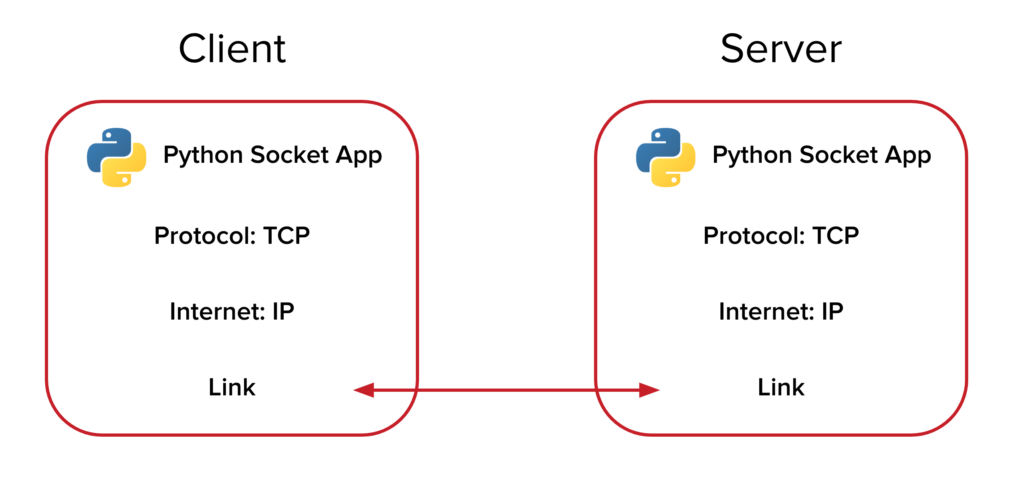
Building a Malicious Backdoor & C2 Server in Python
Backdoors and Command & Control (C2) servers are some of the tools used in cyberattacks to […]
Mastering Linux: The Top Commands Every Server Administrator Should Know
As a Linux system administrator, you must understand how to configure and manage your Linux servers […]

So You Want to Be a Hacker: 2025 Edition
Growing up in the 90s inundated me with images of hackers portrayed as mysterious, hoodie-clad figures […]
Nmap Cheat Sheet 2025
Nmap is a powerful and versatile network scanning tool used by network administrators, security professionals, and […]
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!

Master Shell Scripting– Zero to Interview Ready!🔥
Have you ever found yourself doing the same monotonous task over and over again on your […]

Master Shell Scripting– Zero to Interview Ready!🔥
Have you ever found yourself doing the same monotonous task over and over again on your […]
Basic Network Concepts for Hacking
If you’re stepping into the world of ethical hacking, then network knowledge isn’t just helpful but […]
Basic Network Concepts for Hacking
If you’re stepping into the world of ethical hacking, then network knowledge isn’t just helpful but […]