
NIS2 und der Mittelstand: Zwischen Pflicht und Praxis
NIS2 kommt: Die EU-Richtlinie ist seit 2023 in Kraft und soll europaweite Standards für IT-Sicherheit und […]

Shadow AI is surging — getting AI adoption right is your best defense
AI adoption in the enterprise is no longer theoretical. It is already happening, whether organizations are […]

Behind the Coinbase breach: Bribery emerges as enterprise threat
On May 11, cryptocurrency exchange giant Coinbase “received an email communication from an unknown threat actor […]

Das kostet ein Data Breach 2025
width=”2028″ height=”1141″ sizes=”auto, (max-width: 2028px) 100vw, 2028px”>Laut einer aktuellen Studie liegen die durchschnittlichen Kosten einer Datenpanne […]
The Death of Perimeter Security: Why Firewalls Are the Fax Machines of 2025
As we step in 2025, once the major firewalls that define network safety for decades, now […]

Warum das SOC in der Krise steckt – und wie Sie das ändern
669226129 Gorodenkoff | shutterstock.com Trotz Millioneninvestitionen in Security Operations Center (SOCs) und modernsten Detection-Technologien sind Breaches […]

What Is Your Digital Footprint Revealing to Attackers—and How Can You Turn It into a Defense?
Your online presence—social media posts, web registrations, breach data—creates a digital footprint that attackers can study […]

Munich Reinsurance unites global security teams to boost resilience, cut costs
When an insurer takes on big risks—whether it’s covering homes, cars, or health care—it often turns […]
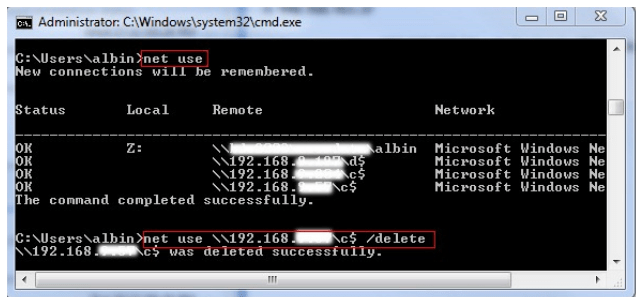
Hunt Evil Your Practical Guide to Threat Hunting – Part 2
As we discussed in the Part 1 , adversaries will come in many forms and will […]

2025 CSO Hall of Fame: Meg Anderson on AI, strategic security investments, and life after InfoSec
Meg Anderson has spent nearly two decades leading enterprise cybersecurity, most recently as vice president and […]
