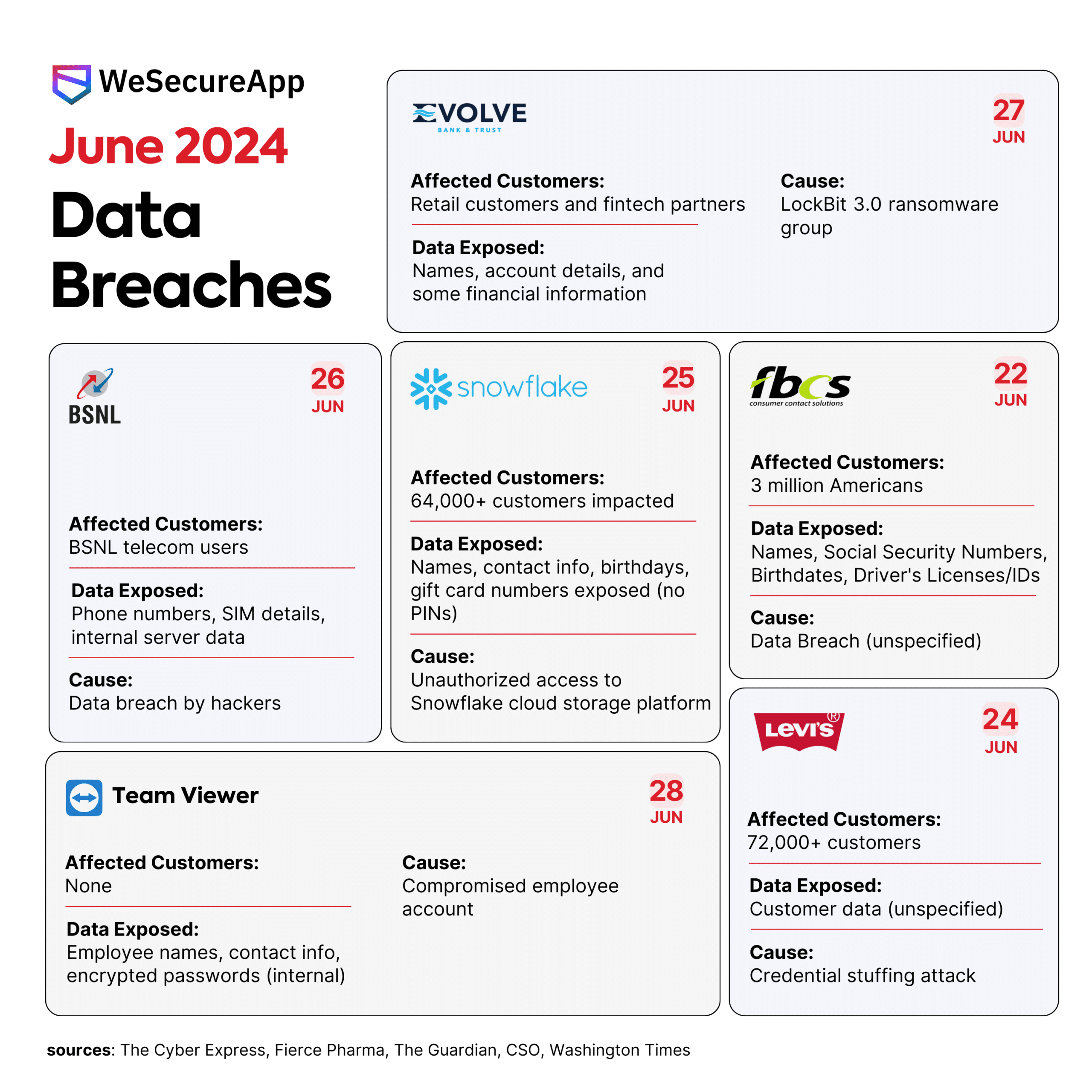
Data Breaches in June 2024 – Infographic
Have you ever gotten that sinking feeling that your personal information might be out in the […]
Data Breaches in June 2024 – Infographic
Have you ever gotten that sinking feeling that your personal information might be out in the […]
The Vital Role of On-Premises Hardware Security Module (HSMs) in Securing Encryption Keys
Encryption stands as a cornerstone for safeguarding sensitive data within any organization. Complying with data privacy […]

How To Scan a Website for Vulnerabilities: Top Tools and Techniques
Knowing how to scan a website for vulnerabilities can help keep you protected in today’s digital […]
CryptoBind HSM is now built with FIPS 140-3 Level 3 Certified Cryptographic Boundary
In the ever-evolving landscape of digital security, staying ahead of the curve is paramount. Today, we […]
Safeguarding Your Digital Assets: The Crucial Role of Enterprise Key Management Systems
In today’s digital age, the landscape of cybersecurity is complex and ever evolving. Protecting sensitive information […]
Mobile SDK Security: Effective Testing Methodology
In mobile penetration testing, third-party modules or libraries are often considered out of scope for several […]
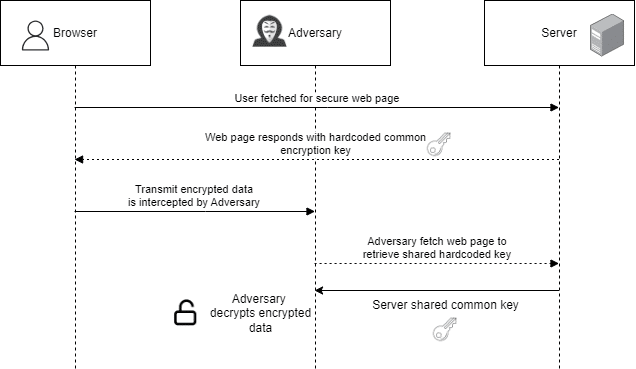
How Poor Cryptographic Practices Endanger Banking Software Security
In today’s digital age, financial institutions rely heavily on encryption to protect sensitive data in their […]
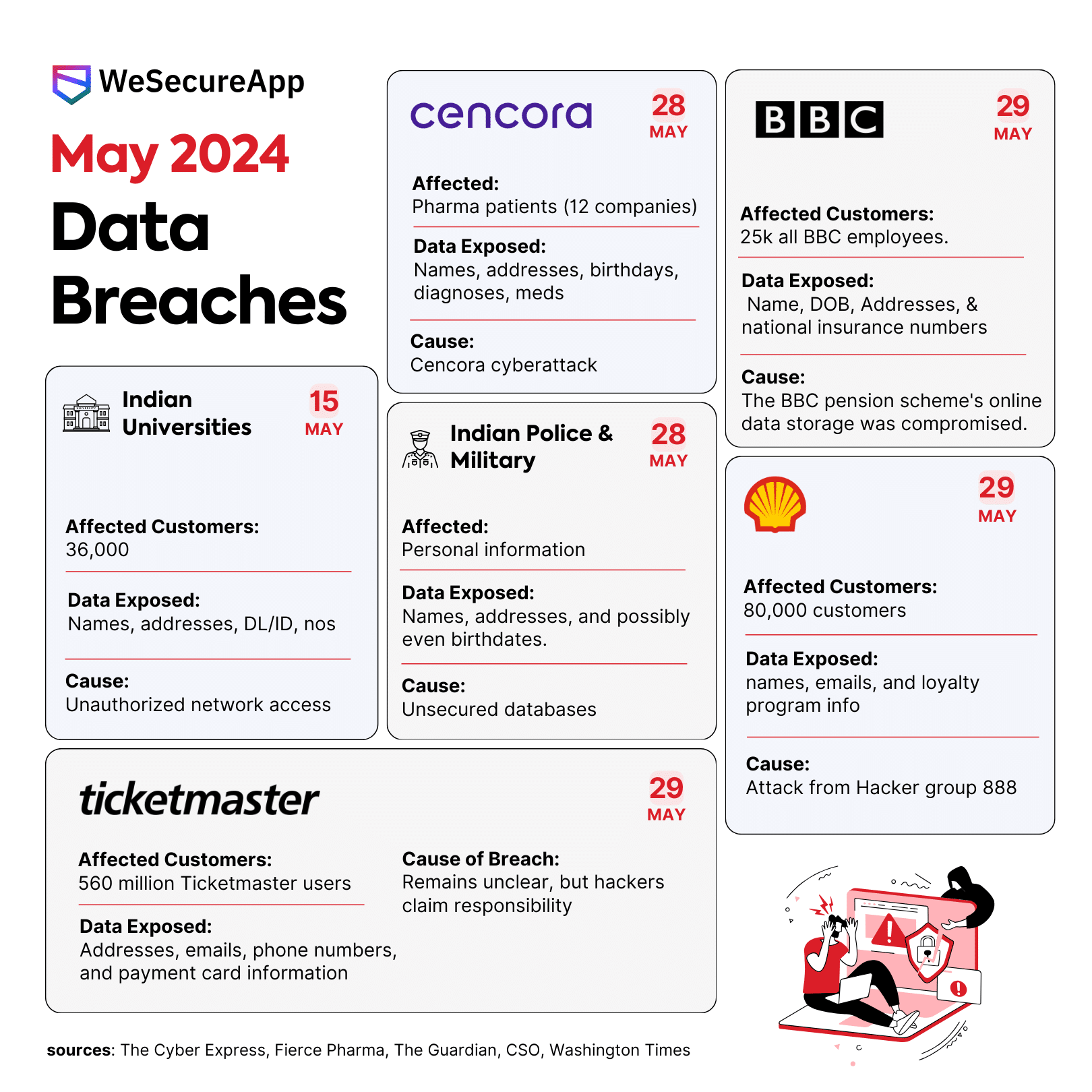
Data Breaches in May 2024 – Infographic
Has your data ever felt…exposed? We’ve all heard about data breaches, but have you ever stopped […]
Forescout CEO Barry Mainz on Operational Technology and Cybersecurity
I spoke with Barry Mainz, CEO of Forescout, about the key trends impacting security in operational […]
