
Erneute Phishing-Attacke auf IHK-Unternehmen
Hacker versuchen erneut an Daten von IHK-Unternehmen zu gelangen. janews – Shutterstock.com Cyberkriminelle lassen sich immer […]

Chinas Cyber-Pandas greifen Telekom-Unternehmen an
Setzt China im Rahmen seiner Belt and Road Initiative auf Cyberspionage? ndutfrea/shutterstock.com Dank des von ihm […]

Weaponized pen testers are becoming a new hacker staple
Malicious adaptations of popular red teaming tools like Cobalt Strike and Metasploit are causing substantial disruption, […]

11 biggest financial sector cybersecurity threats
The financial sector faces a wide array of serious security threats that will only increase as […]

Palo Alto Networks zero-day firewall flaws caused by basic dev mistakes
Palo Alto Networks has issued fixes for two actively exploited vulnerabilities that impact its firewalls and […]
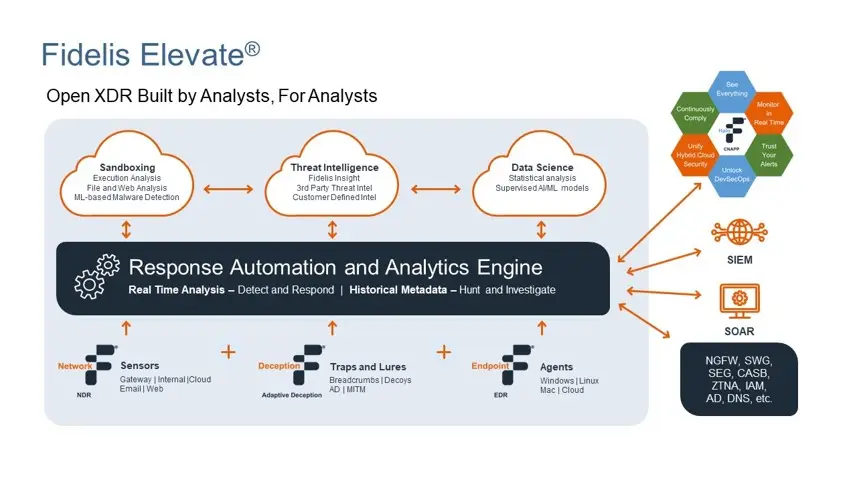
Cracking Threat Hunting & IR with XDR
Did you know that 68% of companies that hunt threats see their overall security improve? Cyber-attacks […]

At Ignite, Microsoft looks to genAI, exposure managment, and new bug bounties to secure enterprise IT
Microsoft announced a host of new security measures at its annual Ignite conference, with the goal […]
Aadhaar Data Vault: Enhancing Security and Privacy
The Aadhaar ecosystem is a cornerstone of India’s digital infrastructure, enabling millions of citizens to access […]

T-Mobile US von China gehackt
Erst hat die chinesische Hackergruppe Salt Typhoon Trumps Handy gehackt und jetzt T-Mobile USA. Chebakalex7/shutterstock.com Die […]

Verteidigungsminister Pistorius vermutet Sabotage
Bundesverteidigungsminister Boris Pistorius (SPD): “Niemand glaubt, dass diese Kabel aus Versehen durchtrennt worden sind.” Alexandros Michailidis […]
