
Complete list of penetration testing and hacking tools
Penetration testing, also known as pen testing, is an integral constituent of cybersecurity. It involves studying […]
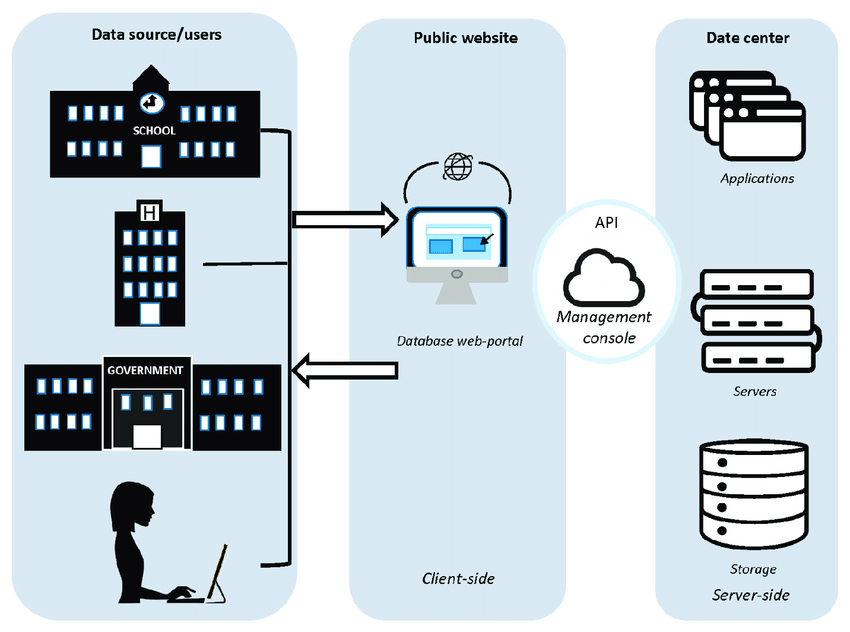
Web Server Side Technology
Server-side technology refers to technology executed by a server in a client-server model. Server-side technology refers […]
Tokenization Solution: Securing Data and Enhancing Privacy
In today’s digital era, protecting sensitive information is paramount. With the increasing number of data breaches […]
How Observability Leads to Better Cybersecurity
The term “observability” refers both to the concept of monitoring, analyzing, and understanding all data moving […]
Cookies vs Sessions Explained: What You Need to Know
Hey there! Welcome to our guide on sessions and cookies. So, what’s the big deal about […]
Creating Custom .onion Addresses for Tor Hidden Services
This article can often contain rather random Tor .onion links. I’ll show you how to create […]

Understanding the Web and HTTP
The web refers to the World Wide Web (commonly used as WWW), a sub-concept of the […]
Red team vs Blue team: A CISO’s Guide to Offensive Security
It’s 3 am. Your phone screams. Hackers are in your system. Panic sets in. But wait! […]
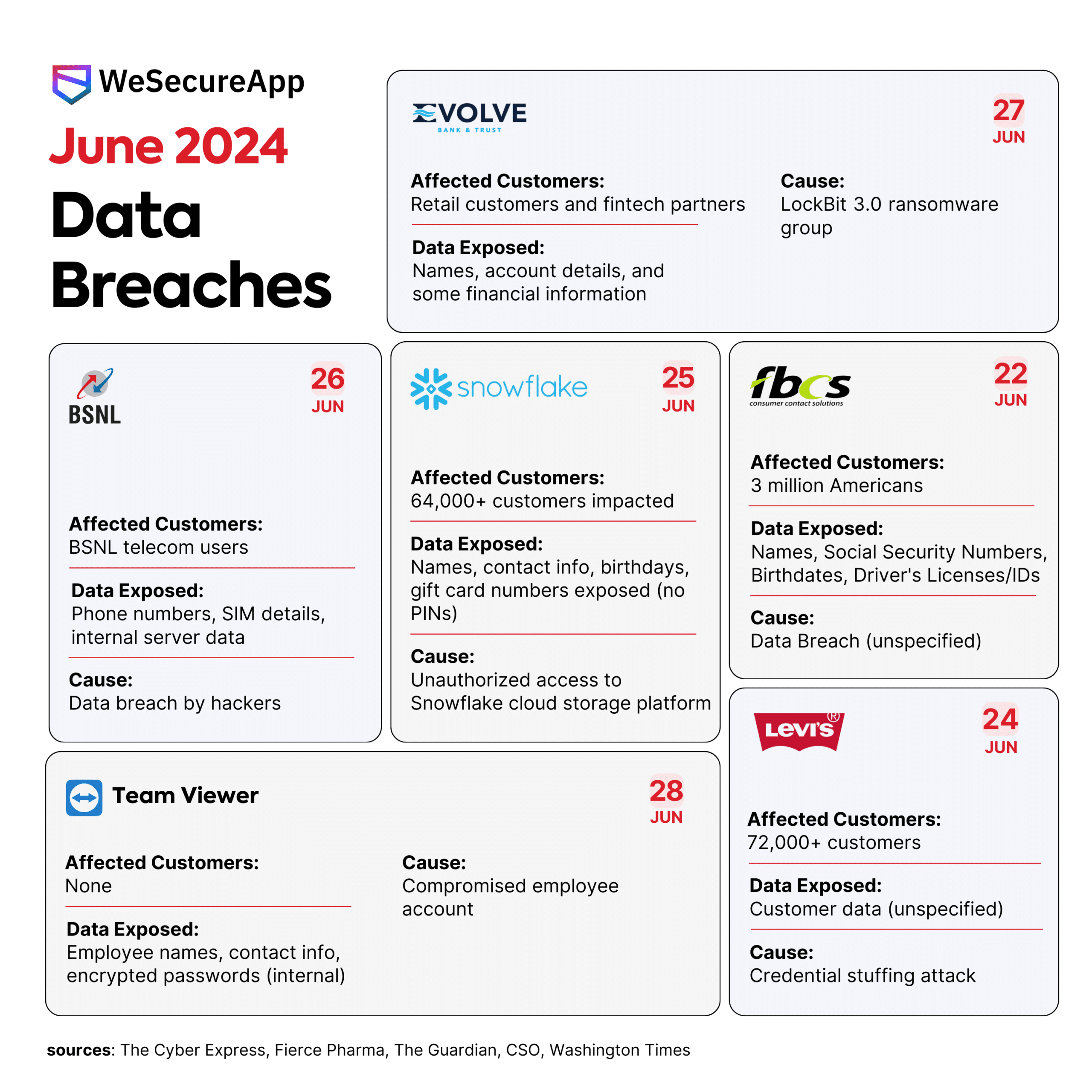
Data Breaches in June 2024 – Infographic
Have you ever gotten that sinking feeling that your personal information might be out in the […]
Data Breaches in June 2024 – Infographic
Have you ever gotten that sinking feeling that your personal information might be out in the […]
