Are paravirtualized drivers a security risk?
Summary – Paravirtualized drivers can be a security risk if not properly secured. – the Use […]
Are stronger passwords safe in case of a breach?
#NAME? The post Are stronger passwords safe in case of a breach? appeared first on Blog […]
Are Windows password hashes salted with the user name?
Summary – Yes, Windows password hashes are Salted with the user name. – the Salt is […]
Best practices for securing open APIs from quota theft
#NAME? The post Best practices for securing open APIs from quota theft appeared first on Blog […]
Buffer overflow attack executing an uncalled function
Summary – Buffer Overflow attacks occur when An attacker injects more Data into a Buffer than […]
Best practices for integrating external javascript?
#NAME? The post Best practices for integrating external javascript? appeared first on Blog – G5 Cyber […]
Are pwgen’s default passwords good enough for online accounts and encryption?
#NAME? The post Are pwgen’s default passwords good enough for online accounts and encryption? appeared first […]
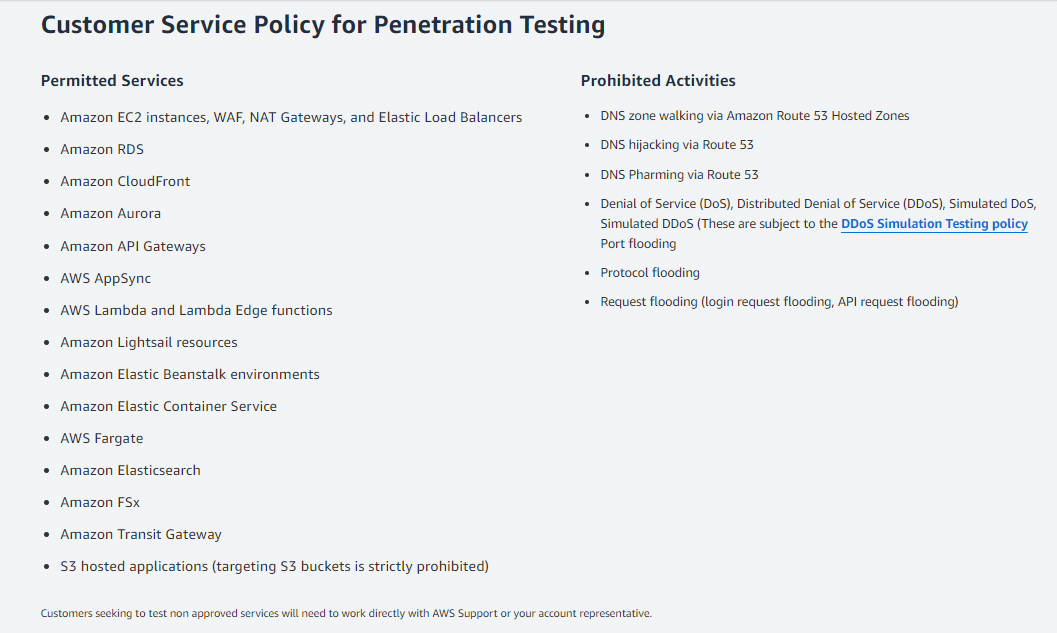
AWS Penetration Testing | Amazon Cloud Security
Migrating your business to the Amazon Web Services (AWS) cloud can be a game-changer, offering scalability, […]
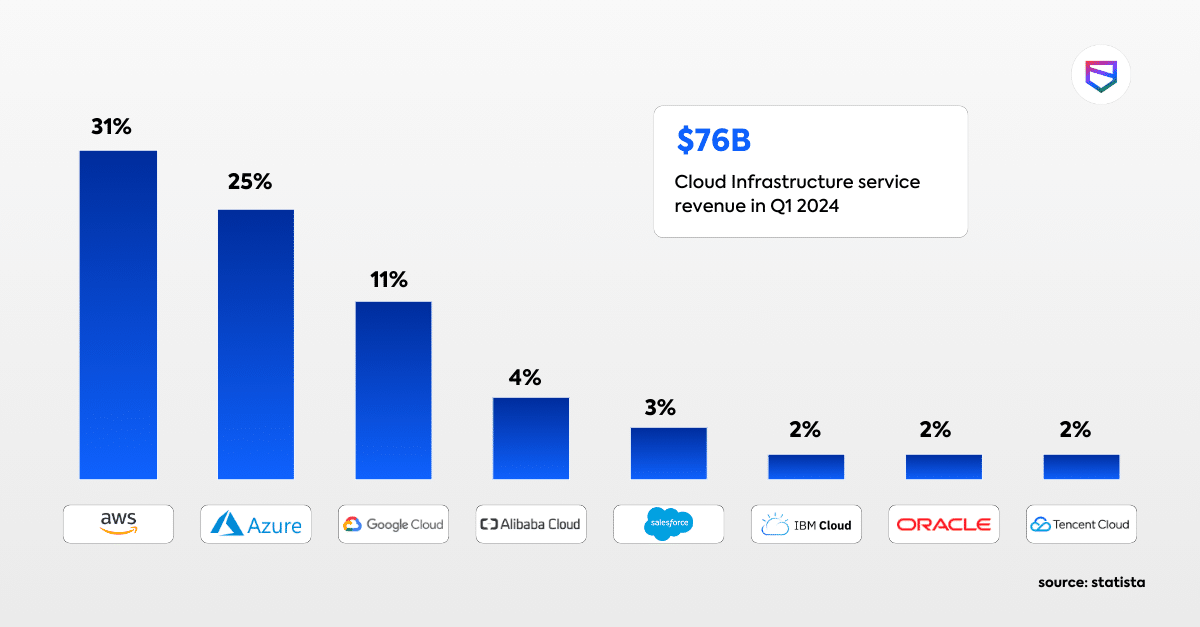
Cloud Pentesting 101: What to Expect from a Cloud Penetration Test?
Hold on, let’s guess. You’ve moved a ton of your business to the cloud – storage, […]
Cyber Security Operation Center Guidelines for best practices SOC Design
Cyber Security is become most needed services for all business and industries in 2024. Every business […]
