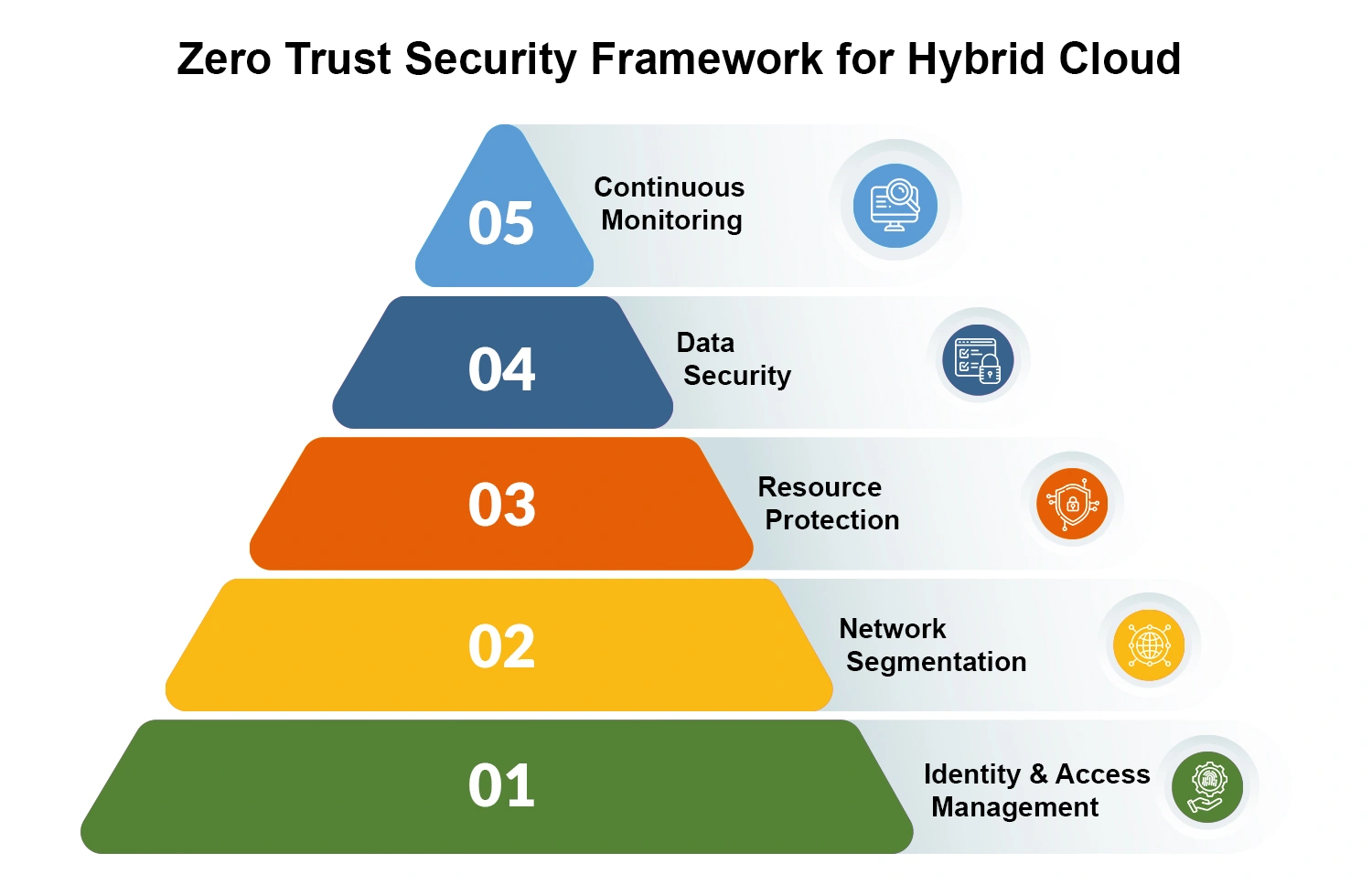
Hybrid Cloud Security: Hidden Threats Your Team Might Miss
Companies are rapidly moving to hybrid cloud environments, with most of them already making this transition. […]
Data Privacy in the Age of Quantum Computing: Is India Ready?
As we move into the era of quantum computing, businesses and governments worldwide are grappling with […]

CISOs wollen Cloud-Security vorantreiben
Cloud-Security: CISOs setzen auf Application-Protection-Plattformen (CNAPP). Digitala World – Shutterstock.com 76 Prozent der deutschen CISOs planen […]

Mac users duped with FrigidStealer posing as browser updates
Hackers are seen dropping a new macOS infoStealer, FrigidStealer, on unsuspecting systems in a web inject […]

Hackerangriff auf LUP-Kliniken: Täter haben Daten gestohlen
Krankenhäuser geraten immer öfter in das Visier von Cyberkriminellen. Jetzt hat es zwei Kliniken im Landkreis […]

Understanding OWASP’s Top 10 list of non-human identity critical risks
Verizon There are some very good reasons why non-human identities (NHI) have landed among the most-discussed […]

What is SIEM? Improving security posture through event log data
Introduction to SIEM Security information and event management software (SIEM) products have been an enduring part […]

Der trügerische Komfort des Risikomanagements
Gefahrenmanagement statt Risikomanagement: Cybersicherheit erfordert Dringlichkeit und Entschlossenheit. Billion Photos – Shutterstock.com Herkömmliches Risikomanagement basiert auf […]

CISO success story: Predicting cyber risk (accurately) is easier with this guy’s formula
You wouldn’t expect a professional jazz musician to morph into a cybersecurity policy expert, but that’s […]

Russian cyberespionage groups target Signal users with fake group invites
Russian advanced persistent threat (APT) groups are increasingly launching phishing attacks aimed at tricking users of […]
