
Why Your Remote Workforce Needs EDR: Beyond VPNs and Firewalls [2025 Guide]
Companies now need EDR to protect their remote workforce because old security measures just don’t cut […]

ECScape: New AWS ECS flaw lets containers hijack IAM roles without breaking out
At Black Hat USA 2025, Sweet Security’s Naor Haziz revealed a significant privilege escalation flaw in […]
How to Achieve Encrypted Traffic Visibility and Monitoring Without Breaking Privacy
In today’s networks, more than 90% of traffic is encrypted, obscuring both legitimate business data and […]

Beyond cryptocurrency: Blockchain 101 for CISOs and why it matters
When I first heard someone suggest blockchain for enterprise cybersecurity, I nearly rolled my eyes. At […]

13 Produkt-Highlights der Black Hat USA
Das Mandalay Bay Convention Center wird zur Black Hat USA zum Cybersecurity-Hub – 2025 lag der […]
How India’s fintech fraud patterns are evolving in 2025
Accelerated digitalization, embedded finance, and the clear regulatory environment have been precipitating the swift transformation of […]

What is a CISO? The top IT security leader role explained
The chief information security officer (CISO) is the top-level executive responsible for an organization’s information and […]
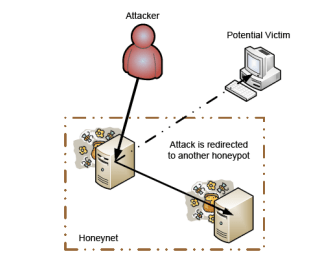
A Practical Guide to Honeypots
In this section, we describe Network Intrusion Detection Systems (IDS)—the traditional approach to network security.We also […]

So sparen CISOs, ohne die Sicherheit zu torpedieren
Geht’s dem Security-Budget an den Kragen, ist der Spielraum für CISOs denkbar gering. TippaPatt | shutterstock.com […]

Black Hat 2025 Recap: A look at new offerings announced at the show
Black Hat 2025 is on its home stretch, having gathered together thousands of security professionals to […]
