
6 novel ways to use AI in cybersecurity
AI is already widely recognized as a powerful cybersecurity protection tool. AI-driven systems can detect threats […]
Why Tokenization is the Future of Data Security
In a world where information is the currency, its security has become the foundation of faith, […]
UIDAI 2025 Guidelines: Ensuring Aadhaar Data Compliance
The Aadhaar system has always been the hallmark of secure citizen authentication in the realm of […]

Das gehört in Ihr Security-Toolset
Lesen Sie, welche Werkzeuge essenziell sind, um Unternehmen gegen Cybergefahren abzusichern. Gorodenkoff | shutterstock.com Sicherheitsentscheider sind […]
Google’s Head of AI Studio Builds Apps in Under a Minute – Here’s How
Logan Kilpatrick, who leads AI Studio and Gemini API at Google DeepMind, revealed something wild when […]

Ex-lobbyist for Meta becomes Irish data protection commissioner
The Irish government has appointed Niamh Sweeney as a new member of the Data Protection Commission (DPC), the […]

AI-powered phishing scams now use fake captcha pages to evade detection
In an attempt to evade security tools, cybercriminals are now leveraging AI to craft sophisticated phishing […]

European airports continue to crawl after a cyberattack on Collins’ MUSE systems
A cyberattack that began late Friday on an airline service provider in Europe has caused widespread […]
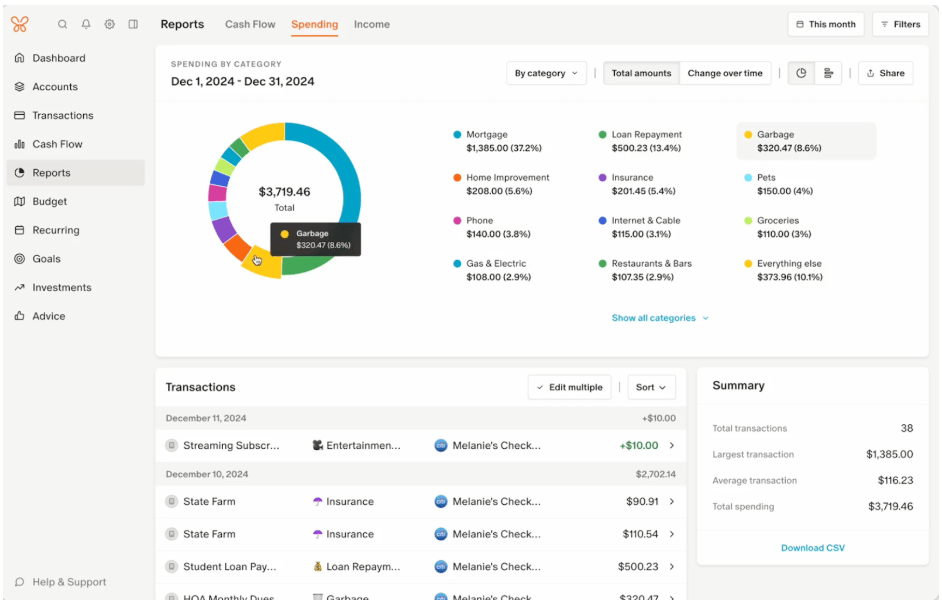
Best AI Tools for Personal Finance
If you ever feel like your budgeting tasks never end, AI tools for personal finance can […]
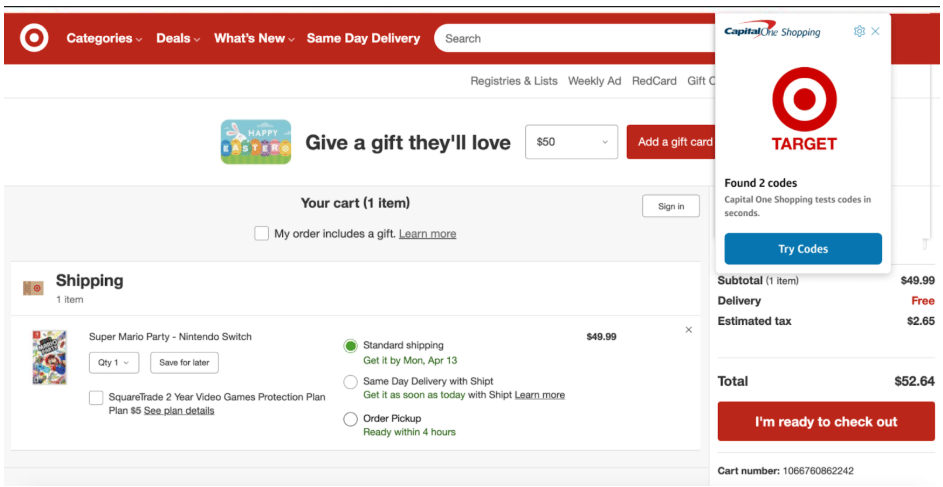
Best AI Shopping Assistants to Save Money
Shopping smarter is no longer about clipping coupons or waiting for Black Friday sales; AI shopping […]
