Microsoft AI CEO on the Danger of Considering AI Conscious: ‘There is Nothing Inside’
One of the recurring themes in conversations about generative AI is its ability to mimic human […]
Alibaba’s ‘Most Powerful’ AI Model: Qwen3-Max Packs 1 Trillion Parameters
Alibaba has released its most powerful AI model yet, the Qwen3-Max, a system with more than […]
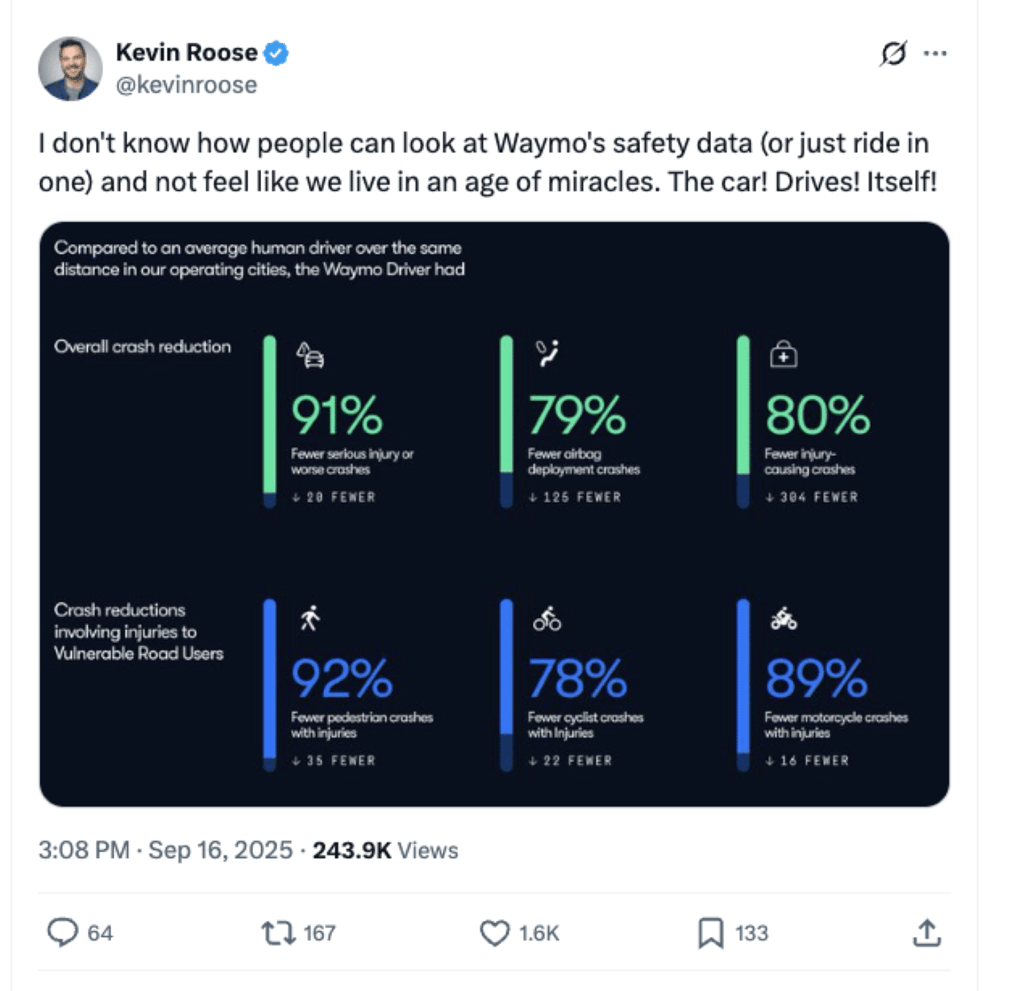
Waymo’s Safety Stats Are So Good, Even the Skeptics Are Running Out of Arguments
It’s been about a year since we last covered Alphabet’s driverless car company Waymo. Since then, […]
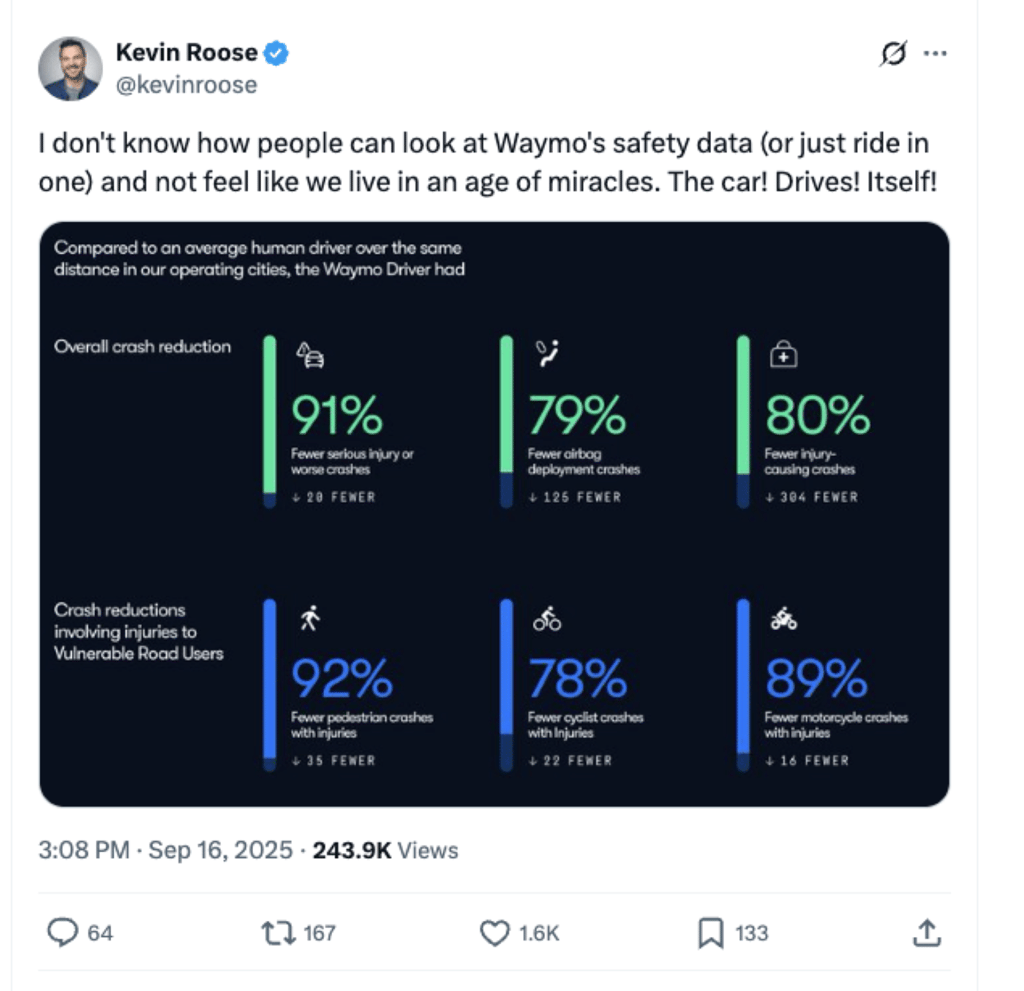
Waymo’s Safety Stats Are So Good, Even the Skeptics Are Running Out of Arguments
It’s been about a year since we last covered Alphabet’s driverless car company Waymo. Since then, […]
California Court Issues $10,000 ‘Warning’ Over Lawyer’s ChatGPT Brief
A California appeals court has fined Los Angeles attorney Amir Mostafavi $10,000 after he filed a […]

Turning Cloud Security Best Practices into Action with XDR
What once seemed like an optional upgrade has now become mission-critical: cloud security sits at the […]
Microsoft to Launch Marketplace for Publishers to Sell Content to AI Companies
Microsoft is planning to launch a marketplace that will allow publishers to sell their content to […]
Over 200 Leaders Demand Binding Global AI Rules Before It’s Too Late
Over 200 scientists and politicians, including Nobel Laureates and former heads of state, are calling for […]
OpenAI’s First Consumer Device Will Be Built by Apple Supplier Luxshare
Shares of Luxshare Precision Industry surged 10% on Monday after reports linked the Apple supplier to […]
AI Tool Predicts Health Problems in Patients 20 Years Before They Emerge
An artificial intelligence system called Delphi-2M is pushing the boundaries of predictive medicine, estimating a person’s […]