
Malicious actors increasingly put privileged identity access to work across attack chains
Abuse of legitimate privileged access is on the rise, accounting for the majority of security breaches […]

Oracle Health warnt vor Datenleck
width=”2432″ height=”1368″ sizes=”(max-width: 2432px) 100vw, 2432px”>Hacker haben sich Zugriff auf Daten von Oracle Health verschafft. Pincasso […]

Microsoft takes first step toward passwordless future
Microsoft is looking to permanently abandon password-based user authentication, replacing it with a system that uses […]

10 best practices for vulnerability management according to CISOs
It was 2003, and I was giving my first cybersecurity presentation at an industry conference in […]
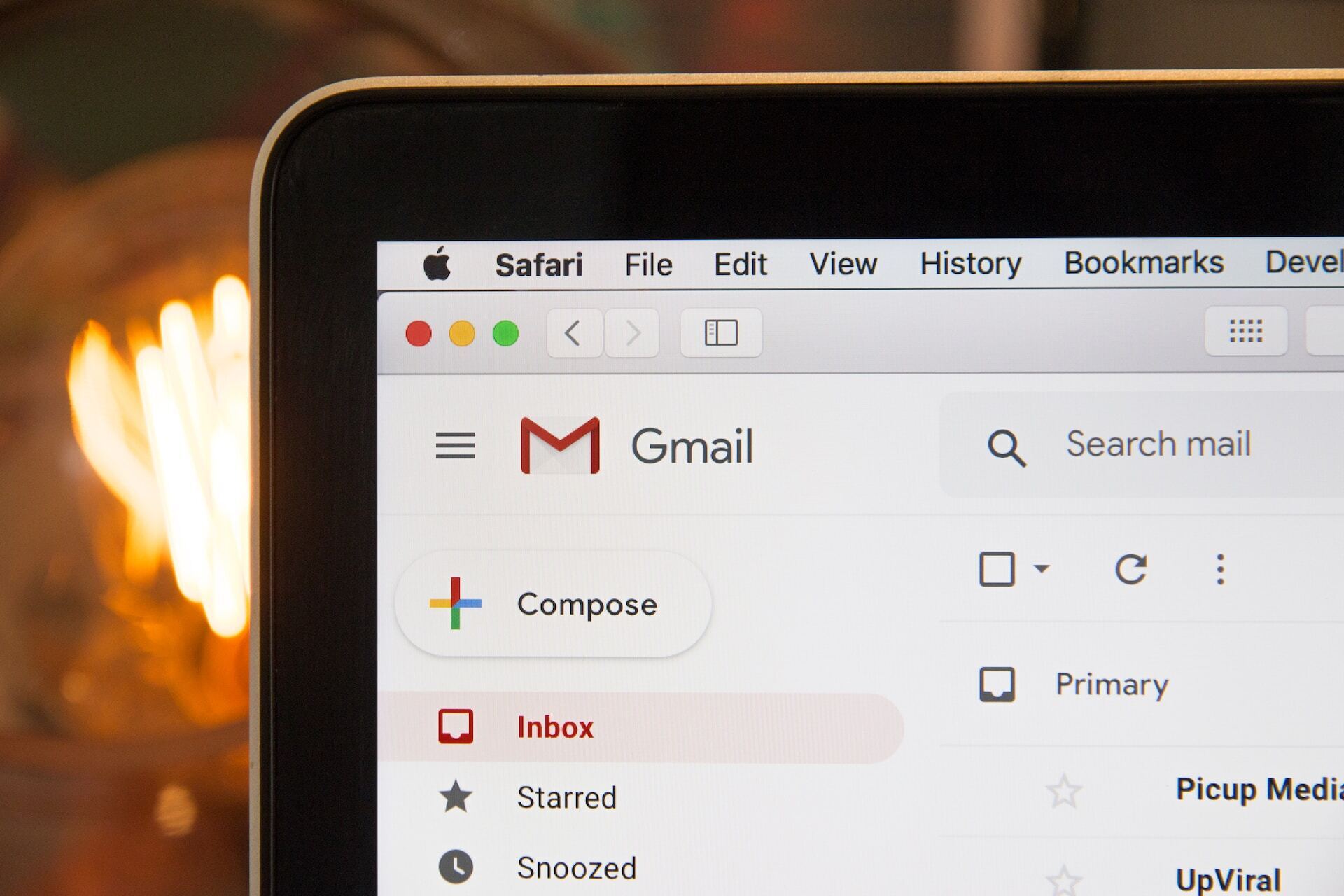
Google adds end-to-end email encryption to Gmail
Google has introduced a new end-to-end encryption (E2EE) feature in Gmail, enabling organizations to send encrypted […]

The UK’s Cyber Security and Resilience Bill will boost standards – and increase costs
If you’re a UK enterprise, this might not be good news: extra investment by infrastructure providers […]

The urgent reality of machine identity security in 2025
The importance of machine identity security has reached a critical juncture in 2025. With machine identities now far […]

How CISOs can use identity to advance zero trust
AI is the best thing that’s ever happened to cybercriminals. It allows them to weaponize trust […]

Download the Strategizing Data Analytics for AI Enterprise Spotlight
Download the April 2025 issue of the Enterprise Spotlight from the editors of CIO, Computerworld, CSO, […]

Altgeräte bedrohen Sicherheit in Unternehmen
width=”2500″ height=”1406″ sizes=”(max-width: 2500px) 100vw, 2500px”>Schwachstellen in alten Netzwerkgeräten stellen ein erhebliches Sicherheitsrisiko für Unternehmen dar. […]
