All About Logic Bombs: Your Computer Could Be Hijacked With Malware
Most users are familiar with viruses, trojans and worms. But there is a special type of […]
All About Logic Bombs: Your Computer Could Be Hijacked With Malware
Most users are familiar with viruses, trojans and worms. But there is a special type of […]
Port Binding Shellcode Remote Shellcode
When a host is exploited remotely, a multitude of options are available to gain access to […]

Port Binding Shellcode Remote Shellcode
When a host is exploited remotely, a multitude of options are available to gain access to […]
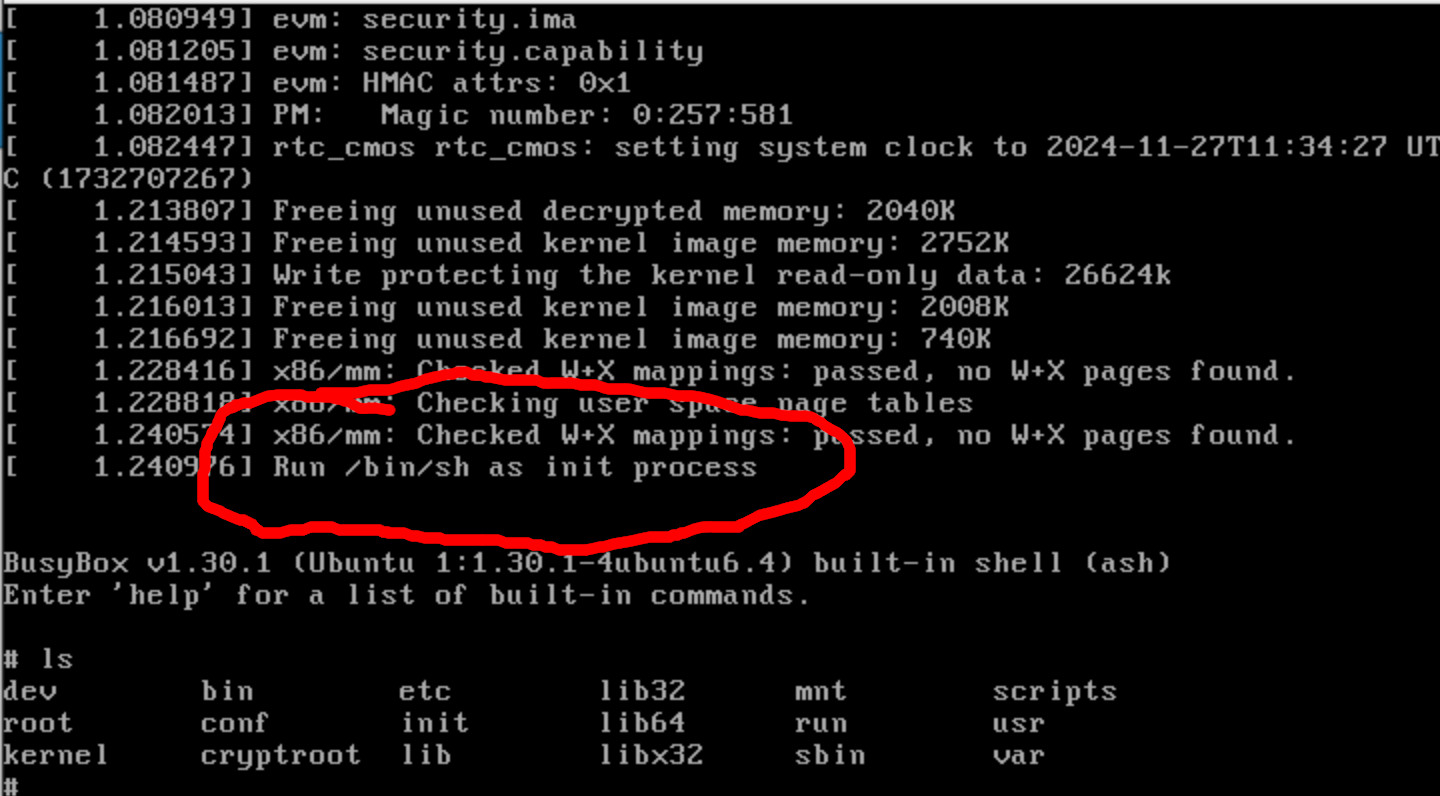
GRUB LUKS Bypass and Dump
Recently, I needed to get the data off of a LUKS encrypted partition on a Virtual […]

GRUB LUKS Bypass and Dump
Recently, I needed to get the data off of a LUKS encrypted partition on a Virtual […]
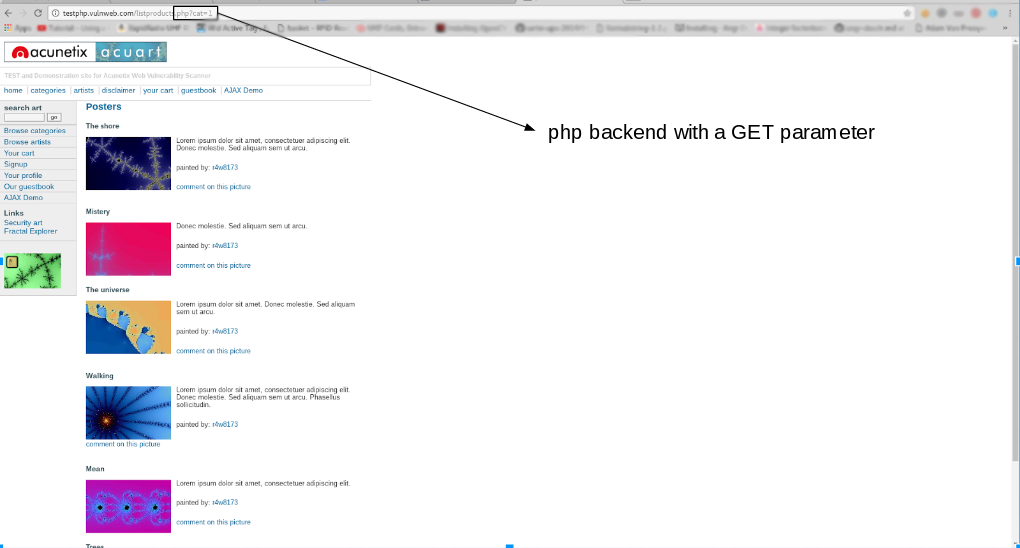
Unleashing the Power of SQL Injection Testing with SQLMap : A Comprehensive Guide
Sqlmap is a Python-based tool, which means it will usually run on any system with Python. […]

Unleashing the Power of SQL Injection Testing with SQLMap : A Comprehensive Guide
Sqlmap is a Python-based tool, which means it will usually run on any system with Python. […]
Can Port Scanning Crash the Target Computer or Network
So, you’ve probably heard of port scanning in movies or tech blogs, where hackers “scan” networks […]
Can Port Scanning Crash the Target Computer or Network
So, you’ve probably heard of port scanning in movies or tech blogs, where hackers “scan” networks […]