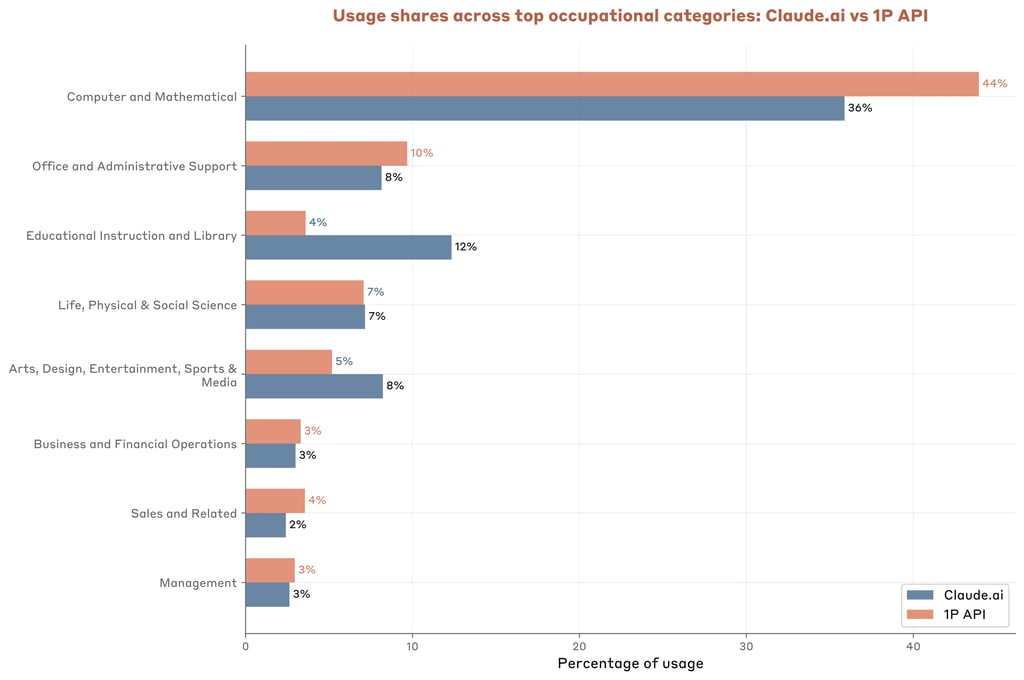
Anthropic’s AI Usage Study: Coding Still Dominates, Education and Science Increases
Anthropic has released its third Economic Index, a wide-ranging study of Claude AI usage across countries, […]

Why Your SOC Needs XDR to Automate Threat Detection and Containment
Your SOC scrambles when alerts flood in: disparate tools, manual triage, and slow follow-through mean attackers […]
Best AI Tools for Party Planning
Throwing a party sounds fun, but often, you find yourself drowning in theme ideas, endless guest […]

Deception Technology in Banking: A New Line of Defense Against Insider Threats and Fraud
When Your Most Trusted Employees Become Your Greatest Threat Insider threats cost organizations an average of […]
FTC Presses Meta, OpenAI, Others on Kids’ AI Chatbot Exposure
The Federal Trade Commission has launched a sweeping inquiry into AI chatbots, pressing seven tech giants […]
OpenAI and Microsoft Seem to Have Set Aside Their Differences and Settled on a Deal
In what’s called a “non-binding” memo of understanding (MOU), Microsoft and OpenAI put out a joint statement […]
Enabling Agentic AI: Why Data Strategy Is Now Business Strategy
In this episode of eSpeaks, host Corey Noles explores “Enabling Agentic AI: Why Data Strategy Is […]
How Will Agentic AI Change Enterprise Data Management in 2026 and Beyond?
SUB: Reltio CEO Manish Sood explains why “agentic AI” will first transform data matching and merging, […]
Anthropic Backs SB 53 – California’s Landmark AI Safety Bill
California is moving ahead with a state bill that would require transparency and safety reporting for […]
With AI Looming, NFL Legend Emmitt Smith Tells FABTECH Audience to Embrace Change
AI is reshaping nearly every sector and industry. So, it was fitting that NFL Hall of […]