
Threat actors using Google Gemini to amplify attacks: Report
Government-backed threat actors are currently using Google’s Gemini AI service to expand their capabilities, part of […]
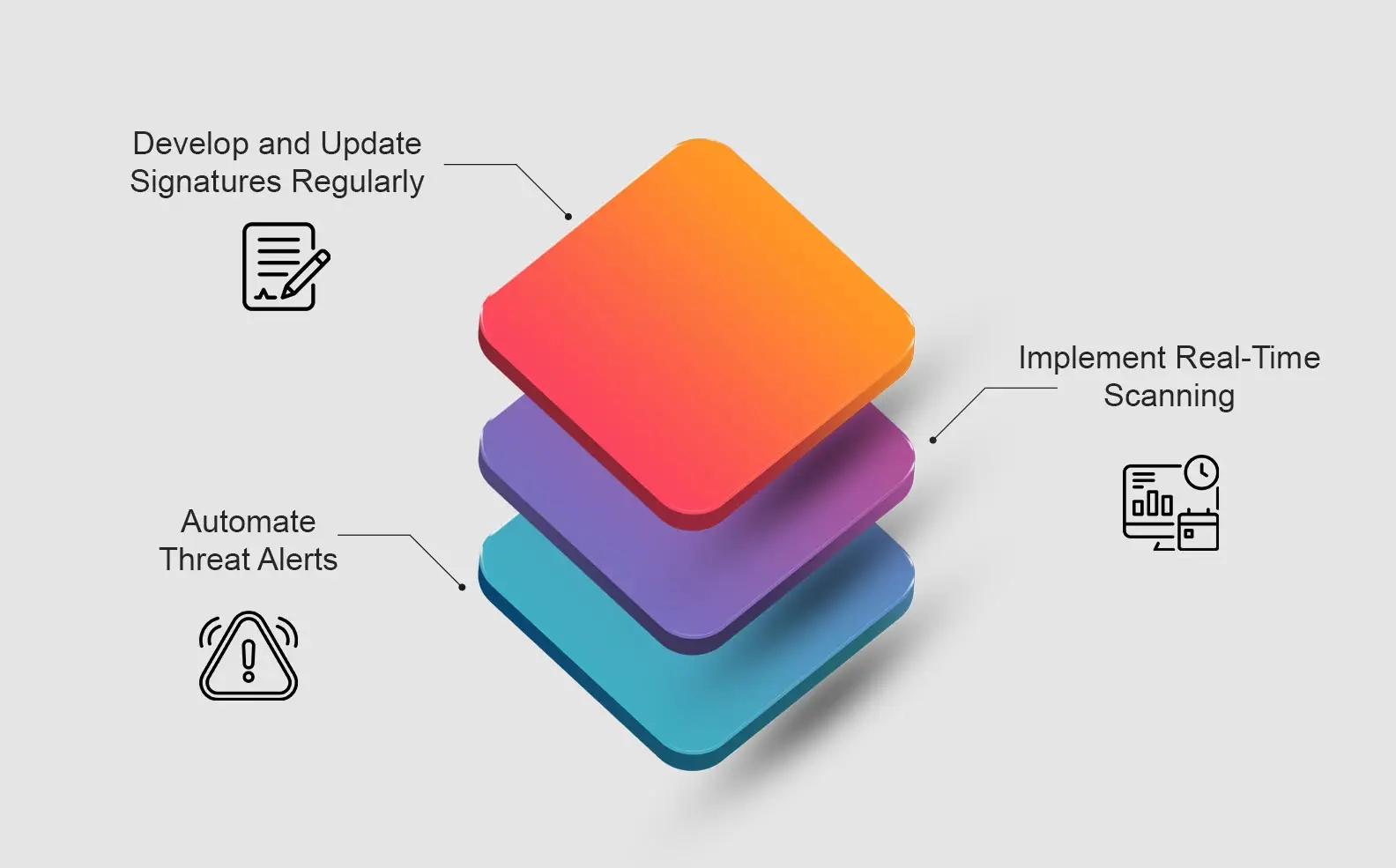
Breaking Down Signature-Based Detection: A Practical Guide
Nearly 90% of cyberattacks are known methods that proper systems can detect, but most organizations don’t […]

Ransomware: Schwere Versäumnisse in deutschen Unternehmen
Laut einer Umfrage benötigen deutsche Unternehmen im Vergleich zu anderen Ländern mehr Zeit und Geld, um […]

Download our security information and event management (SIEM) tools buyer’s guide
From the editors of CSO, this enterprise buyer’s guide helps IT security staff understand what SIEM […]

New phishing campaign targets users in Poland and Germany
An ongoing phishing campaign, presumably by an advanced persistent threat (APT) actor, is seen dropping a […]

CISOs are moving closer to the board — but budget hurdles remain
In recent years, CISOs have often felt that their board of directors did not take them seriously. […]

Active Directory Incident Response: Key Things to Keep in Mind
Active Directory (AD) is crucial for network security as it controls access to sensitive data, making […]

Want to be an effective cybersecurity leader? Learn to excel at change management
If there’s one thing that’s inevitable in cybersecurity, it’s change. Ever-evolving technology requires new protections, threats […]

Unknown threat actor targeting Juniper routers with backdoor: Report
Network administrators using routers from Juniper Networks are being urged to scan for possible compromise after […]

CISA warns of critical, high-risk flaws in ICS products from four vendors
The US Cybersecurity and Infrastructure Security Agency has issued advisories for 11 critical and high-risk vulnerabilities […]
