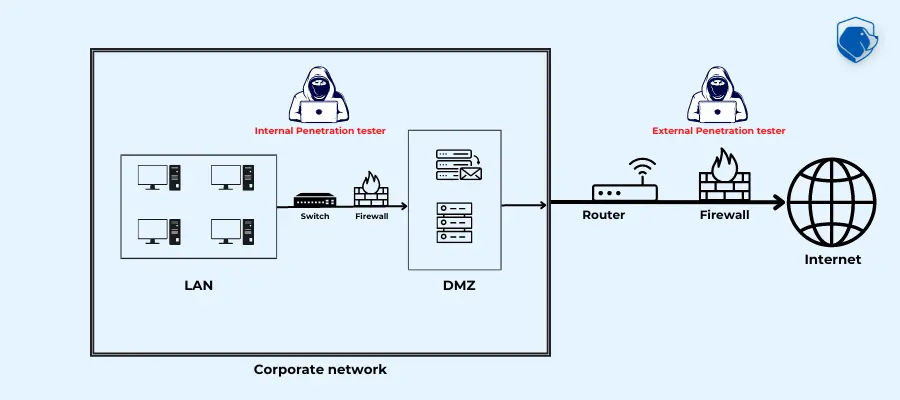
Automated Pentesting: The Future of Network Security
Greetings to all! Welcome to our exploration of network security’s future, with a particular focus on […]

Struggling to Find Your Next Job in Cybersecurity?
Finding your next job in cybersecurity can feel like navigating a maze. If you are beginning […]
Bug Bounties: Hacking For a Paycheck
Bug bounties are like digital treasure hunts for hackers—except instead of hidden gold, they’re looking for […]
What is a cyberattack?
What is a cyberattack? Cyberattacks aim to damage or gain control or access to important documents […]
What is SIEM ?
Security information and event management, SIEM for short, is a solution that helps organizations detect, analyze, […]

How to Use Netcat Commands: Examples and Cheat Sheets
Hey there! We can describe Netcat as a penetration testing tool, or networking Swiss army knife […]

Leveraging OSINT for User Privacy in Linux
Have you ever wondered how some people find all sorts of information on the internet? That’s […]

🛠️ Essential Resources to Start Your Hacking Journey
Hey there, future hacker! 🎩 You want to get your feet wet in the exciting world […]
Automate Everything With Python and Bash
Hey there! You ever think about how amazing it would be to just automate your life […]

Learning Linux? Start Here
Admittedly, getting into Linux can be a bit confusing if you’re doing it for the first […]