
Spy vs spy: Security agencies help secure the network edge
The national intelligence services of five countries have offered enterprises advice on beating spies at their […]
Malicious package found in the Go ecosystem
A malicious typosquat package has been found in the Go language ecosystem. The package, which contains a backdoor […]

Ransomware-Angriff auf Escada
Der Modehersteller Escada wird von einer Ransomware-Bande mit gestohlenen Daten erpresst. Indoor Vision – Shutterstock Die […]

Lazarus Group tricks job seekers on LinkedIn with crypto-stealer
North Korea-linked Lazarus Group is duping job seekers and professionals in an ongoing campaign that runs […]
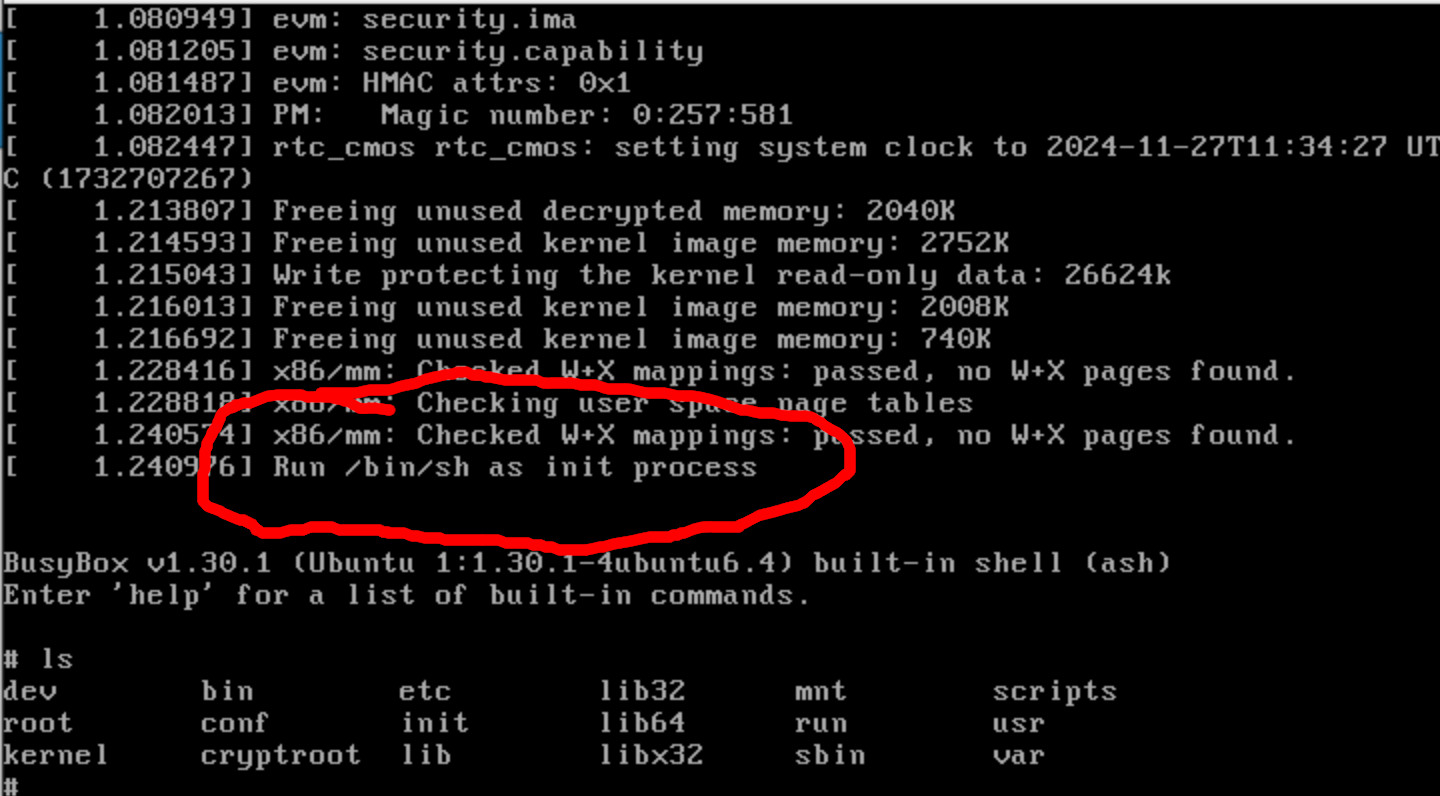
GRUB LUKS Bypass and Dump
Recently, I needed to get the data off of a LUKS encrypted partition on a Virtual […]

GRUB LUKS Bypass and Dump
Recently, I needed to get the data off of a LUKS encrypted partition on a Virtual […]
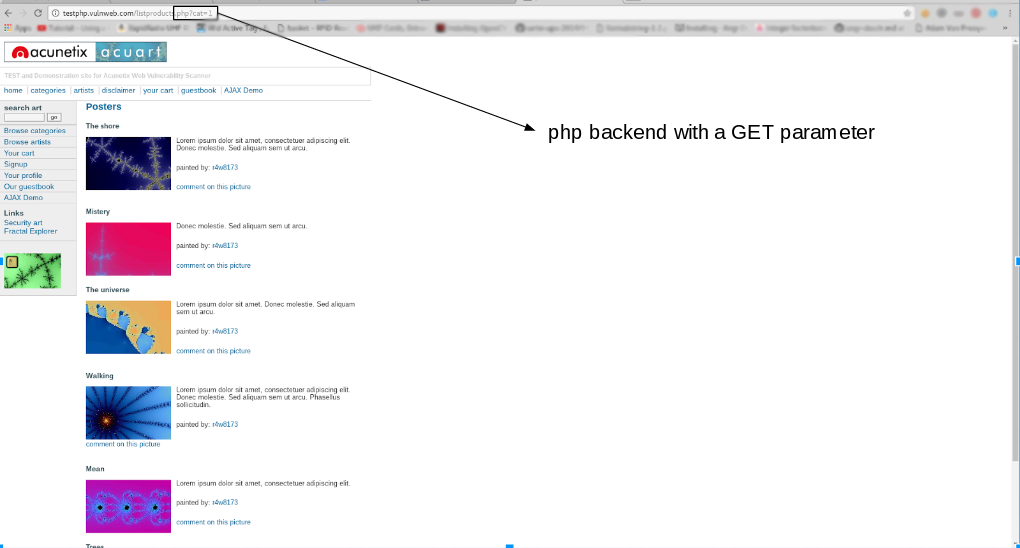
Unleashing the Power of SQL Injection Testing with SQLMap : A Comprehensive Guide
Sqlmap is a Python-based tool, which means it will usually run on any system with Python. […]

Unleashing the Power of SQL Injection Testing with SQLMap : A Comprehensive Guide
Sqlmap is a Python-based tool, which means it will usually run on any system with Python. […]

21% of CISOs pressured to not report compliance issues
CISOs are increasingly getting caught between business pressures and regulatory obligations, leaving them struggling to balance […]

The cloud is not your only option: on-prem security still alive and well in Windows Server 2025
We’ve often heard that on-premises solutions are on their way out, but until it’s clear that […]
