How to Crack PDF File Password using John the Ripper
Hello guys, in this tutorial, we will show that how we can decrypt or crack the […]

How to Crack PDF File Password using John the Ripper
Hello guys, in this tutorial, we will show that how we can decrypt or crack the […]
Safeguarding the Backbone of the Global Economy: OT/ICS Security in the Oil and Gas Industry
The oil and gas industry is an essential pillar of the global economy, enabling energy production, […]
Detailed Guide to SOAR and SIEM
What Is SOAR? SOAR stands for Security Orchestration, Automation, and Response. It’s a cybersecurity tool designed […]

Ethical Hacking Roadmap – A Beginners Guide
Originally, the term “hacker” was defined as a professional programmer with knowledge of machine code and […]
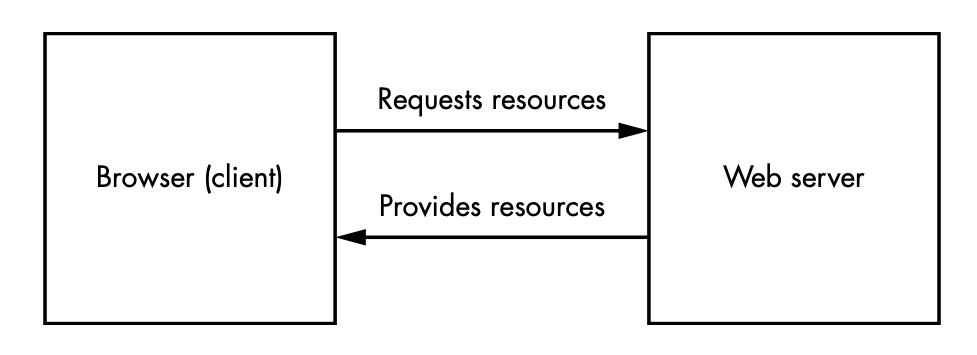
How the Internet Works | A Detailed Guide
Before we start troubleshooting, let’s take some time to understand how the network works. Finding web […]
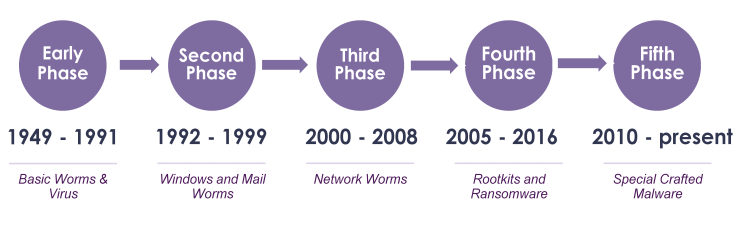
Introduction to Malware : Everything You Need To Know
🕵️♂️ Ever heard of that mysterious word “malware” buzzing around the digital jungle? No worries if […]

Mastering Wireshark: A Comprehensive Tutorial and Tips for Network Analysis
Wireshark is a powerful network protocol analyzer that allows you to see what’s happening on your […]

Exploring Metasploit: The Powerhouse of Penetration Testing
In a world where cybercrime is running wild, it’s high time we gear up and learn […]
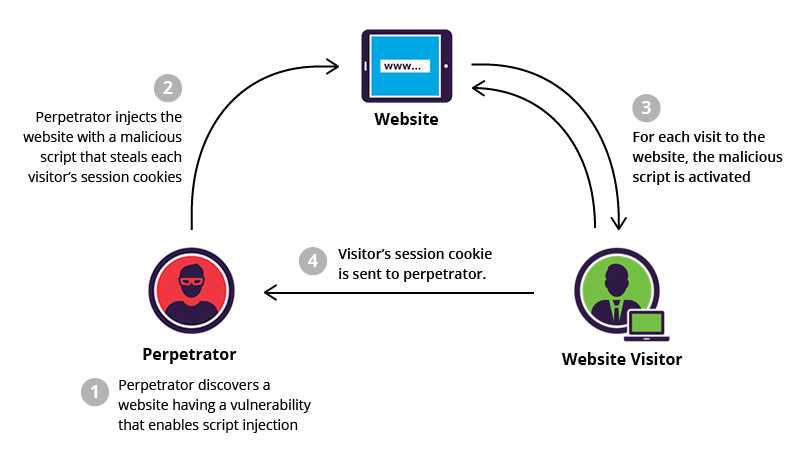
XSS 101: Understanding the Basics of Cross-Site Scripting (XSS) Vulnerabilities
Yooo mates, it’s Rocky here! Hope you’re all pumped up because today we’re diving into another […]