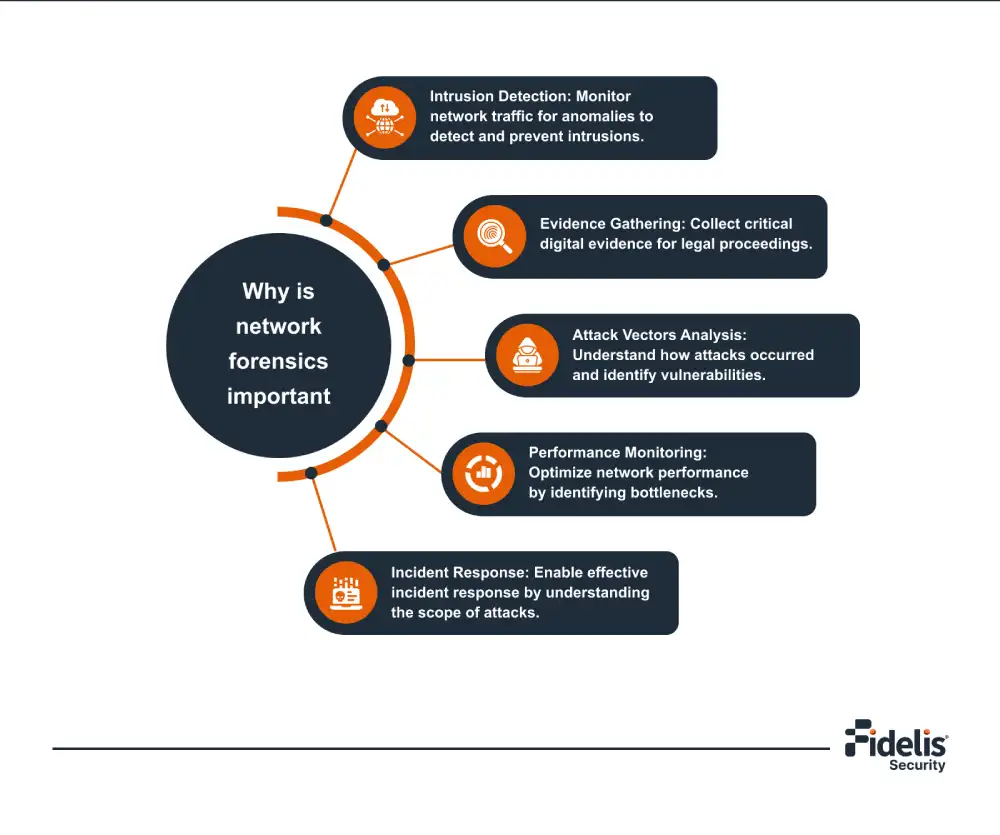
The Role of Network Forensics in Identifying Threats
The outlook of cyber threats in this modern cyber warfare theater has changed a great deal. […]
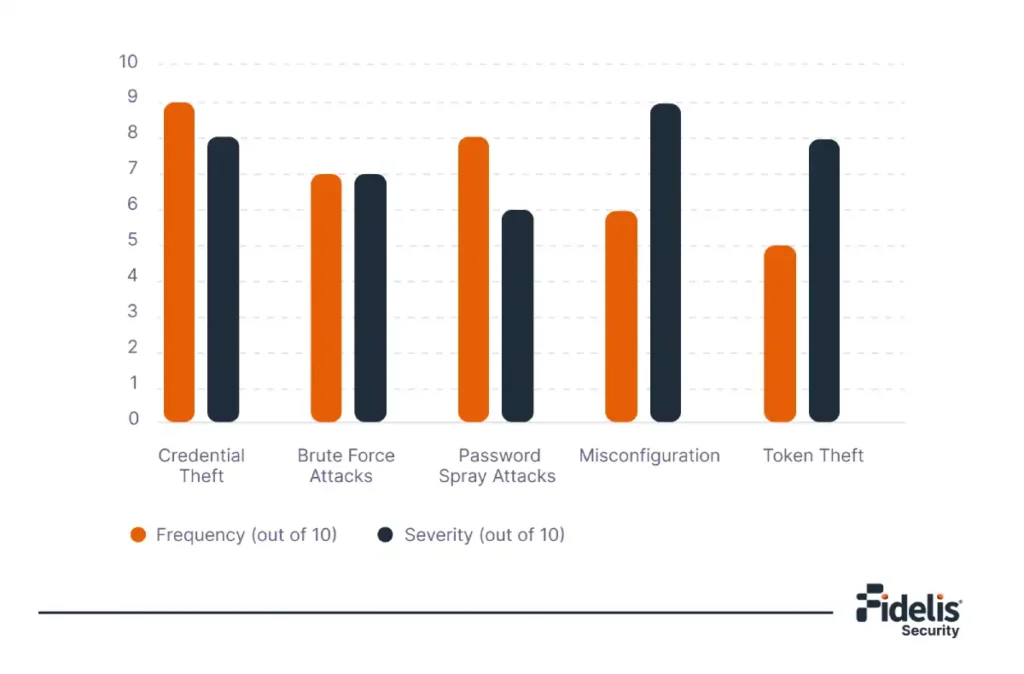
Elevate Your Azure AD Security Before the Next Attack
As 98% of businesses are using some form of cloud computing, keeping track of who has […]
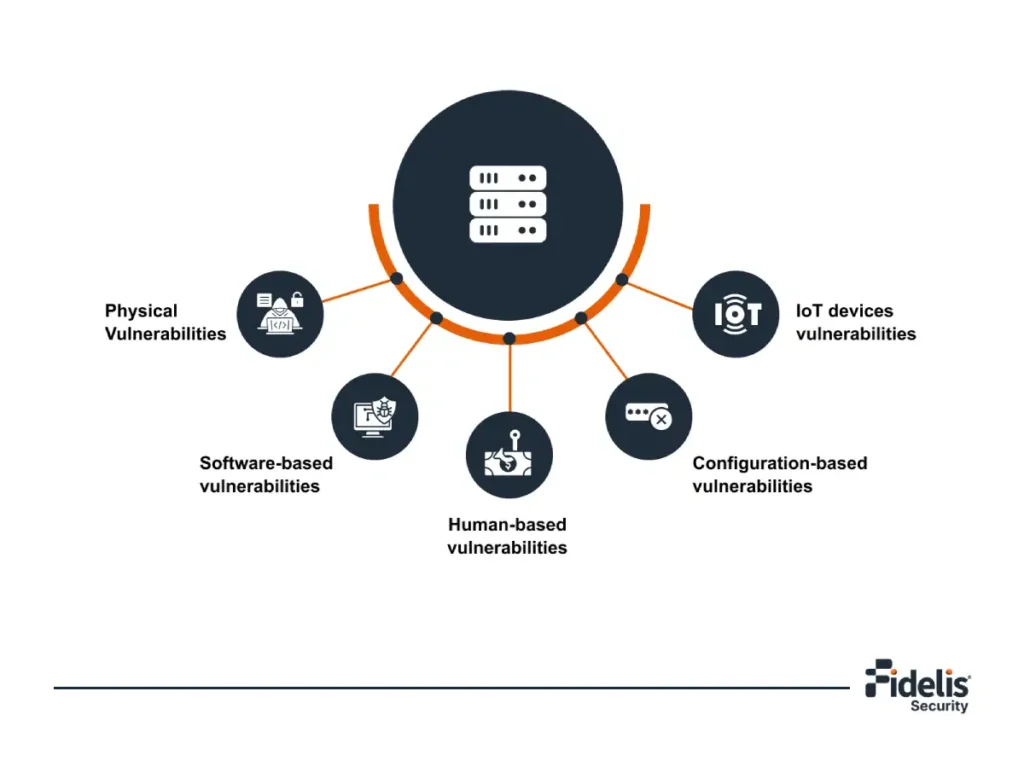
Network Vulnerabilities and Threats: A Cyber-Security Challenge
The digital world is under constant risk as cyber-attacks are becoming increasingly advanced and increasing at […]
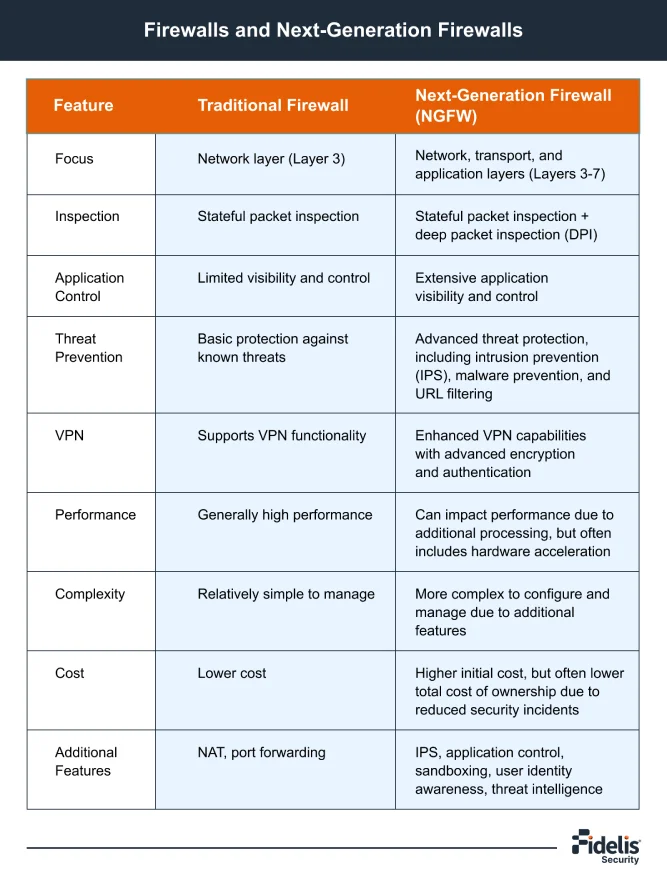
What Are Network Security Solutions?
Picture this, you are trying to protect a chest full of treasure and have no idea […]
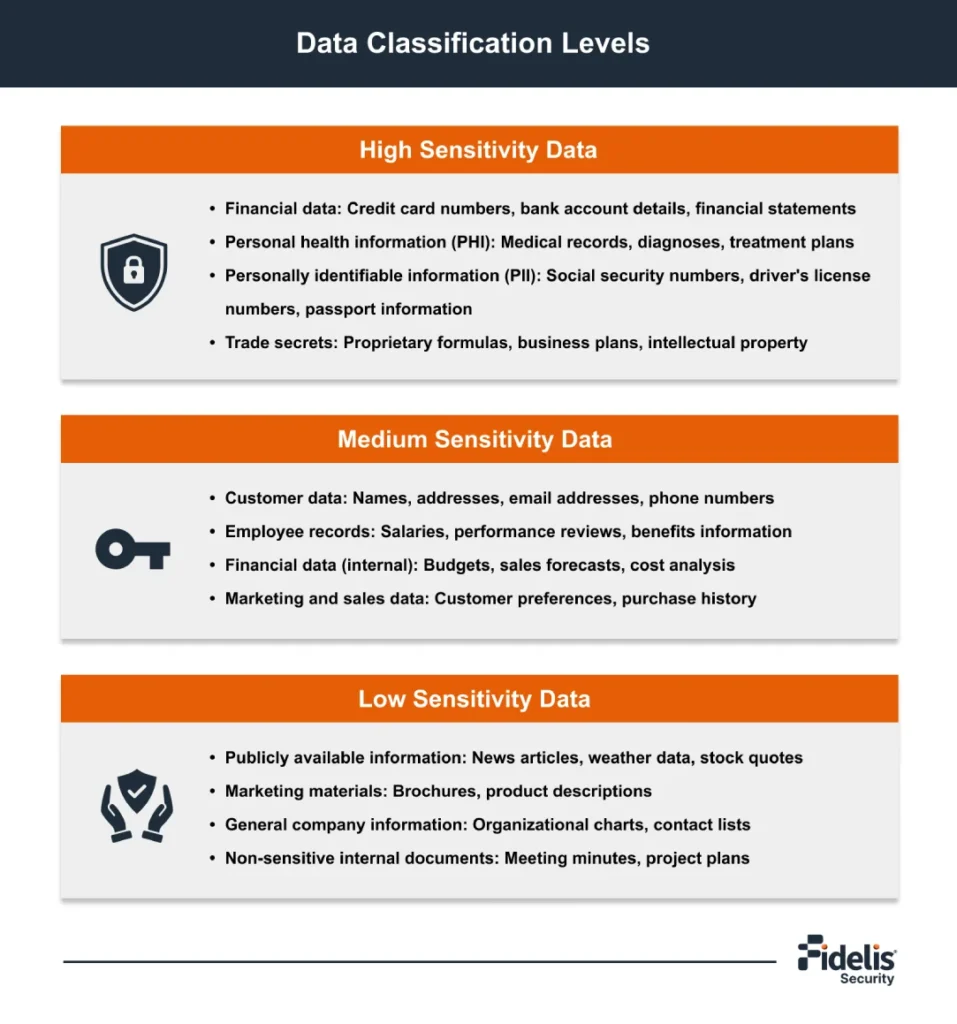
How to Classify, Protect, and Control Your Data: The Ultimate Guide to Data Classification
In our digital world, data fuels businesses. This power brings huge responsibility. Cyber threats are real […]
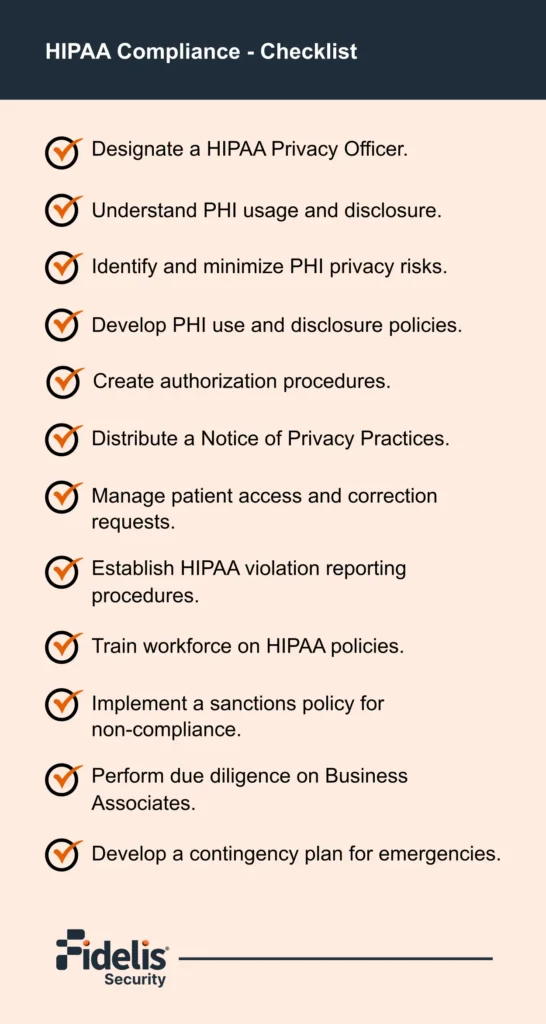
Comprehensive Guide to Healthcare Data Security: Essential Safety and Compliance Tips
Healthcare data security is one of the top responsibilities in this digital age. Since patients’ sensitive […]
What Is an Endpoint Protection Platform (EPP)?
Defining an Endpoint Protection Platform An Endpoint Protection Platform is an endpoint security capability designed to […]
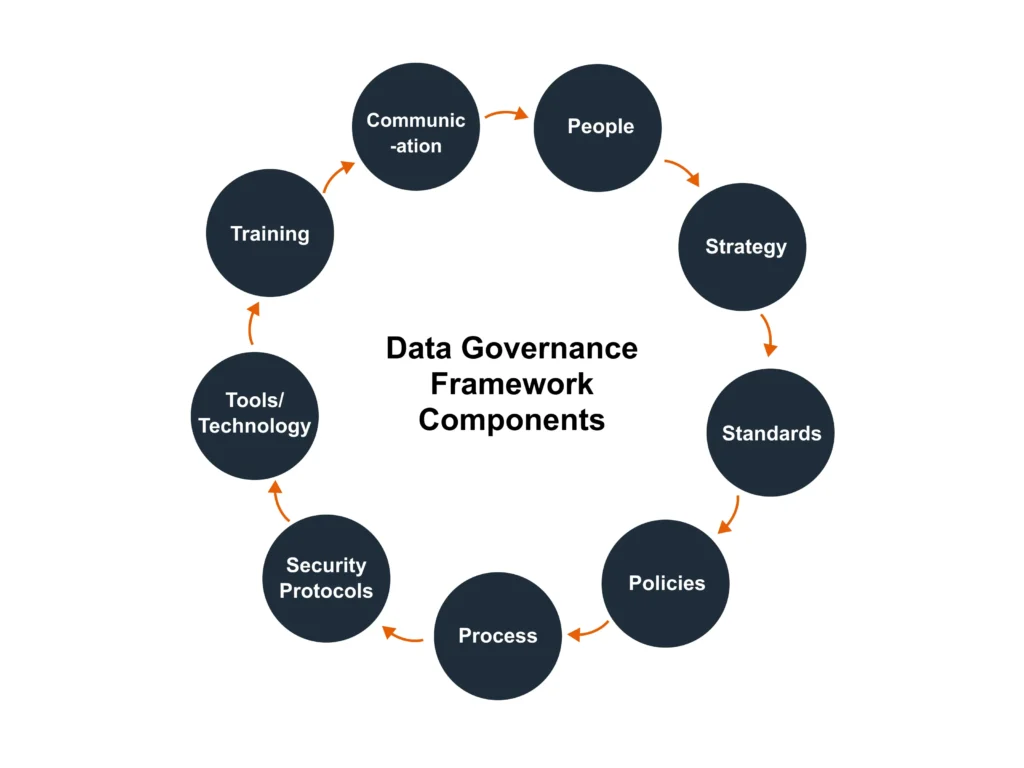
Data Governance Framework: Unlocking the Power of Enterprise Data
Data has become the lifeblood of modern businesses, influencing important business decisions and powering digital transformation […]
How Observability Leads to Better Cybersecurity
The term “observability” refers both to the concept of monitoring, analyzing, and understanding all data moving […]

How To Scan a Website for Vulnerabilities: Top Tools and Techniques
Knowing how to scan a website for vulnerabilities can help keep you protected in today’s digital […]