
6 ways hackers hide their tracks
CISOs have an array of ever-growing tools at their disposal to monitor networks and endpoint systems […]

Windows tips for reducing the ransomware threat
As Scattered Spider headlines have reminded us of late, ransomware is always in season. The group […]

Beef up AI security with zero trust principles
Many CSOs worry about their firm’s AI agents spitting out advice to users on how to […]

IT-Security-Jobs – 5 bittere Wahrheiten
Viel Geld schützt nicht vor Burnout. Volodymyr TVERDOKHLIB | shutterstock.com Die Nachfrage nach Cybersecurity-Spezialisten ist ähnlich […]

Durch Datenlecks verursachte Kosten sind gefallen
Durch KI unterstützte Angriffe wie Phishing und Deepfakes nehmen weiter zu, doch Unternehmen zögern in gleichem […]

Researchers uncover RCE attack chains in popular enterprise credential vaults
Researchers have found 14 logic flaws in various components of HashiCorp Vault and CyberArk Conjur, two […]
ReVault flaws let attackers bypass Windows login or place malware implants on Dell laptops
Flaws in the firmware that ships with more than 100 models of Dell business laptops compromise […]
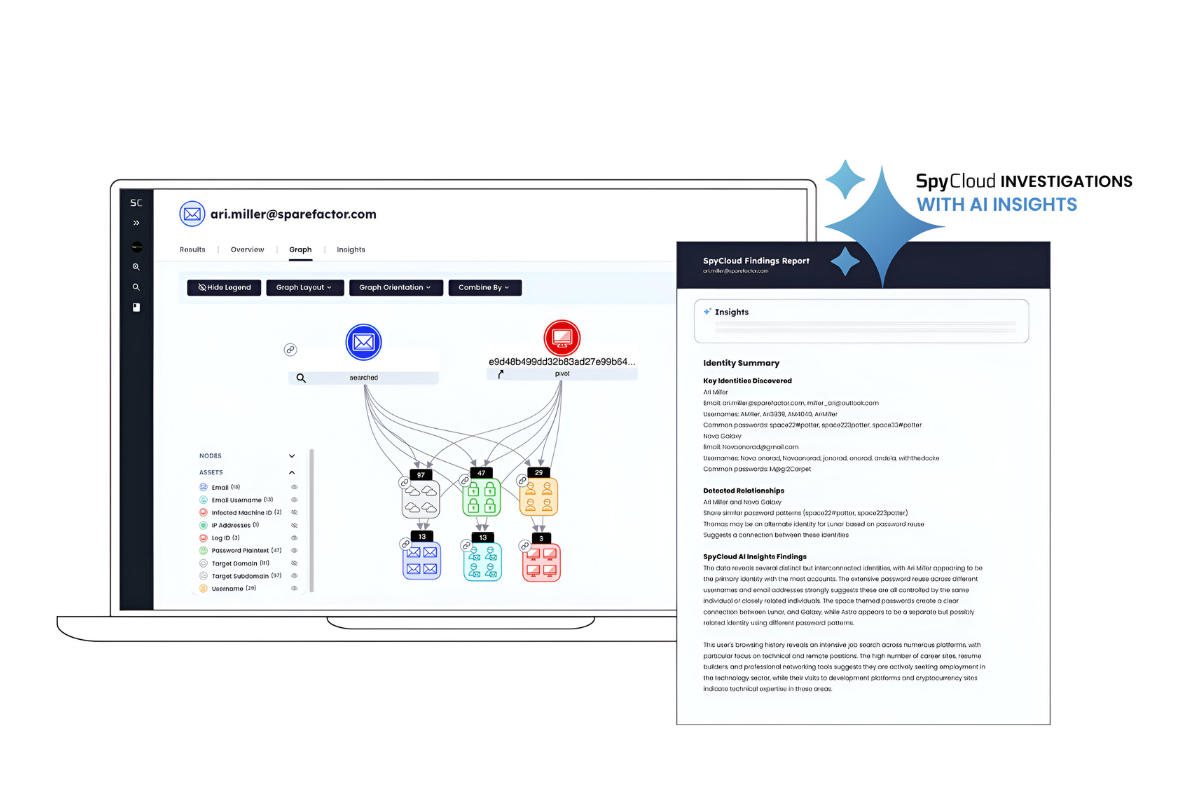
SpyCloud Enhances Investigations Solution with AI-Powered Insights – Revolutionizing Insider Threat and Cybercrime Analysis
SpyCloud Investigations, now with AI Insights, empowers security teams to act decisively with finished intelligence built […]

Akira affiliates abuse legitimate Windows drivers to evade detection in SonicWall attacks
Threat researchers at GuidePoint Security have uncovered Akira affiliates abusing legitimate Windows drivers in a previously […]
Countdown to QDay: Is Your Data Ready for the Quantum Reckoning?
Within the next decade, the encryption that safeguards your business’s most sensitive data could be shattered […]
