
Understanding OWASP’s Top 10 list of non-human identity critical risks
Verizon There are some very good reasons why non-human identities (NHI) have landed among the most-discussed […]

What is SIEM? Improving security posture through event log data
Introduction to SIEM Security information and event management software (SIEM) products have been an enduring part […]

Der trügerische Komfort des Risikomanagements
Gefahrenmanagement statt Risikomanagement: Cybersicherheit erfordert Dringlichkeit und Entschlossenheit. Billion Photos – Shutterstock.com Herkömmliches Risikomanagement basiert auf […]

CISO success story: Predicting cyber risk (accurately) is easier with this guy’s formula
You wouldn’t expect a professional jazz musician to morph into a cybersecurity policy expert, but that’s […]

Russian cyberespionage groups target Signal users with fake group invites
Russian advanced persistent threat (APT) groups are increasingly launching phishing attacks aimed at tricking users of […]
Using Metadata for Incident Response to Strengthen Your Security Strategy
Effective incident response is a top priority for organizations to minimize the impact of cyber threats. […]

How to prevent AI-based data incidents
It’s every company’s nightmare: A competitor is targeting its own customers with targeted campaigns. And it’s […]

Hackers gain root access to Palo Alto firewalls through chained bugs
A high-severity authentication bypass vulnerability in Palo Alto Networks’ PAN-OS software, patched last week, is now […]

Mehrheit der Deutschen fürchtet sich vor Cyberangriffen
Viele Deutsche fürchten sich vor gezielten Cyberangriffen, die von Staaten ausgehen. Andrea Danti – Shutterstock.com Eine […]
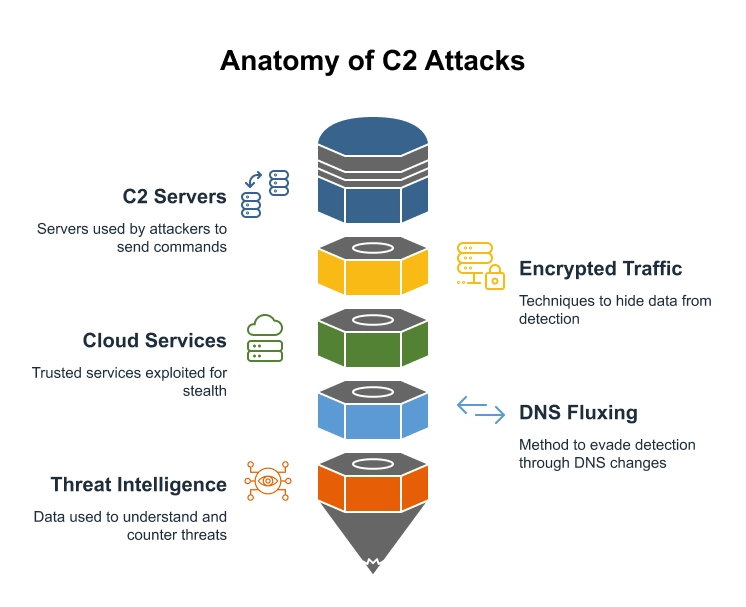
Command and Control Attack Detection: How to Stop Them
To defeat the enemy, you must first disarm their ability to communicate. Command and Control (C2) […]
