Sam Altman: Jobs in the Intelligence Era Are ‘Not Real Work’
What is in a job? Well, according to OpenAI CEO Sam Altman, jobs created by the […]
Nvidia Brings Open-Source Innovation to AI Factories at OCP 2025
This week at the Open Compute Project (OCP) Global Summit, Nvidia shared its plans for what […]
Google Plans $15B AI Hub in India
Google has announced its first artificial intelligence hub in India, marking a major milestone in the […]
California Enacts First-in-the-Nation Law to Shield Children from AI Chatbots
California Governor Gavin Newsom on Monday signed a batch of bills aimed at protecting children from […]
Neuroscientists Sue Apple over Alleged Use of Pirated Books to Train AI Models
Apple faces more allegations as two U.S. neuroscientists have filed a federal lawsuit accusing the company […]
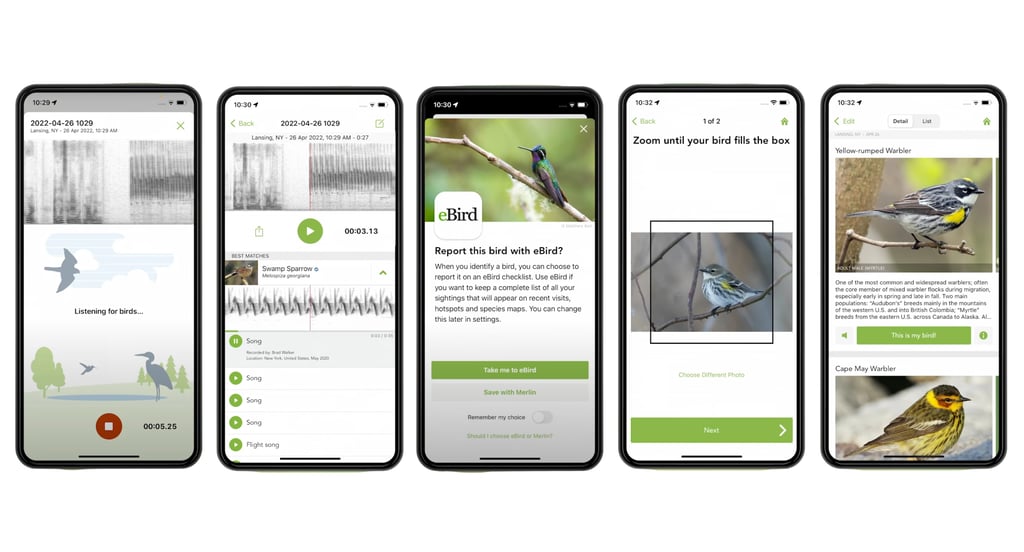
Best AI Tools for Birders
For birders, spotting a flash of feathers and not knowing its name can be frustrating, especially […]
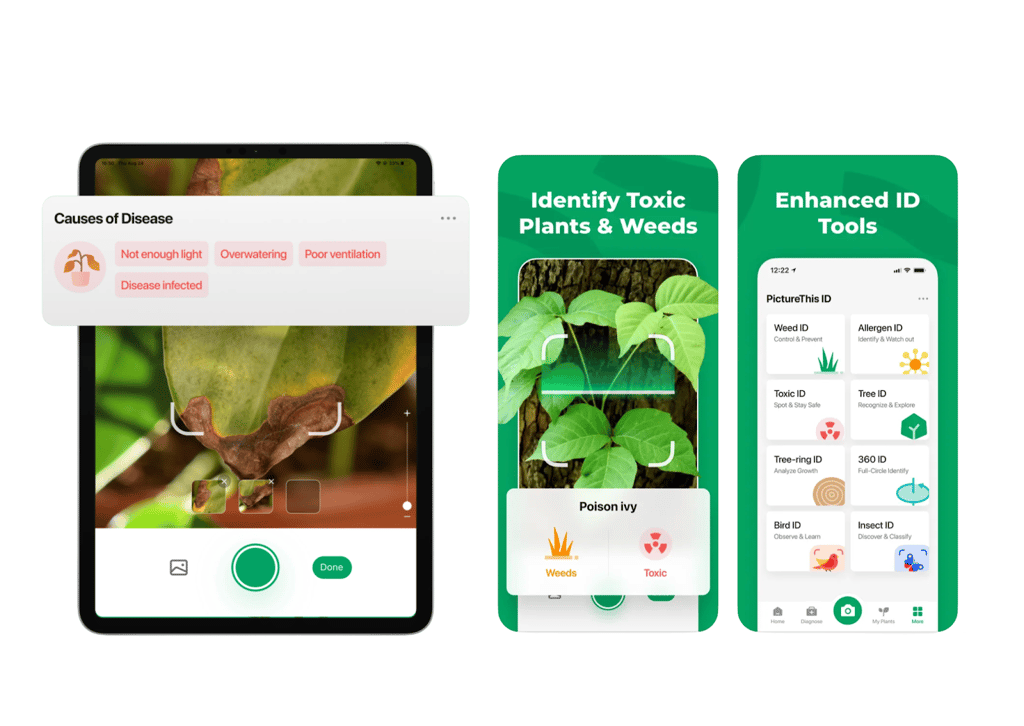
Best AI Tools for Gardening
For people like me who don’t have a green thumb, gardening can feel overwhelming. Here’s the […]

Is Figure 03 the ‘Model T’ moment for robots?
Figure AI just dropped Figure 03, and holy moly: this might be the first humanoid robot […]
AI Tools Flood Workplaces With ‘Workslop,’ Hurting Productivity and Team Trust
AI was supposed to make work cleaner. Instead, it’s making a mess. Across US workplaces, a […]
OpenAI Partners With Broadcom to Build Its Own AI Chip
Take note, Nvidia: OpenAI is tightening its grip on the AI economy. With a new partnership, […]