
How the Marine Corps slashed IT delays by shifting to DevOps and agile development
The U.S. Marine Corps is celebrated for its precision and ability to adapt on the battlefield. […]

Razzia gegen Darknet-Drogenversand
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2008599362.jpg?quality=50&strip=all 4904w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2008599362.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2008599362.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2008599362.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2008599362.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2008599362.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2008599362.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2008599362.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

Neues Phishing-Framework stiehlt Login-Daten von Microsoft und Google
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2142206135.jpg?quality=50&strip=all 9147w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2142206135.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2142206135.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2142206135.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2142206135.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2142206135.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2142206135.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/09/shutterstock_2142206135.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

Scattered Spider’s ‘retirement’ announcement: genuine exit or elaborate smokescreen?
Nearly 15 ransomware and cybercrime groups, led by the notorious Scattered Spider collective, announced their retirement […]

New ransomware Yurei adopts open-source tools for double-extortion campaigns
A new ransomware group called Yurei has surfaced, adopting a double-extortion model. The group encrypts the […]

Samsung’s image library flaw opens a zero-click backdoor
Samsung has disclosed a serious vulnerability affecting a core utility within its Android devices, one that […]
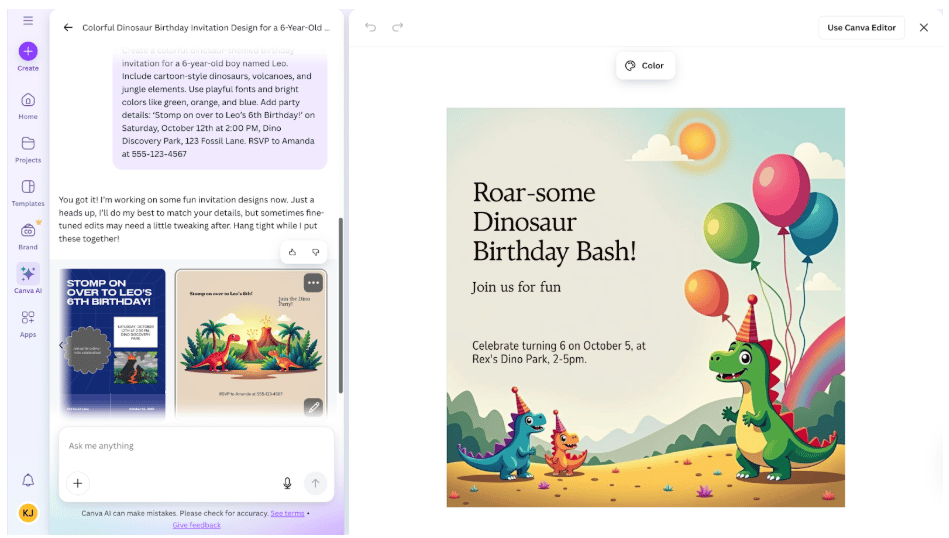
Best AI Tools for Party Planning
Throwing a party sounds fun, but often, you find yourself drowning in theme ideas, endless guest […]

Your SOC is the parachute — Will it open?
The security economy revolves around the assumption that security operations centres (SOCs) will save organizations. Spend […]
What augmented intelligence really means for fintech leaders
Artificial Intelligence (AI) has been the buzzword in the fintech industry more than ten years now. […]

5 trends reshaping IT security strategies today
Cybersecurity’s core mission remains the same: Defend the organization from all the dangers that lurk in […]
