybersecurity crossroads
Healthcare is one of the largest industries in the world. In the US, healthcare spending accounts […]

How AI red teams find hidden flaws before attackers do
AI systems present a new kind of threat environment, leaving traditional security models — designed for […]

Cyber Circle: Awareness Training neu gedacht
Cybersicherheit hat sich zu einer der wichtigsten Prioritäten für Unternehmen und Regierungen entwickelt, und die digitale […]

Chinese ‘Fire Ant’ spies start to bite unpatched VMware instances
Suspected China-aligned actors are running a new “Fire Ant” espionage campaign, active since early 2025, that […]

Fidelis Elevate® Deep Visibility: The Force Multiplier for Modern Security Operations
Security teams struggle to detect and respond to attacks across expanding environments. Cloud systems, digital initiatives, […]
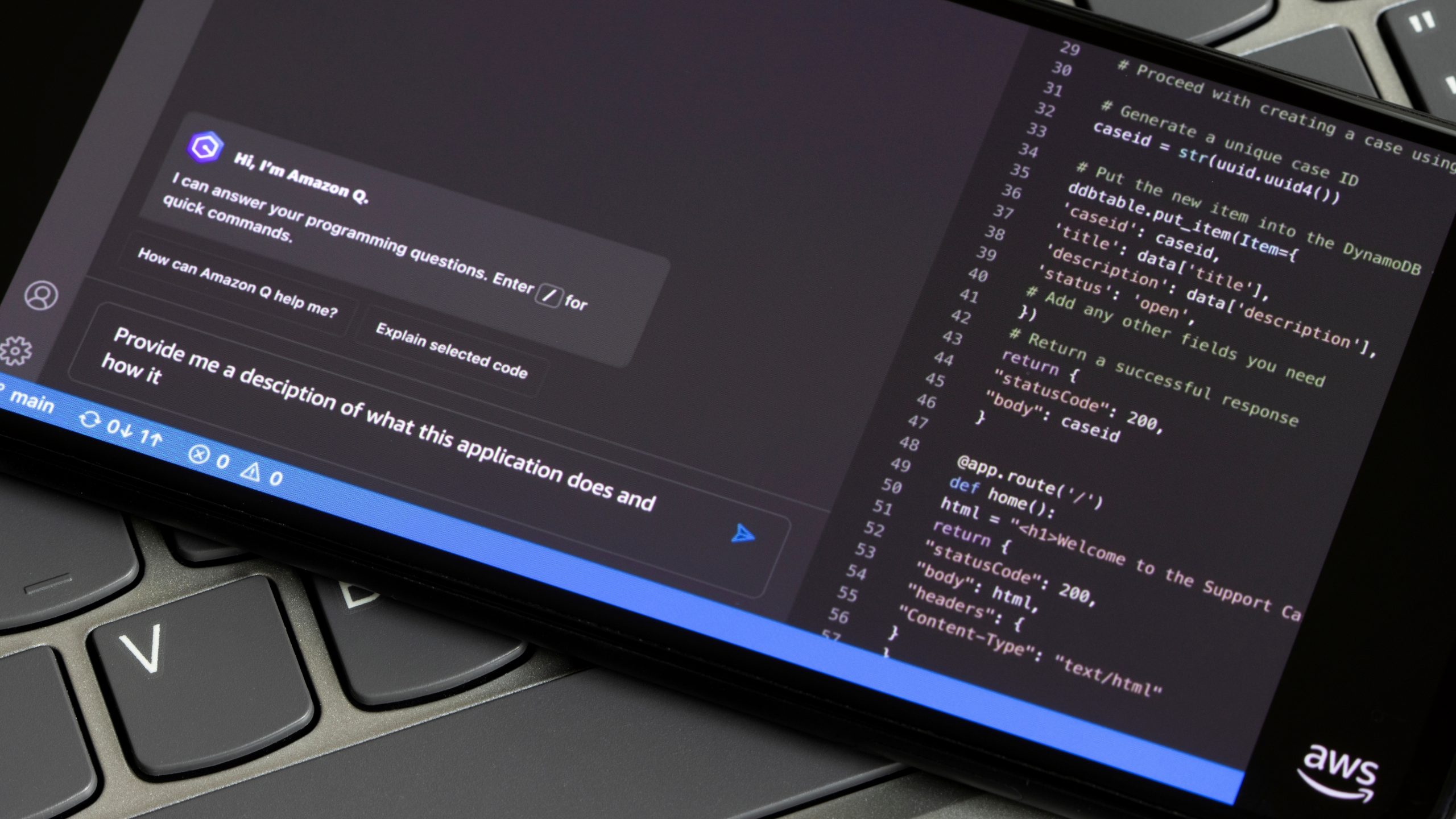
Entwickler-Tool von Amazon verseucht
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/07/Tada_Images-shutterstock_2395625183-NR_16z9.jpg?quality=50&strip=all 5984w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Tada_Images-shutterstock_2395625183-NR_16z9.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Tada_Images-shutterstock_2395625183-NR_16z9.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Tada_Images-shutterstock_2395625183-NR_16z9.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Tada_Images-shutterstock_2395625183-NR_16z9.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Tada_Images-shutterstock_2395625183-NR_16z9.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Tada_Images-shutterstock_2395625183-NR_16z9.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Tada_Images-shutterstock_2395625183-NR_16z9.jpg?resize=150%2C84&quality=50&strip=all 150w, […]
