
7 Anzeichen für akuten MSSP-Bedarf
Managed Security Service Provider können das Sicherheitsniveau nachhaltig steigern. Godlikeart | shutterstock.com Ein Managed Security Service […]

LeakBase marketplace unplugged by cops in 14 countries
The LeakBase cyberforum, considered one of the world’s largest online marketplaces for cybercriminals to buy and […]

How Does Endpoint Deception Detect Attacks Before Damage Happens?
Key Takeaways Endpoint deception technology helps detect threats before exploitation spreads. Deception endpoint coverage expands visibility […]

Detecting Living-off-the-Land Attacks in OT Networks
Key Takeaways LOTL attacks use trusted tools like PowerShell, WMI, and RDP, making malicious activity appear […]

Cisco issues emergency patches for critical firewall vulnerabilities
Cisco has handed security teams one of the largest ever patching workloads affecting its firewall products, […]

Coruna iOS exploit kit moved from spy tool to mass criminal campaign in under a year
Google’s threat intelligence researchers have identified a sophisticated exploit kit targeting iPhones that was first used […]

Europol: Großer Markt für gestohlene Daten geschlossen
Europol koordinierte den Schlag gegen Leakbase. PixelBiss – shutterstock.com Die Polizei von Amsterdam hat im Zuge […]
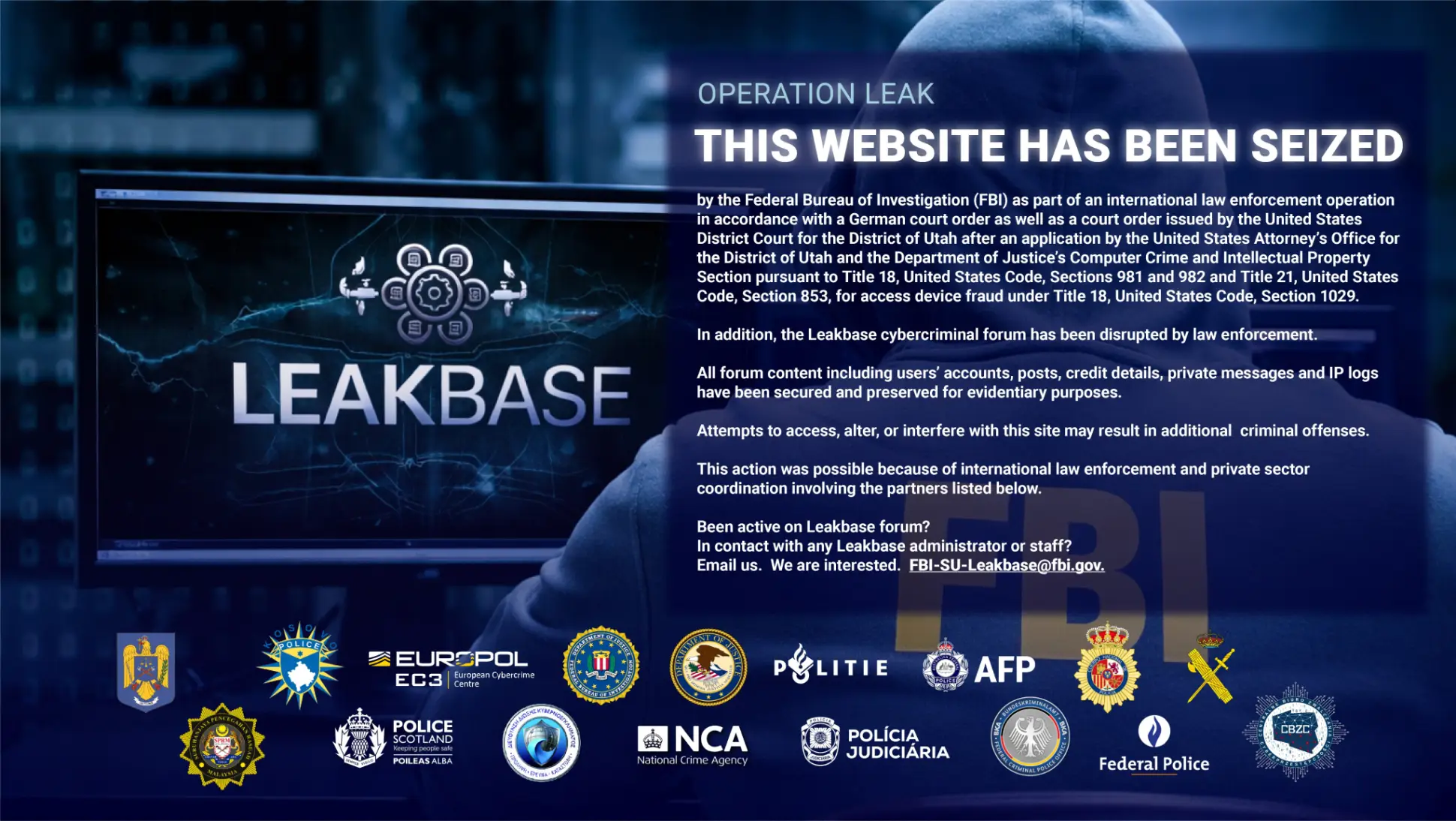
Europol schließt riesigen Markt für gestohlene Daten
loading=”lazy” width=”400px”>LeakBase wird von den Strafverfolgungsbehörden untersucht. Die Polizei von Amsterdam hat im Zuge einer internationalen […]

State-affiliated hackers set up for critical OT attacks that operators may not detect
Several state-linked threat groups known for breaking into operational technology (OT) networks have shifted their focus […]

14 old software bugs that took way too long to squash
In 2021, a vulnerability was revealed in a system that lay at the foundation of modern […]
