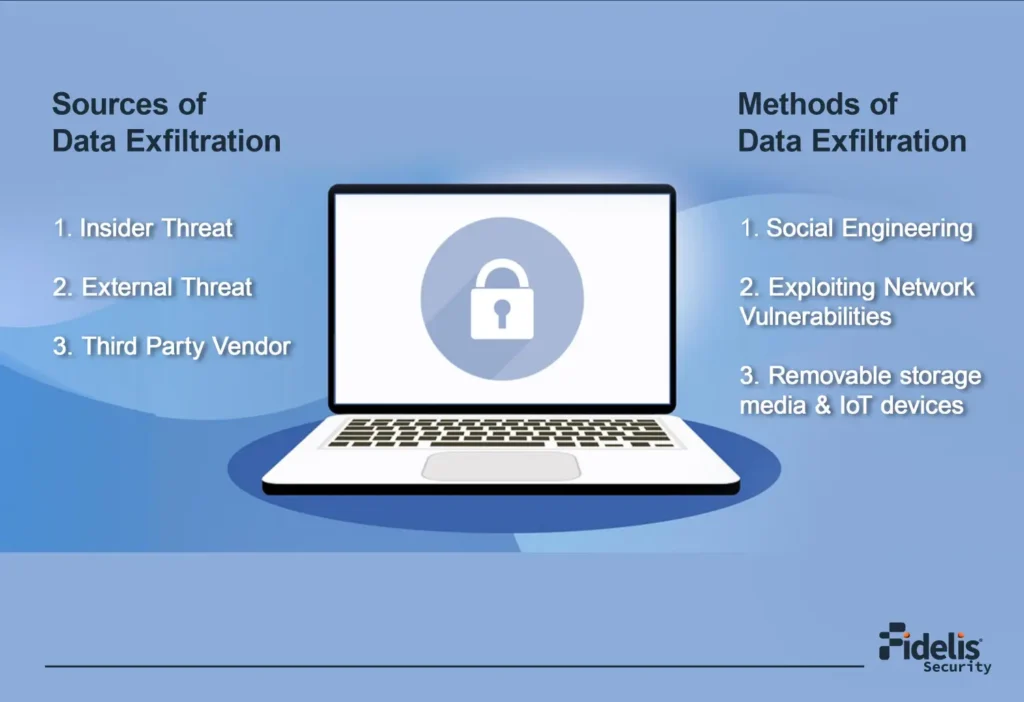
How to Prevent Data Exfiltration
What is Data Exfiltration? When someone steals important information, usually with the intent of misusing it, […]

Want to know how the bad guys attack AI systems? MITRE’S ATLAS can show you
It’s one thing to understand that artificial intelligence introduces new and rapidly evolving threats, but it’s […]

What is pretexting? Definition, examples, and attacks
Pretexting definition Pretextingis form of social engineering in which an attacker fabricates a story to convince a victim […]
Reveal of Chinese-controlled botnet is another warning to CISOs to keep up with asset and patch management
A Chinese-controlled botnet of tens of thousands of unpatched internet-connected firewalls, network attached storage devices, internet-connected […]

Need better network performance? Adopt better secure networking strategies
Many organizations consider digital acceleration a key initiative because those in the C-Suite and IT leadership […]

Microsoft warns of ransomware attacks on US healthcare
Ransomware group Vanilla Tempest is targeting US healthcare providers using the INC ransomware service, according to […]

Companies skip security hardening in rush to adopt AI
Security analysis of assets hosted on major cloud providers’ infrastructure shows that many companies are opening […]

Deepfakes break through as business threat
Deepfakes targeting enterprise financial data used to be a hypothetical concern, but that’s no longer the […]
Active Directory Hardening: Best Practices and Checklist
As cyber threats continue to be more sophisticated, the need for active directory security becomes paramount. […]
Automate Everything With Python and Bash
Hey there! You ever think about how amazing it would be to just automate your life […]
