What Happens If AI Actually Makes Us All Smarter?
Affirm CEO Max Levchin says artificial intelligence is boosting humanity’s brainpower. Speaking on TBPN last Friday, […]
What Happens If AI Actually Makes Us All Smarter?
Affirm CEO Max Levchin says artificial intelligence is boosting humanity’s brainpower. Speaking on TBPN last Friday, […]
These AI Smart Glasses Are Always Recording: Experts Weigh in on Risks & Benefits
A startup has raised $1 million to develop always-on, AI-equipped smart glasses it calls a “second […]
These AI Smart Glasses Are Always Recording: Experts Weigh in on Risks & Benefits
A startup has raised $1 million to develop always-on, AI-equipped smart glasses it calls a “second […]

What Should You Expect from a Modern Network Threat Detection Platform?
Many security teams struggle to see the full scope of threats because network, endpoint, and cloud […]

The Role of Behavioral Machine Learning in Detecting Network Anomalies at Scale
Enterprise networks face a fundamental challenge: traditional signature-based detection methods fail against sophisticated threats that deliberately […]

What to Do When Your Backyard Turns Into a Disaster Zone
Sometimes you walk outside and it’s clear: the yard’s a mess. Grass is taller than it […]

What Deep Investigation Really Looks Like: A SOC Analyst’s Perspective
Deep investigation in cybersecurity isn’t just about watching dashboards and clicking “resolve” on tickets. It’s an […]
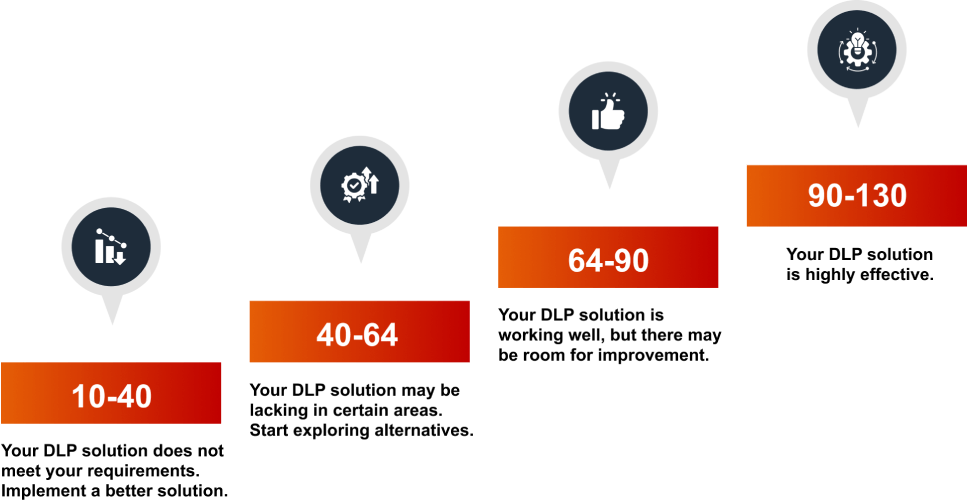
How Advanced DLP Accelerates Data Breach Recovery and Reduces Regulatory Risk
Data breach recovery has become a top priority for organizations in today’s digital world. Organizations must […]
Claude-for-Chrome Pilot: Anthropic Takes Cautious Step Into AI Browser Wars
Anthropic, the company behind the Claude AI assistant, has begun testing a Chrome extension that allows […]