
Russian cyberespionage groups target Signal users with fake group invites
Russian advanced persistent threat (APT) groups are increasingly launching phishing attacks aimed at tricking users of […]
Using Metadata for Incident Response to Strengthen Your Security Strategy
Effective incident response is a top priority for organizations to minimize the impact of cyber threats. […]

How to prevent AI-based data incidents
It’s every company’s nightmare: A competitor is targeting its own customers with targeted campaigns. And it’s […]

Hackers gain root access to Palo Alto firewalls through chained bugs
A high-severity authentication bypass vulnerability in Palo Alto Networks’ PAN-OS software, patched last week, is now […]

Mehrheit der Deutschen fürchtet sich vor Cyberangriffen
Viele Deutsche fürchten sich vor gezielten Cyberangriffen, die von Staaten ausgehen. Andrea Danti – Shutterstock.com Eine […]
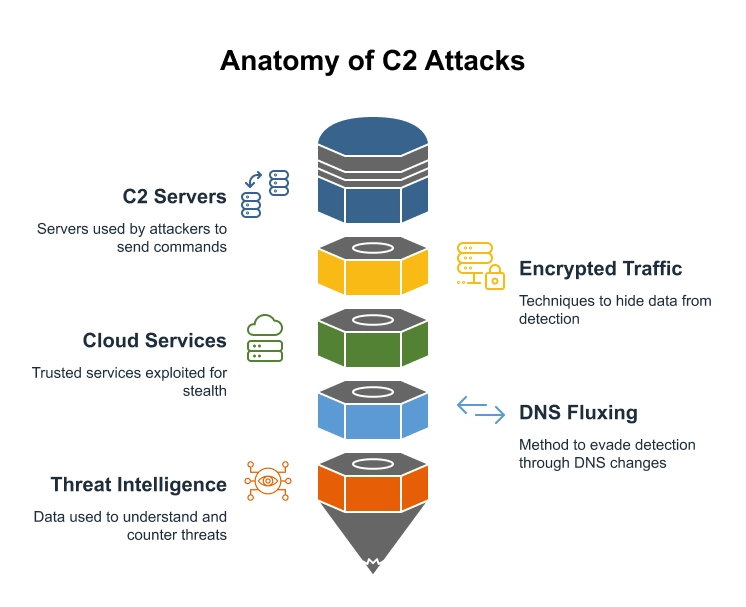
Command and Control Attack Detection: How to Stop Them
To defeat the enemy, you must first disarm their ability to communicate. Command and Control (C2) […]

Think being CISO of a cybersecurity vendor is easy? Think again
When people in this industry hear that a CISO is working at a cybersecurity vendor, it […]

Customer Identity & Access Management: Die besten CIAM-Tools
Wir haben die besten Lösungen in Sachen Customer Identity & Access Management für Sie zusammengestellt. Jackie […]

OpenSSH fixes flaws that enable man-in-the-middle, DoS attacks
OpenSSH, the most widely used tool for remotely managing Linux and BSD systems, received patches for […]
Understanding Content-Based and Context-Based Signatures
In cybersecurity, identifying and neutralizing threats quickly is crucial. IDS solutions play a vital role in […]
