
Give Me 5 Minutes and I’ll Fix Your Bug Bounty Strategy (The 2026 Blueprint)
Let’s be real. You’re putting in the hours. You’ve got your tools set up, you’re scoping […]

From feeds to flows: Using a unified linkage model to operationalize threat intelligence
The problem: Static intelligence in a dynamic world Every CISO knows the fatigue that comes with […]

Windows shortcuts’ use as a vector for malware may be cut short
A longstanding problem with the way Windows handles LNK shortcut files, which attackers have been abusing […]

Momberger: Betrug-E-Mails an Kunden im Umlauf
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?quality=50&strip=all 5150w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=150%2C84&quality=50&strip=all 150w, […]
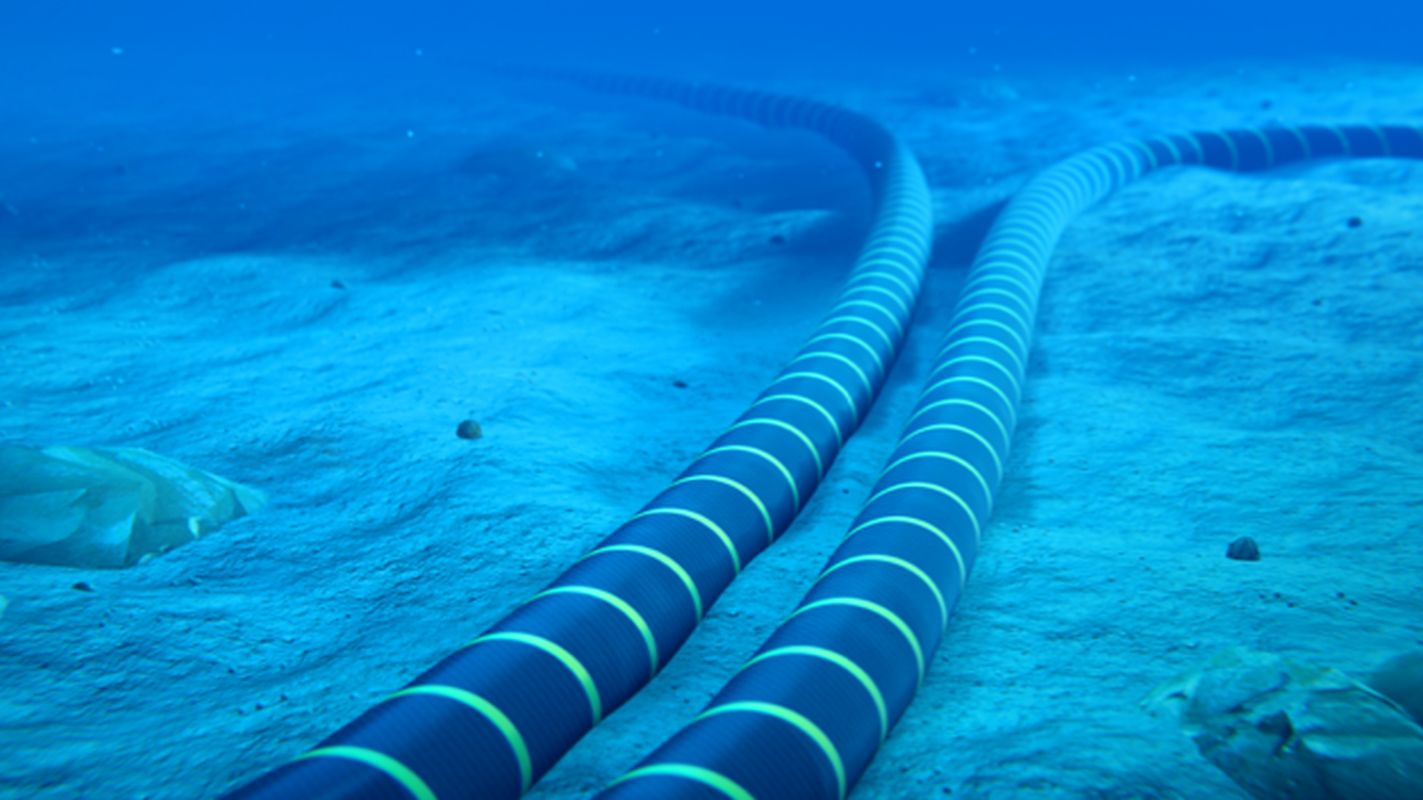
Submarine cable cybersecurity: protecting critical infrastructure
Between 95 and 99% of the world’s data traffic travels through submarine cables. An extensive network […]

Coach or mentor: What you need depends on where you are as a cyber leader
Renee Guttmann, a Fortune 50 CISO who has served at Time Warner, Coca-Cola, Royal Caribbean Cruises, […]

Wie Unternehmen sich gegen neue KI-Gefahren wappnen
KI ist nicht nur ein Tool für Hacker, sondern kann auch selbst zur Gefahr werden. inray27 […]

Developers urged to immediately upgrade React, Next.js
Developers using the React 19 library for building application interfaces are urged to immediately upgrade to […]

RCE flaw in OpenAI’s Codex CLI highlights new risks to dev environments
In a new example of how AI tools expand the attack surface of development machines, researchers […]

Hybrid 2FA phishing kits are making attacks harder to detect
Some 2FA-phishing attacks are becoming significantly harder to spot as threat actors blend two previously distinct […]
