
Munich Reinsurance unites global security teams to boost resilience, cut costs
When an insurer takes on big risks—whether it’s covering homes, cars, or health care—it often turns […]
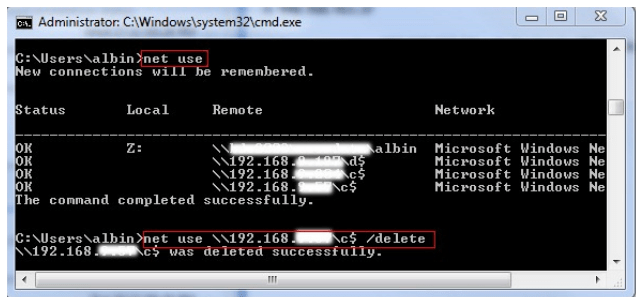
Hunt Evil Your Practical Guide to Threat Hunting – Part 2
As we discussed in the Part 1 , adversaries will come in many forms and will […]

2025 CSO Hall of Fame: Meg Anderson on AI, strategic security investments, and life after InfoSec
Meg Anderson has spent nearly two decades leading enterprise cybersecurity, most recently as vice president and […]

Need help with AI safety? Stay ahead of risks with these tools and frameworks
The Cloud Security Alliance (CSA) has spent the past 14 years bringing together experts to help […]

Meet the unsung silent hero of cyber resilience you’ve been ignoring
At 02:17 a.m., the Security Information and Event Management (SIEM) dashboard blinked. A remote user had […]

BSI-E-Mail-Checker soll vor Hackern schützen
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/08/shutterstock_2344891127.jpg?quality=50&strip=all 4539w, https://b2b-contenthub.com/wp-content/uploads/2025/08/shutterstock_2344891127.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/08/shutterstock_2344891127.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/08/shutterstock_2344891127.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/08/shutterstock_2344891127.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/08/shutterstock_2344891127.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/08/shutterstock_2344891127.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/08/shutterstock_2344891127.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

Rowhammer attack can backdoor AI models with one devastating bit flip
A team of researchers from George Mason University has developed a new method of using the […]

BSI-Doppelstrategie für digitale Souveränität
width=”4743″ height=”2667″ sizes=”auto, (max-width: 4743px) 100vw, 4743px”>BSI-Präsidentin Claudia Plattner: “Je mehr vertrauenswürdige Produkte verfügbar sind, desto […]

83% of CISOs say staff shortage is major issue for defense
Most enterprise CISOs can’t remember a time when there wasn’ta cybersecurity talent shortage, but a new […]

How AI is reshaping cybersecurity operations
Generative AI has become a pervasive tool in the enterprise. According to a recent Boston Consulting […]
