Musk Names Ex-Morgan Stanley Banker as xAI CFO
Elon Musk has tapped former Morgan Stanley banker Anthony Armstrong as the new CFO of his […]

Autonomous AI hacking and the future of cybersecurity
AI agents are now hacking computers. They’re getting better at all phases of cyberattacks, faster than […]
The Road Ahead: India’s Data Protection in 2026
Data is now being used as a strategic asset and a major vulnerability as global businesses […]
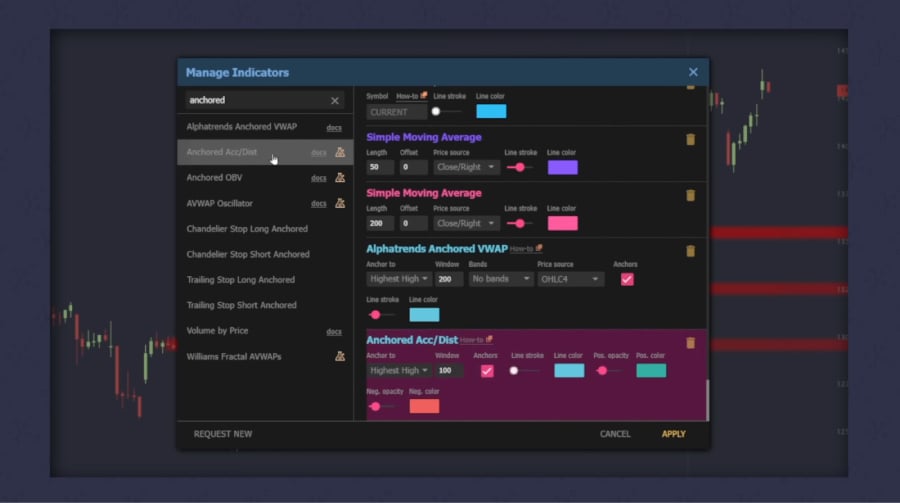
Best AI Tools for Tracking Stocks
Keeping up with the stock market is no simple task. It can be overwhelming as prices […]

10.0-severity RCE flaw puts 60,000 Redis instances at risk
The popular Redis in-memory data store received a patch for a critical vulnerability that leads to […]

Cybersecurity in Banking: Challenges in 2025—and How to Overcome Them
Why $16 Trillion in Bank Assets Became Cybercriminals’ Ultimate Prize Banking executives managing $16 trillion across […]
MrBeast Warns of ‘Scary Times’ as AI Threatens YouTube Creators
YouTube’s biggest star, MrBeast, is raising a red flag about the future of online video creation. […]
Report: 78% of ICT Job Postings in G7 Countries Expect AI Skills
If you work in the information and communications technology (ICT) industry or you want to, mastering […]

it-sa 2025: Fast 1.000 Security-Anbieter am Start
Weggefährten der it-sa auf der ersten Pressekonferenz (von links): Claudia Plattner, BSI-Präsidentin, Ralf Wintergerst, Präsident des […]
1 in 5 US Workers Now Use AI on the Job, Pew Research Finds
A new survey from the Pew Research Center shows that AI is gradually becoming part of […]
