
Schadenersatz nach Datendiebstahl bei Facebook?
Begründet der Verlust der Kontrolle über Daten einen immateriellen Schaden und wie dieser zu bemessen? TY […]

7 reasons security breach sources remain unknown
One-third of companies still don’t know what caused their data security incidents over the past year, […]

UAB CIO Gonçal Badenes on ransomware lessons learned
“Although it happened two and a half years ago, it still generates anxiety and restlessness to […]
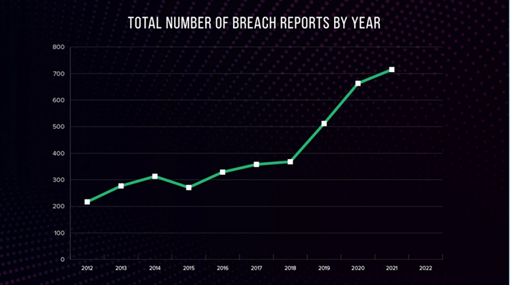
Why a Cyber-healthy Network is Essential for Patient Safety?
The healthcare industry increasingly (and heavily) relies on technology to deliver care and manage patients, employees, […]
5 Myths About Tokenization: Debunking Common Misunderstandings
Tokenization is a powerful strategy in the realm of data security, where sensitive information is replaced […]

Androxgh0st botnet integrates Mozi payloads to target IoT devices
Androxgh0st, a botnet known to steal cloud credentials and exploit vulnerabilities in web frameworks and servers, […]
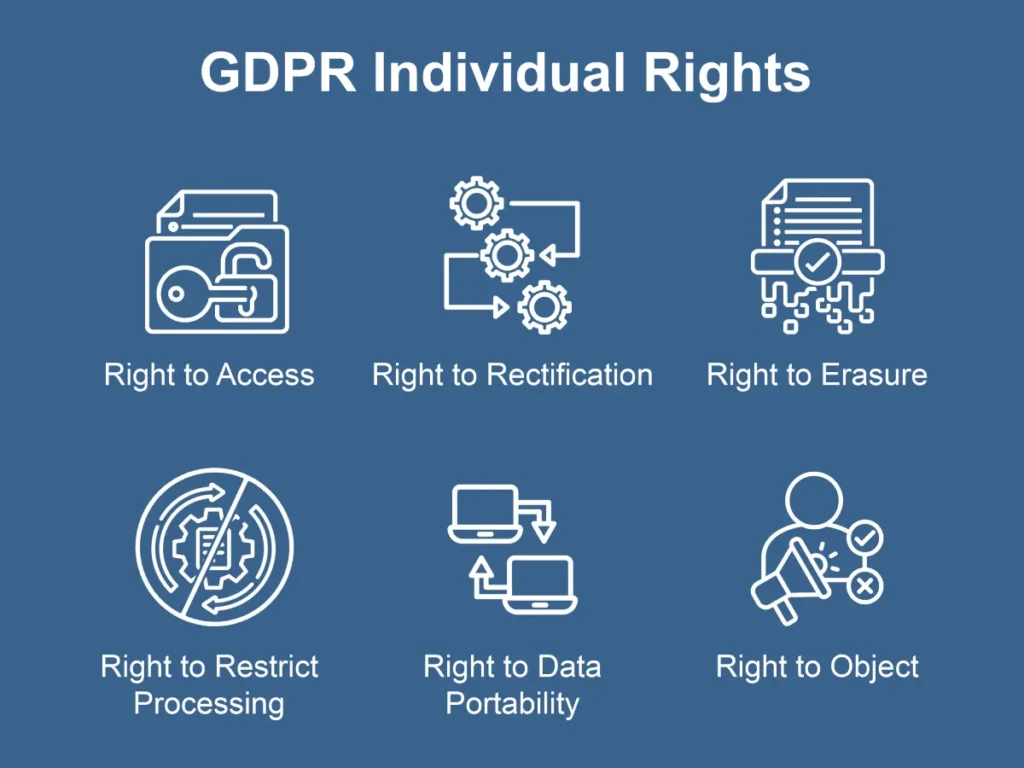
What is GDPR Compliance? Understanding the Role of DLP
What is GDPR Compliance General Data Protection Regulation Compliance, also known as GDPR Compliance, is the […]

Ransomware-Attacke auf bayerische Schulen
Hacker sind in die IT-Systeme von sieben bayerischen Schulen eingedrungen. CeltStudio – Shutterstock.com Bereits im Oktober […]

US consumer protection agency bans employee mobile calls amid Chinese hack fears
The US Consumer Financial Protection Bureau (CFPB) has issued an urgent directive barring employees and contractors […]

Threat Hunting: Strategic Approaches and Capabilities to Uncover Hidden Threats
What is Threat Hunting? Threat hunting is the discovery of malicious artifacts, activity or detection methods […]
