
Cyberbedrohungen erkennen und reagieren: Was NDR, EDR und XDR unterscheidet
Mit Hilfe von NDR, EDR und XDR können Unternehmen Cyberbedrohungen in ihrem Netzwerk aufspüren. Foto: alphaspirit.it […]
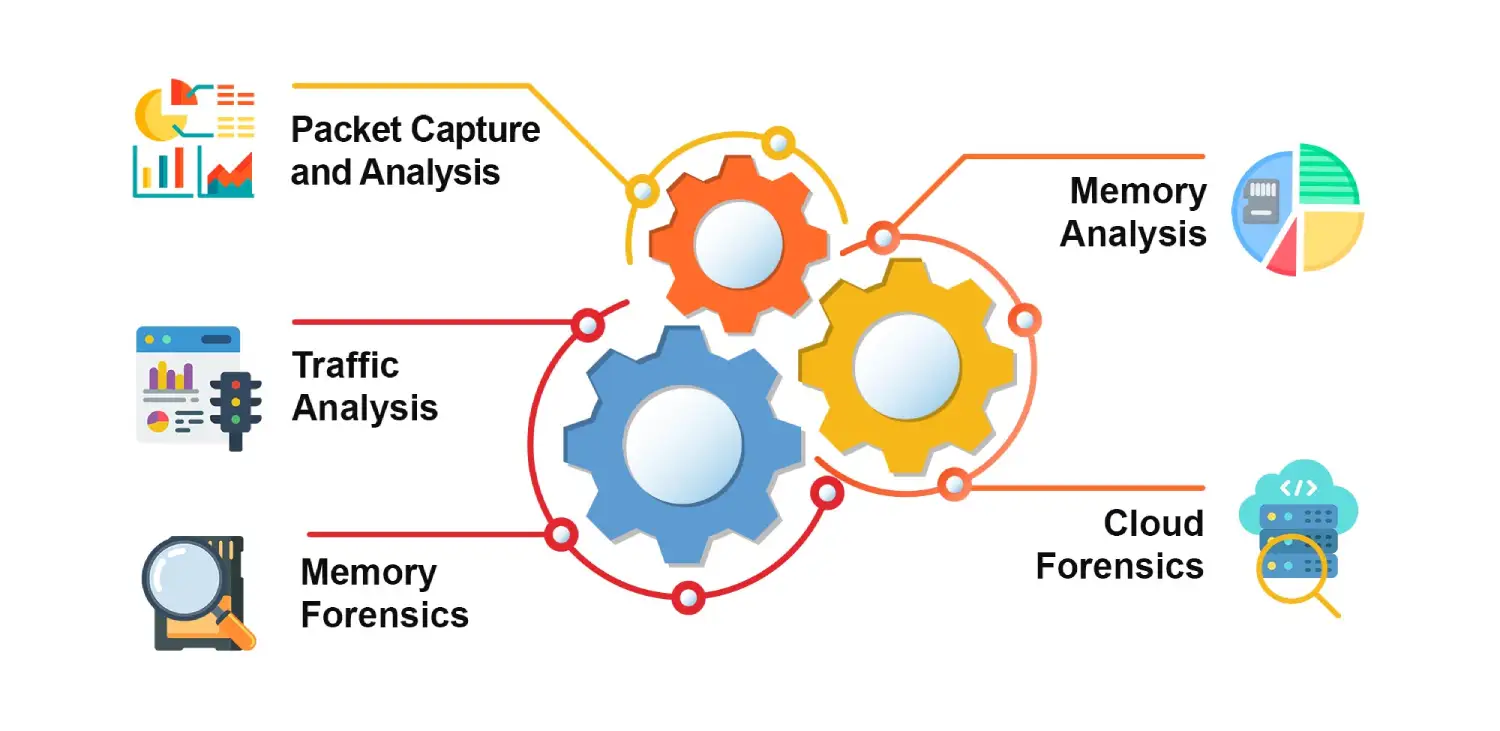
Network Forensics: Tracking, Investigating and Identifying Threats
What is Network Forensics? “Network forensics is a science that centers on the discovery and retrieval […]
Strengthening Cloud Defense with XDR: Why It’s Your Best Move in 2025
Cloud security isn’t optional anymore—it’s essential. More companies are shifting to the cloud, which makes their […]

Ransomware-Angriff beeinträchtigt IT von Starbucks
srcset=”https://b2b-contenthub.com/wp-content/uploads/2024/11/shutterstock_2538779037.jpg?quality=50&strip=all 6000w, https://b2b-contenthub.com/wp-content/uploads/2024/11/shutterstock_2538779037.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2024/11/shutterstock_2538779037.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2024/11/shutterstock_2538779037.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2024/11/shutterstock_2538779037.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2024/11/shutterstock_2538779037.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2024/11/shutterstock_2538779037.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2024/11/shutterstock_2538779037.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

QNAP fixes critical security holes in its networking solutions
Network and software solutions provider QNAP — whose customers include trusted IT service providers like Accenture, […]

Starbucks operations hit after ransomware attack on supply chain software vendor
Starbucks is grappling with operational challenges after a ransomware attack on a third-party software provider, affecting […]

9 VPN alternatives for securing remote network access
Once the staple for securing employees working remotely, VPNs were designed to provide secure access to […]
Cybersecurity in der Lieferkette Wie Sie Ihre Software-Supply-Chain schützen
Um Ihre Software-Lieferkette zu schützen, kann Generative AI sehr hilfreich sein. NTPY -Shutterstock.com Es klingt wie […]

Australia’s first Cyber Security Act passes both houses
The Cyber Security Legislative Reforms proposed by the Australian federal government passed both houses on 25 November, […]

Vossko von Ransomware-Attacke getroffen
Die Systeme des Lebensmittelproduzenten Vossko wurden von Hackern angegriffen. Vossko Nach eigenen Angaben hat Vossko am […]
