
CIOs and CISOs grapple with DORA: Key challenges, compliance complexities
In force since January, the Digital Operational Resilience Act (DORA) has required considerable effort from CIOs […]

Die besten Cyber-Recovery-Lösungen
Nicht greifende Recovery-Prozesse sind für Unternehmen ein Albtraumszenario, das dank ausgefeilter Angriffe immer öfter zur Realität […]

Police arrest teenager suspected of hacking NATO and numerous Spanish institutions
Spain‘s National Police, in a joint operation with the Civil Guard, has arrested an 18-year-old suspected […]
Port Binding Shellcode Remote Shellcode
When a host is exploited remotely, a multitude of options are available to gain access to […]

Port Binding Shellcode Remote Shellcode
When a host is exploited remotely, a multitude of options are available to gain access to […]

Spy vs spy: Security agencies help secure the network edge
The national intelligence services of five countries have offered enterprises advice on beating spies at their […]
Malicious package found in the Go ecosystem
A malicious typosquat package has been found in the Go language ecosystem. The package, which contains a backdoor […]

Ransomware-Angriff auf Escada
Der Modehersteller Escada wird von einer Ransomware-Bande mit gestohlenen Daten erpresst. Indoor Vision – Shutterstock Die […]

Lazarus Group tricks job seekers on LinkedIn with crypto-stealer
North Korea-linked Lazarus Group is duping job seekers and professionals in an ongoing campaign that runs […]
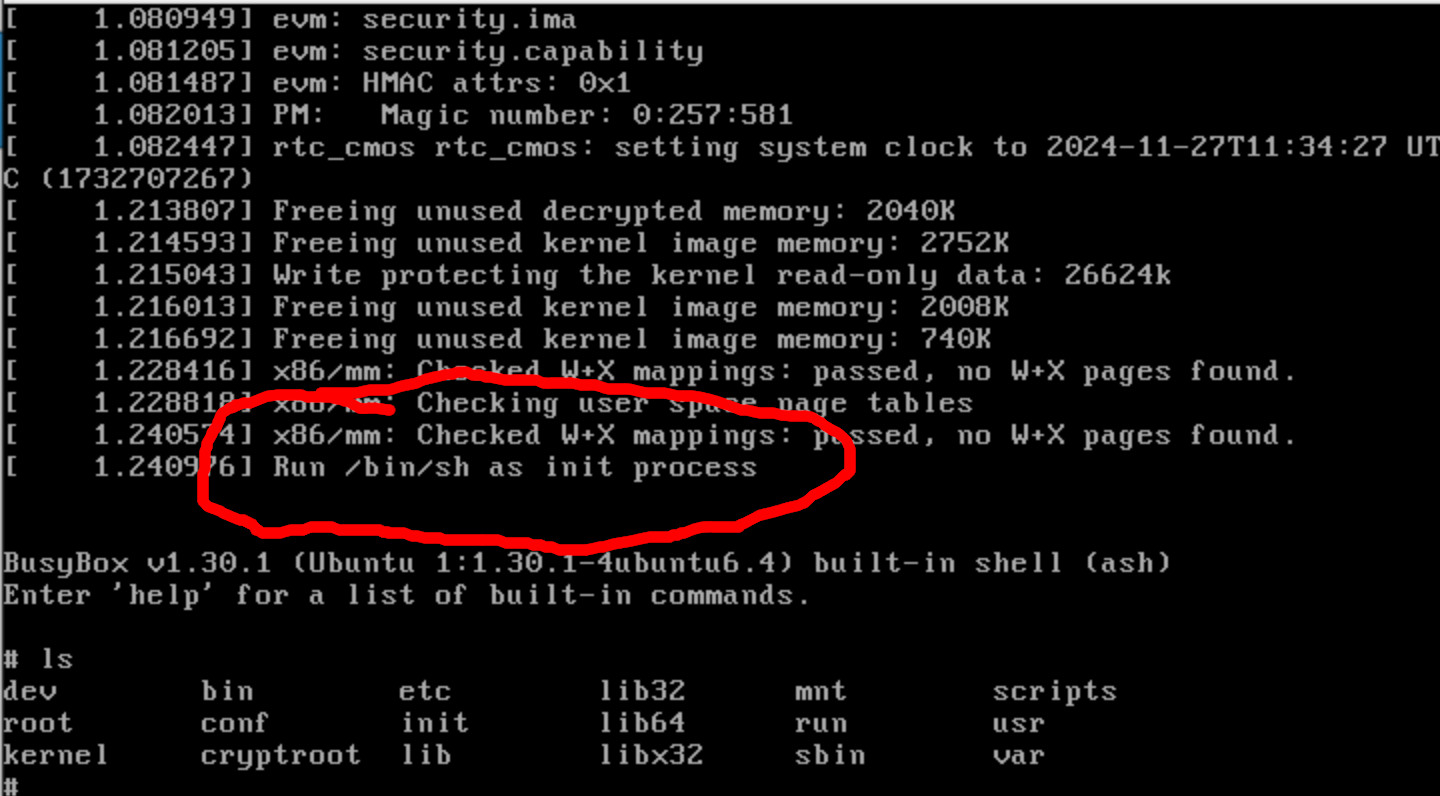
GRUB LUKS Bypass and Dump
Recently, I needed to get the data off of a LUKS encrypted partition on a Virtual […]
