
Addressing Cloud Security Blind Spots for Better Protection
As businesses increasingly migrate to the cloud, securing these dynamic environments has become more challenging than […]
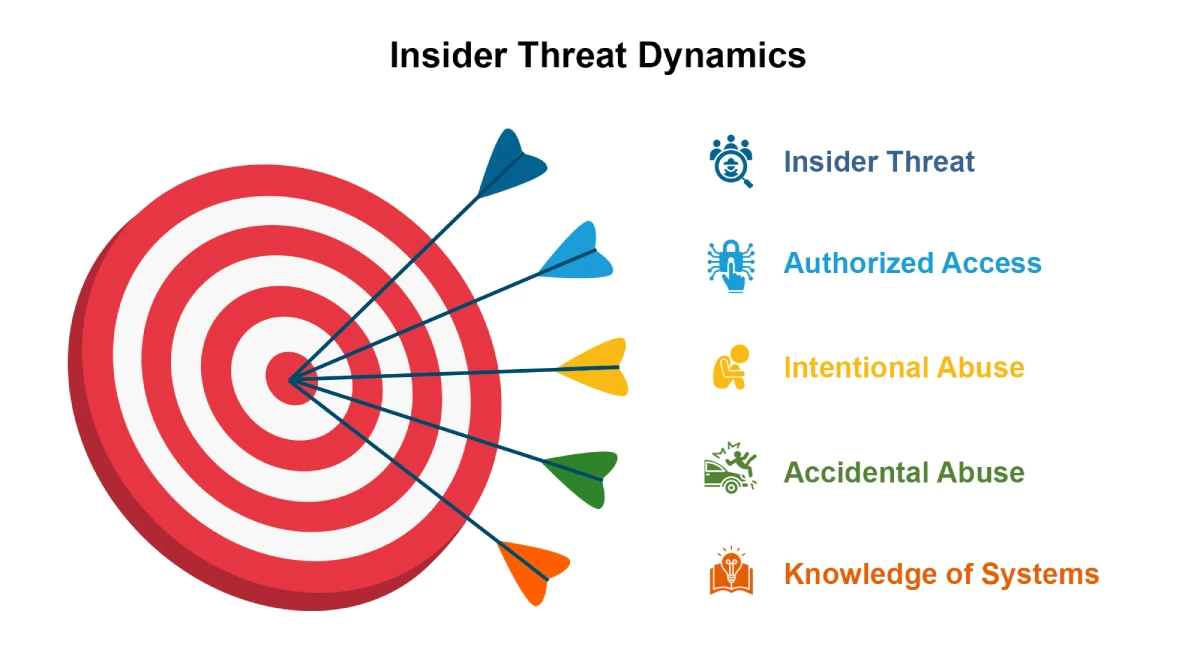
Mitigating Insider Threats with Deception: A Game-Changing Security Approach for 2025
“The greatest information security threat is not from the professional social engineer, nor from the skilled […]
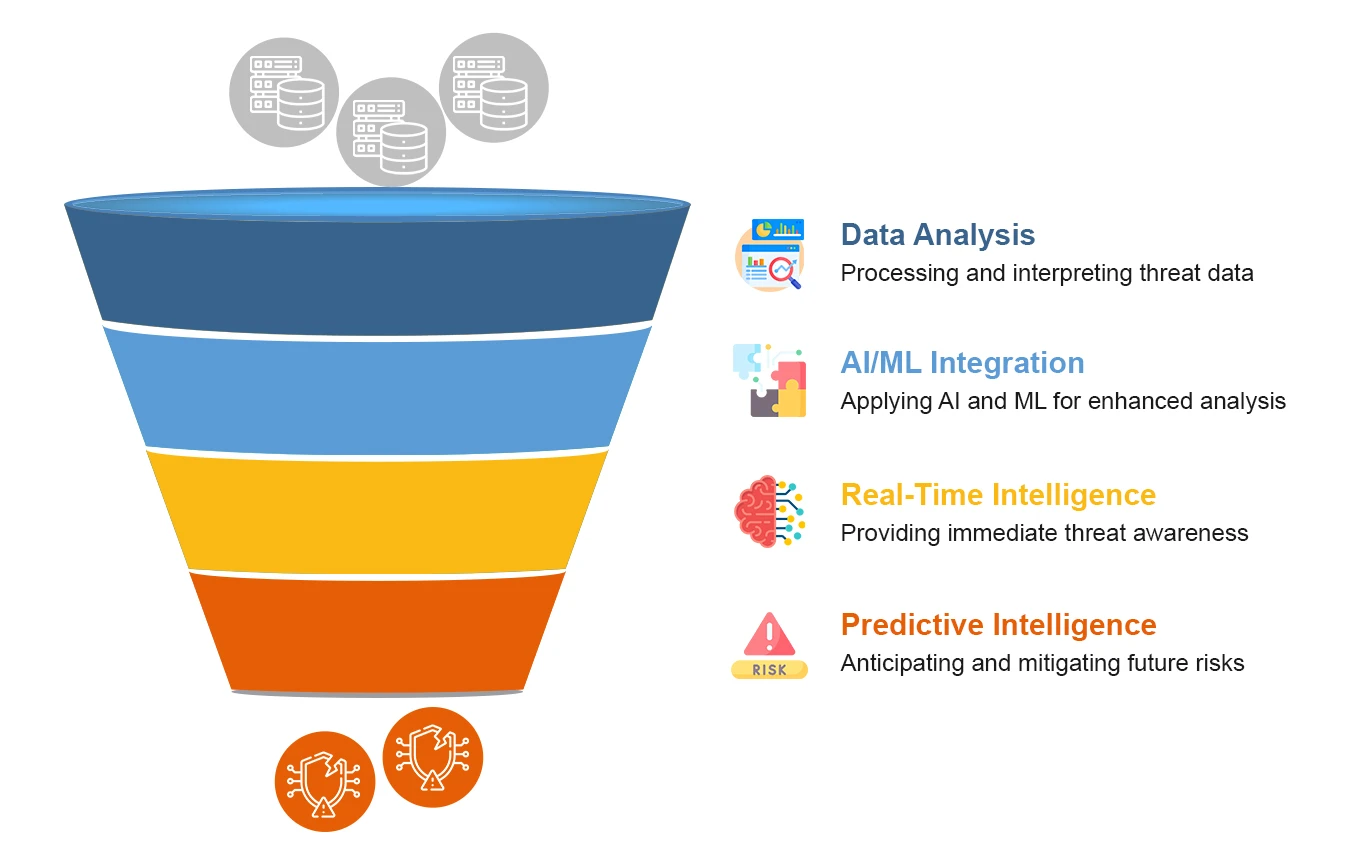
The Future of Cyber Defense: Smarter, Faster, Stronger
Not only are cyberthreats increasing, but they are also evolving at an unprecedented rate. To bypass […]
What to Look for in an NDR Solution: A Buyer’s Guide to Cutting-Edge Features
As cyberattacks become more complex, network detection and response solutions have become essential for modern organizations. […]
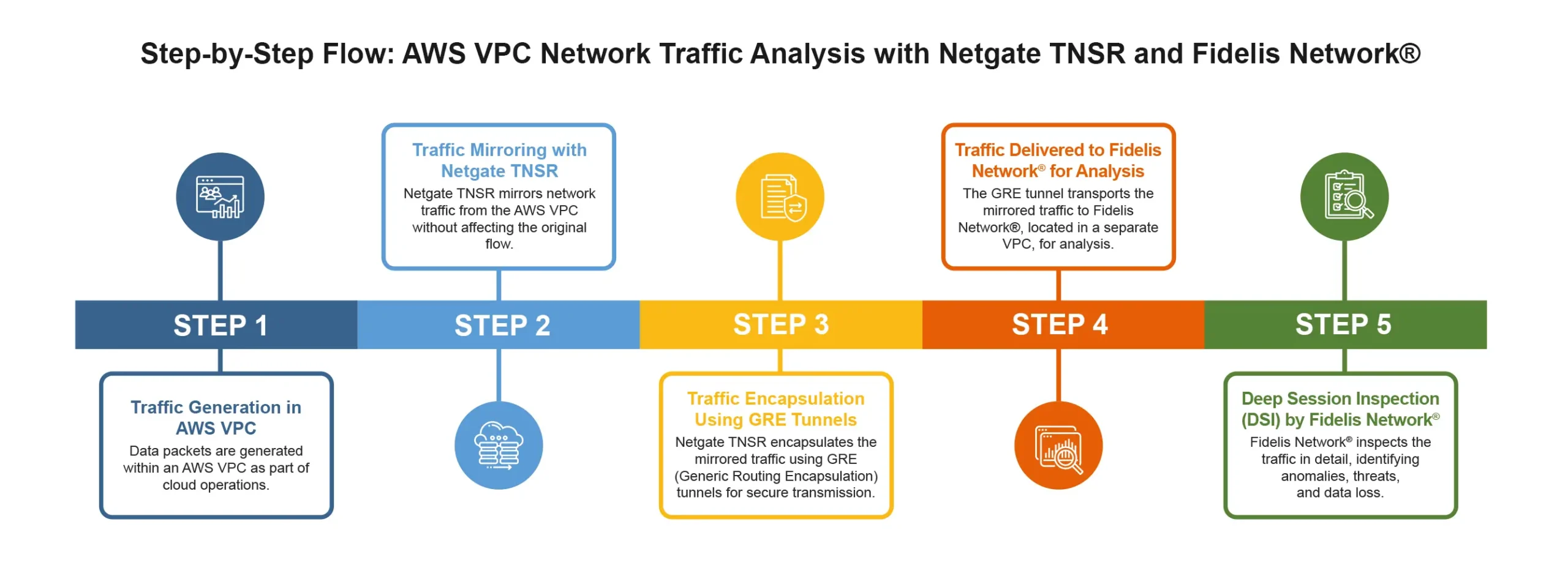
Fidelis Network® for Amazon VPC Traffic Mirroring
Over the last decade, cloud computing has become the backbone of modern business, transforming how organizations […]
Why Your Network Flow Analysis Fails (And How to Fix It)
A recent report reveals that 98% of businesses struggle with growing complexity in their cloud and on-premises infrastructures. […]
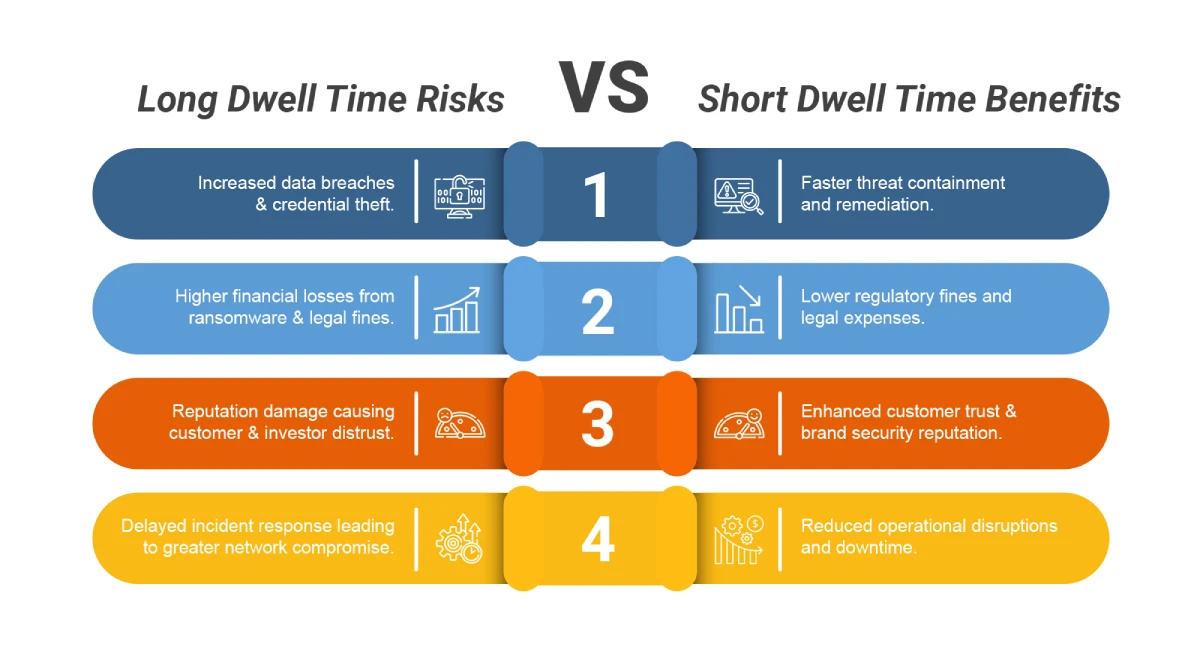
Top 5 Strategies to Reduce Dwell Time with XDR: Accelerating Threat Detection and Response
Why Is Dwell Time a Critical Security Risk? Cyber adversaries operate with one goal in mind—stealth. […]

Anomaly Detection Algorithms: A Comprehensive Guide
Data anomalies indicate serious issues like fraud, cyberattacks, or system breakdowns. It is crucial to preserve […]
Choosing the Right CNAPP: Essential Tips for Effective Decision-Making
What is CNAPP? A Cloud-Native Application Protection Platform (CNAPP) is an integrated cloud security solution designed […]
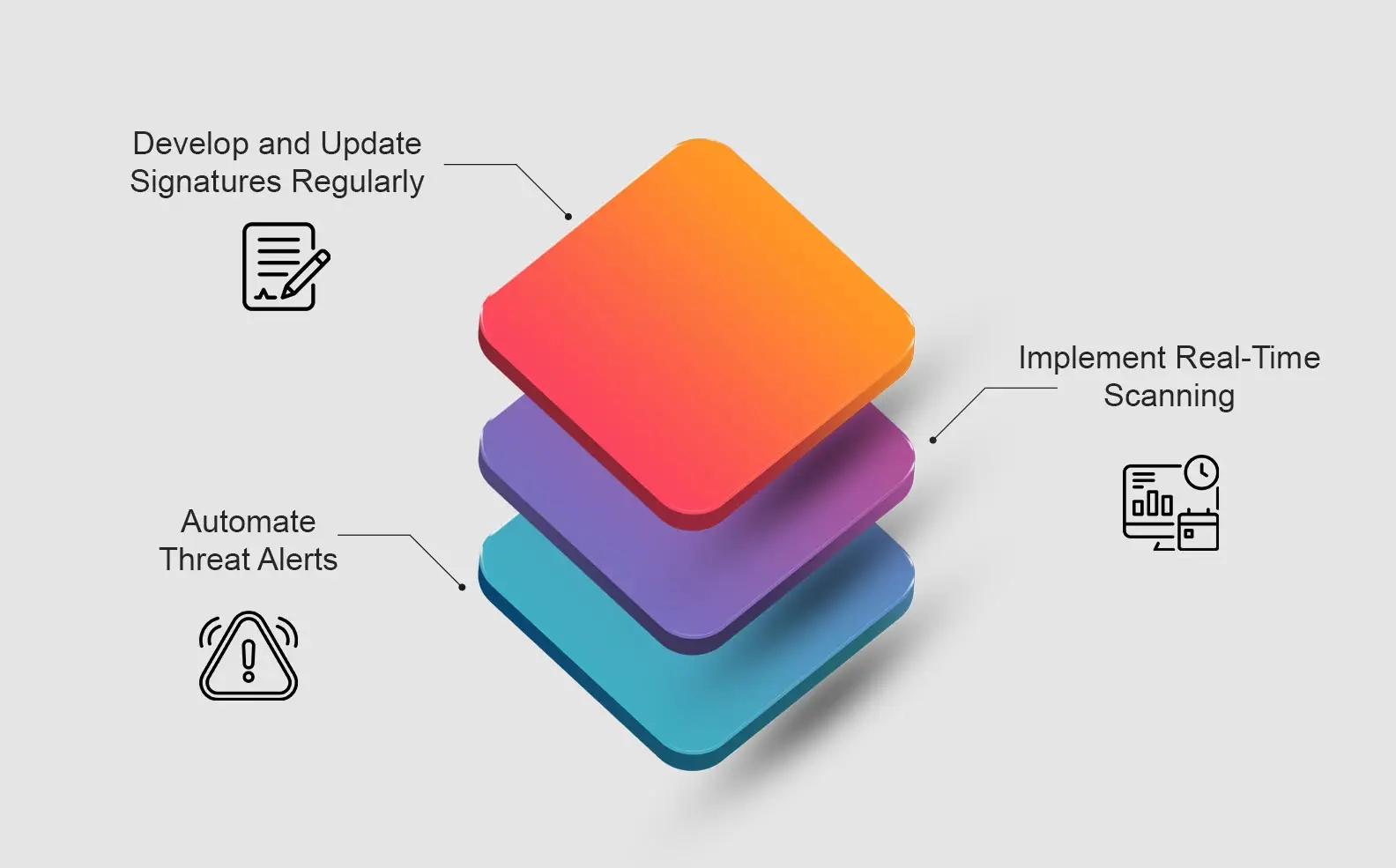
Breaking Down Signature-Based Detection: A Practical Guide
Nearly 90% of cyberattacks are known methods that proper systems can detect, but most organizations don’t […]