
PoisonSeed outsmarts FIDO keys without touching them
PoisonSeed, the notorious crypto-hacking attack group known for large-scale phishing campaigns, was seen cracking Fast Identity […]

Microsoft SharePoint zero-day breach hits on-prem servers
Attackers are exploiting a previously unknown vulnerability in Microsoft SharePoint Server, with security researchers confirming dozens […]

Klöckner warnt vor Cyberangriffen auf Bundestag
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/07/shutterstock_2637171389.jpg?quality=50&strip=all 3490w, https://b2b-contenthub.com/wp-content/uploads/2025/07/shutterstock_2637171389.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/07/shutterstock_2637171389.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/07/shutterstock_2637171389.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/07/shutterstock_2637171389.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/07/shutterstock_2637171389.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/07/shutterstock_2637171389.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/07/shutterstock_2637171389.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

MAD warnt vor russischer Spionage
Der Militärische Abschirmdienst (MAD) verzeichnet deutlich verstärkte Ausspähversuche und Störmaßnahmen russischer Geheimdienste in Deutschland. FamVeld – […]

From hardcoded credentials to auth gone wrong: Old bugs continue to break modern systems
At a time when AI-powered cyber threats and sophisticated state-backed hacking groups dominate the headlines, the […]

Hacker greifen über Microsoft-Lücke an
Über eine Sicherheitslücke in SharePoint haben Hacker zahlreiche Behörden und Unternehmen angegriffen. T. Schneider – Shutterstock.com […]
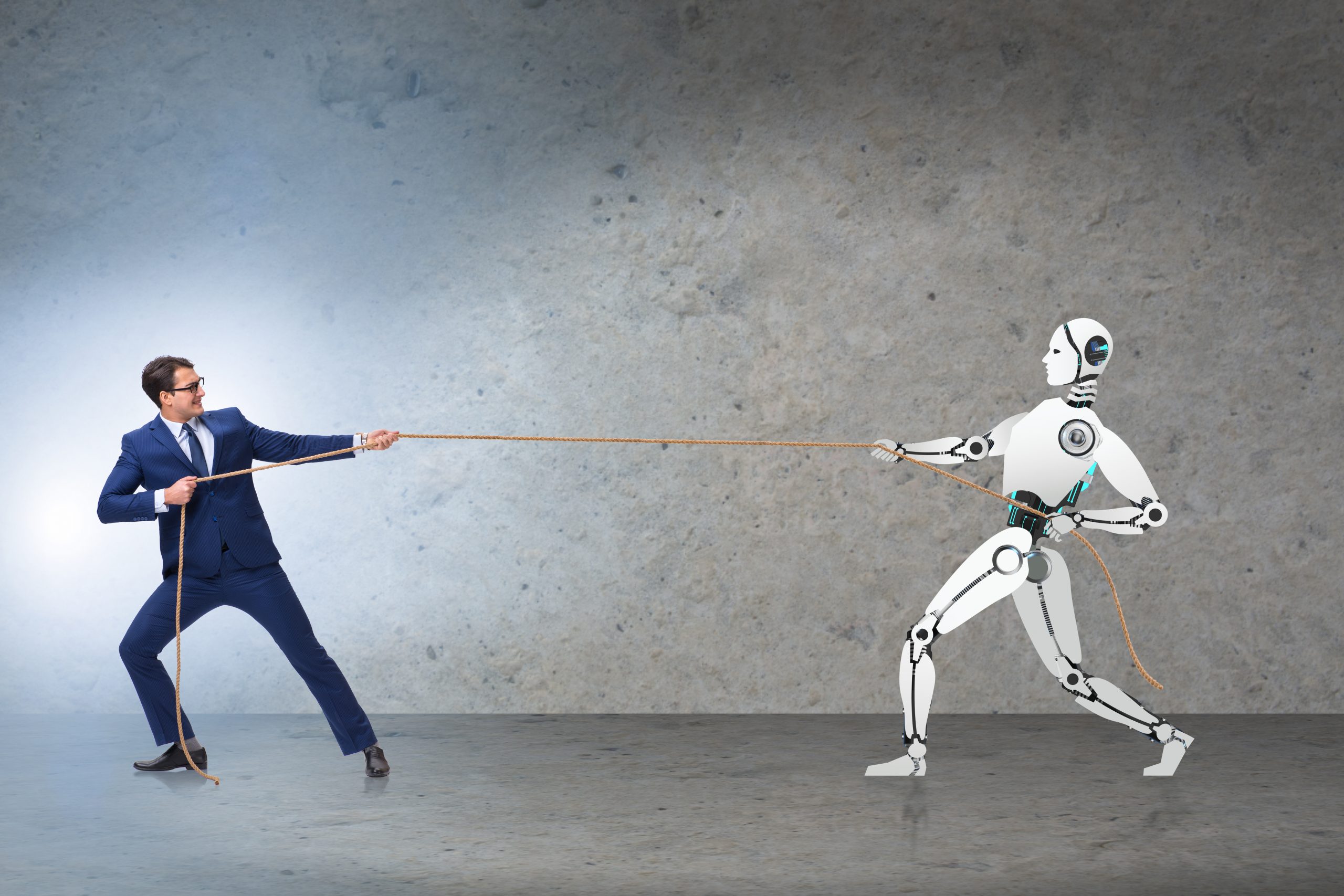
Is AI here to take or redefine your cybersecurity role?
“AI is coming, and will take some jobs, but no need to worry.” That headline ran […]

So geht Tabletop Exercise
Übung macht den Incident-Response-Meister. Foto: GaudiLab – shutterstock.com Die Bedrohungslage entschärft sich bekanntermaßen nie – umso […]

Threat actors scanning for apps incorporating vulnerable Spring Boot tool
Enterprise admins who haven’t yet mitigated a two-month-old vulnerability in apps that incorporate the open source […]

Novel malware from Russia’s APT28 prompts LLMs to create malicious Windows commands
Russian cyberespionage group APT28 has developed malware that generates commands by querying large language models (LLMs). […]
