
Public-private partnerships: A catalyst for industry growth and maturity
As cybercriminals evolve their tactics, relying on tools like AI to simplify and speed their existing […]

Ransomware-Attacke auf Mönchengladbacher Altenheimbetreiber
width=”2461″ height=”1384″ sizes=”(max-width: 2461px) 100vw, 2461px”>Eine Ransomware-Bande erpresst den Altenheimbetreiber der Stadt Mönchengladbach mit verschlüsselten Daten. […]

New Windows zero-day feared abused in widespread espionage for years
A zero-day vulnerability stemming from how Windows User Interface handles its shortcut (.lnk) files has been […]
„Ich bin kein Roboter“ – aber ein mögliches Cyber-Opfer
Experten haben mehrere Kampagnen entdeckt, bei denen Angreifer unter anderem steigende „Klick-Toleranz“ mit mehrstufigen Infektionsketten ausnutzen. […]
UK cyber agency suggests 2035 deadline to move to quantum-safe encryption, warns of threats
The UK’s National Cyber Security Centre (NCSC) has warned that future quantum computers could break today’s […]

Hacker nutzen alte Windows-Sicherheitslücke aus – Microsoft tut nichts
Timepopo – shutterstock.com Experten des Sicherheits-Unternehmens Trend Micro haben eine als ZDI-CAN-25373 bezeichnete Sicherheitslücke in Windows entdeckt, die Angreifer […]

How CISOs are approaching staffing diversity with DEI initiatives under pressure
For many years, organizations have focused a lot on diversity, equity, and inclusion (DEI) programs and […]

DOGE’s cost-cutting database dives offer cybersecurity pros vital lessons in cloud security
Cybersecurity has been politically agnostic until recently, but with the many rapid changes introduced by the […]

6 Mittel gegen Security-Tool-Wildwuchs
Viel hilft nicht immer viel. Foto: Roman Samborskyi | shutterstock.com Auf der Suche nach Möglichkeiten, sich […]
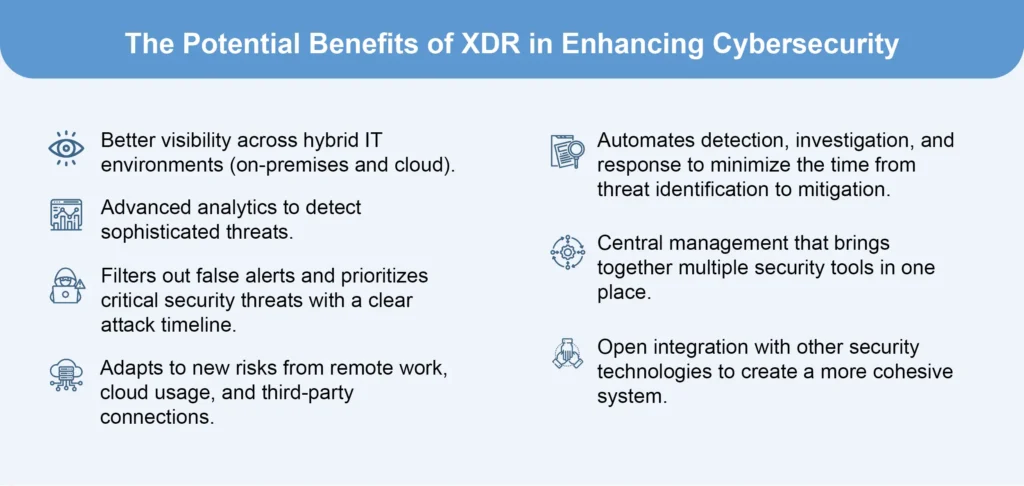
Addressing Security Gaps Using XDR: Enhance Threat Detection & Response
For many organizations, cybersecurity and threat detection are still challenging topics. Some companies’ current security systems […]
