
New ransomware Yurei adopts open-source tools for double-extortion campaigns
A new ransomware group called Yurei has surfaced, adopting a double-extortion model. The group encrypts the […]

Samsung’s image library flaw opens a zero-click backdoor
Samsung has disclosed a serious vulnerability affecting a core utility within its Android devices, one that […]
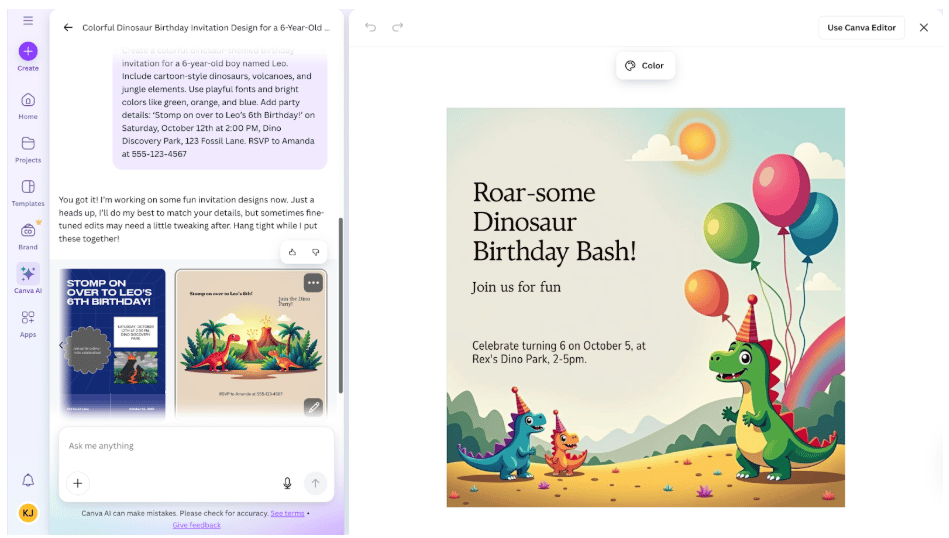
Best AI Tools for Party Planning
Throwing a party sounds fun, but often, you find yourself drowning in theme ideas, endless guest […]

Your SOC is the parachute — Will it open?
The security economy revolves around the assumption that security operations centres (SOCs) will save organizations. Spend […]
What augmented intelligence really means for fintech leaders
Artificial Intelligence (AI) has been the buzzword in the fintech industry more than ten years now. […]

5 trends reshaping IT security strategies today
Cybersecurity’s core mission remains the same: Defend the organization from all the dangers that lurk in […]

9 unverzichtbare Open-Source-Security-Tools
Diese Open-Source-Tools adressieren spezifische Security-Probleme – mit minimalem Footprint. Foto: N Universe | shutterstock.com Cybersicherheitsexperten verlassen […]

Zehn Karrierekiller für CISOs
CISOs müssen sich anpassen und weiterentwickeln. Nur so können sie selbst und ihre arbeitgebenden Unternehmen florieren. […]

VoidProxy phishing-as-a-service operation steals Microsoft, Google login credentials
Identity and access management provider Okta has discovered what it says is a novel phishing-as-a-service (PhaaS) […]

VMScape Spectre BTI attack breaks VM isolation on AMD and Intel CPUs
Researchers have demonstrated a Spectre-like CPU branch target injection attack that allows malicious virtual machine users […]
