OpenAI Strikes Landmark Chip Deal with AMD to Power Next-Gen AI
OpenAI just fired the loudest shot yet in Silicon Valley’s artificial intelligence hardware war. The ChatGPT […]
Claude Sonnet 4.5 Marks Anthropic’s Pivot Toward AI-Powered Cyber Defense
Anthropic claims that AI has reached a turning point in cybersecurity, stating that its Claude Sonnet […]
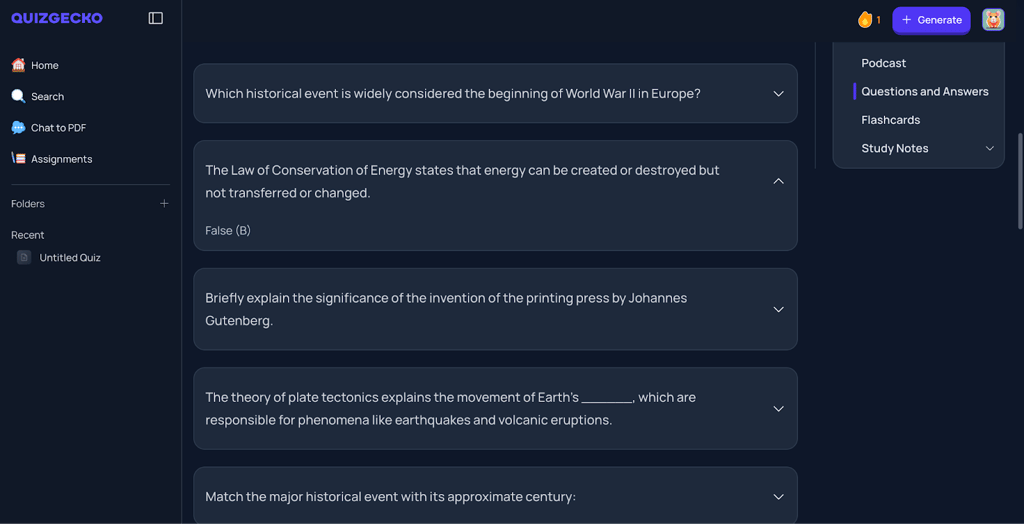
Best AI Tools for Trivia Fans
Trivia isn’t just a game — it’s a way to learn, connect, and show off your […]
OpenAI Is Going To Let Copyright Holders Opt Out of Sora 2
All copyright holders will soon be able to define how, and if, their work is recreated […]
OpenAI’s Billion-Dollar Bet to Power the Next AI Revolution
OpenAI is making a billion-dollar bet on power. The company is shifting from renting cloud space […]
‘Up to 100%’ of AI-Crafted Toxins Escape DNA Screens, Microsoft-Led Team Finds
AI has been used to paraphrase deadly proteins in ways that slipped past DNA security safeguards. […]
Mira Murati’s AI Lab Releases Its First Product, an API for Fine-Tuning LLMs
Former OpenAI CTO Mira Murati’s startup, Thinking Machines Lab, has revealed its first product: Tinker, an […]
OpenAI Reaches $500B Valuation
Investors have purchased OpenAI stock owned by employees, setting a new valuation that makes the ChatGPT […]
Meta Will Use AI Chats for Personalization, Calling It ‘Natural Progression’
Meta announced it will begin using conversations with its AI assistant to shape the ads and […]
AI Scientists Just Got $300M and a Robot Army
Periodic Labs, backed by Andreessen Horowitz (a16z), Nvidia, Jeff Bezos, and Eric Schmidt, aims to solve […]