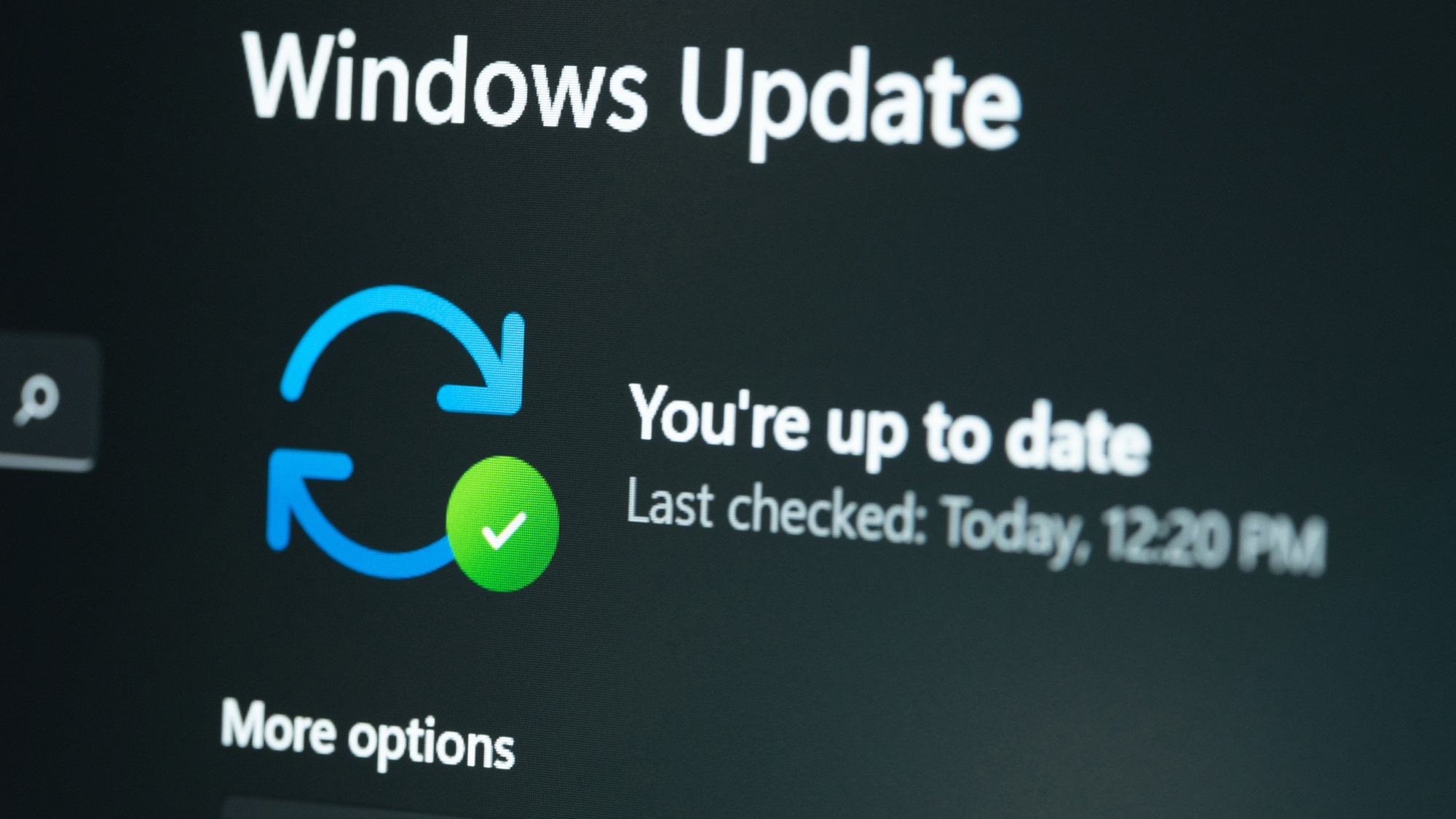
Security patch or self-inflicted DDoS? Microsoft update knocks out key enterprise functions
An October 2025 Microsoft Windows security update is wreaking havoc on enterprises, impacting multiple systems with […]

CISOs’ security priorities reveal an augmented cyber agenda
Technology may be changing rapidly but one thing remains constant: It’s not an easy time to […]

US NSA alleged to have launched a cyber attack on a Chinese agency
China’s claim that the US National Security Agency (NSA) was behind a cyber attack against the […]
Best AI Tools for Bookworms and Avid Readers
Do you ever feel like you’re drowning in books and wonder when you’ll finally catch up? […]
Math-etic! GPT-5’s Math ‘Breakthrough’ Gets F-Minus for Hype
In a very public, very awkward lesson on the difference between “solving” a problem and simply […]
Google Report Finds Teen AI Use Soaring — and Creativity Along With It
AI has become a fixture in European teens’ daily lives, and it’s unlocking a surge of […]
Chipmaker TSMC’s Profits Soar 39% Due to AI Demand
Taiwan Semiconductor Manufacturing Company announced explosive earnings, with profits soaring nearly 40% as artificial intelligence demand […]

Hacker verkaufen Daten von Geiger im Darknet
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_1709962954.jpg?quality=50&strip=all 5616w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_1709962954.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_1709962954.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_1709962954.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_1709962954.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_1709962954.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_1709962954.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_1709962954.jpg?resize=150%2C84&quality=50&strip=all 150w, […]
The Real AI Power Play: Who Controls Your Enterprise Data Layer?
IT and data teams were promised that AI would make work easier. Instead, it’s created new […]

Threat actors are spreading malicious extensions via VS marketplaces
Careless developers publishing Visual Studio extensions to two open marketplaces have been including access tokens and […]
