How Deception Fits into Zero Trust and MITRE Shield Frameworks
A technical analysis of deception technology’s role in modern cybersecurity frameworks In today’s evolving threat landscape, […]
5-Step Plan for Prevention of Social Engineering Attacks
Cyber threats aren’t always about complex code or advanced hacking tools. Often, they start with a […]
Top 5 Proactive Threat Intelligence Use Cases for Enhanced Cyber Defense
In this fast-moving world where businesses operate completely through IT infrastructure, waiting for a threat to […]
Cyber Deception as a Strategic Pillar in Active Defense
Understanding deception for active defense The cat-and-mouse game of cybersecurity never stops, and cyber deception in […]
Difference Between Fidelis’ Deep Session Inspection ™ and Traditional Deep Packet Inspection (DPI)
Deep Packet Inspection (DPI) was once the go-to method for monitoring network traffic, but it now […]
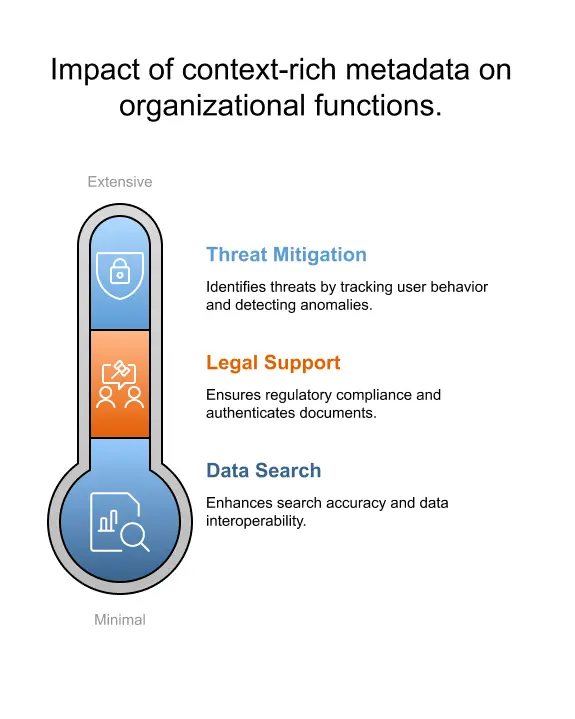
Context Rich Metadata: Best Practices and Techniques for Enhanced Data Analysis
Are you struggling to make sense of your data files and ensure compliance with ever-changing regulations? […]
Mapping Your Cyber Terrain: Understanding Use Cases and How Fidelis Helps
Effective cybersecurity begins with knowing what you’re defending. Organizations investing heavily in security tools often miss […]
Role of Deception for Lateral Movement Detection: A Strategic Guide
Understanding Lateral Movement in Modern Networks Lateral movement plays a crucial role in the attack chain. […]
Decoding Fidelis Deception Technology to Outsmart Attackers with Fidelis Elevate®
In today’s digital battlefield, attackers aren’t just breaking in—they’re sneaking past defenses, staying hidden, and making […]
Analyzing Advanced Persistent Threats (APTs) in Threat Intelligence for Government Agencies
It doesn’t matter which industry you belong to; cybersecurity is one of the most important factors […]