
Malware attack on State Data Center in India puts some citizen services at a standstill
India’s hill state of Uttarakhand’s entire IT infrastructure came to a standstill on Friday after malware […]

Chief risk storyteller: How CISOs are developing yet another skill
Mastering the art of risk storytelling is essential for CISOs not just for engagement, but for […]

How ‘perfctl’ malware infected Linux servers undetected for years
Security researchers warn that a malware campaign dubbed perfctl has targeted millions of Linux servers over […]

How ‘perfctl’ malware infected millions of Linux servers undetected for years
Security researchers warn that a malware campaign dubbed perfctl has infected millions of Linux servers over […]

🛠️ Essential Resources to Start Your Hacking Journey
Hey there, future hacker! 🎩 You want to get your feet wet in the exciting world […]

Hackers steal sensitive customer data from thousands of online stores that use Adobe tools
Distinct groups of cybercriminals have been exploiting the CosmicSting flaw in Adobe’s Commerce and Magento software […]

DOJ seizes 41 Russian-controlled domains in cyber-espionage crackdown
The US Department of Justice (DOJ) has seized 41 internet domains used by Russian intelligence agents […]
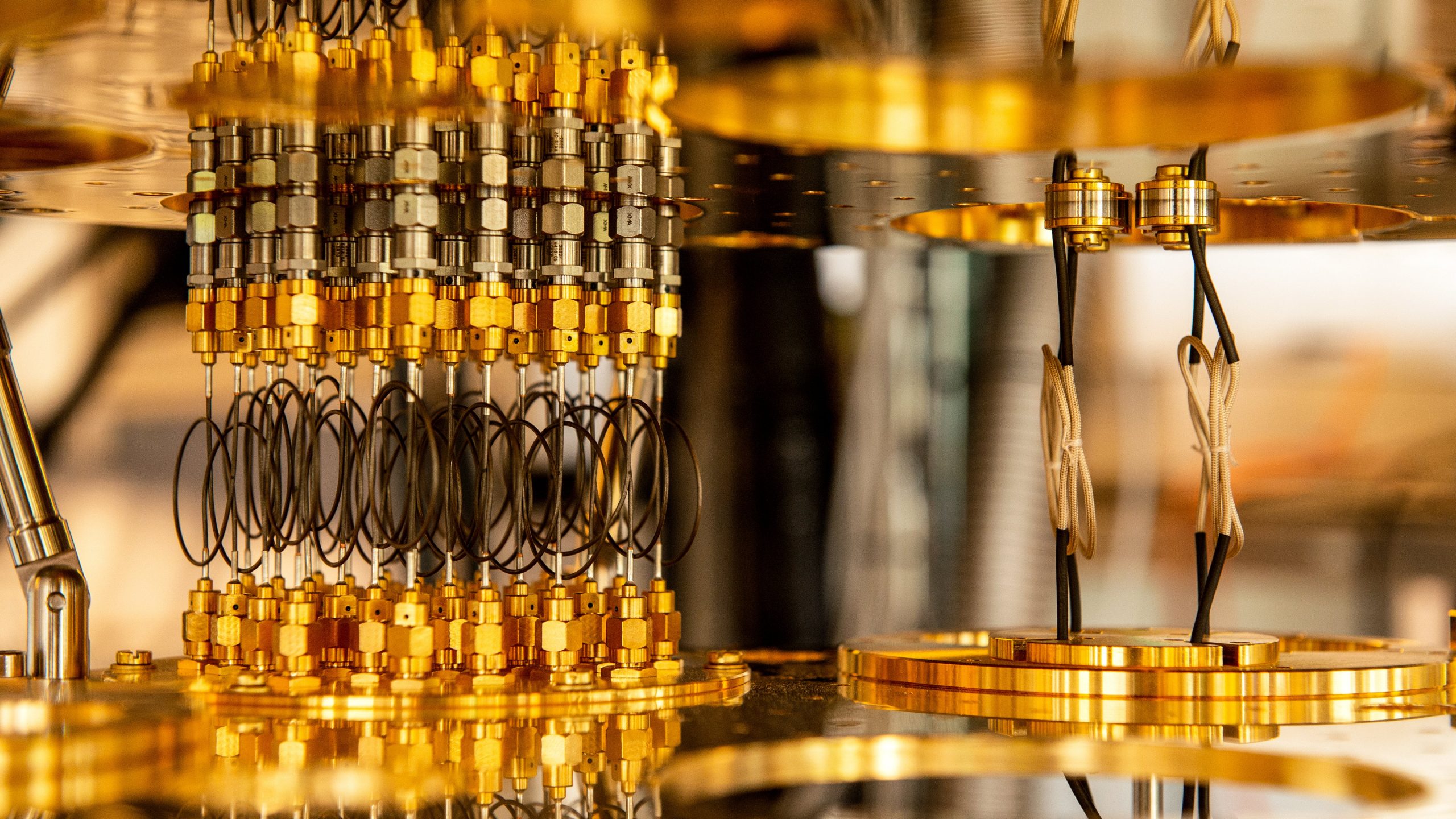
Notable post-quantum cryptography initiatives paving the way toward Q-Day
The point at which quantum computers will be capable of breaking existing cryptographic algorithms — known […]

Nordkoreanische Cyberspione ködern Entwickler
Nordkoreanische Hacker werden immer kreativer, wenn es darum geht, Daten zu ergaunern FOTOGRIN – shutterstock.com Softwareentwickler […]

Over 80% of phishing sites now target mobile devices
Mobile-targeted phishing (M-ishing) attacks are seeing a significant rise with more than four out of every […]
