
How talent-strapped CISOs can tap former federal government cyber pros
Since January, thousands of federal government jobs have vanished through a combination of firings, layoffs and […]

End of life for Microsoft Office puts malicious macros in the security spotlight
The upcoming end of life for Windows 10 has IT teams busy. From planning on migrations, […]

Discovery of compromised Shellter security tool raises disclosure debate
CISOs whose staff use the commercial Shellter Elite antivirus evasion software to detect vulnerabilities need to […]

Real-time Web Traffic Analysis: Why Your Security Stack Needs It Now
Web attacks have exploded in complexity. Hackers no longer send obvious malware through email attachments. They […]

Cyber Attack Simulation: Test Your Security Before Hackers Do
As per the IBM cost of Data Breach report – the average global cost of a […]

NightEagle hackers exploit Microsoft Exchange flaw to spy on China’s strategic sectors
A previously undocumented Advanced Persistent Threat (APT) group, “NightEagle,” has been found targeting the Chinese government […]

Ingram Micro confirms ransomware attack after days of downtime
Ingram Micro is facing a major cybersecurity crisis as a ransomware attack has triggered a multi-day […]
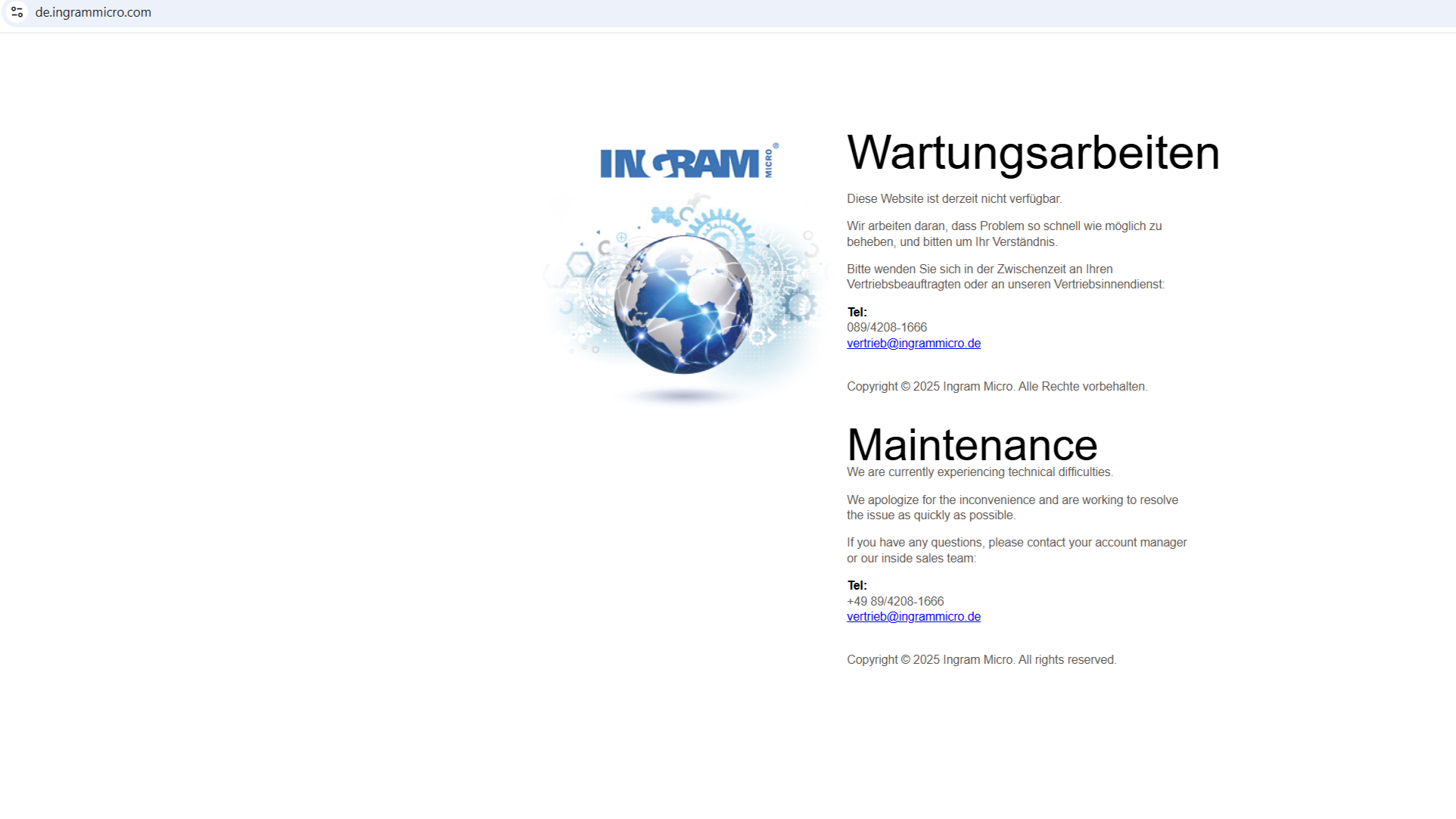
Ransomware-Attacke auf Ingram Micro
Die Webseiten von Ingram Micro sind aufgrund einer Cyberattacke aktuell nicht erreichbar. Screenshot by Foundry / […]

Has CISO become the least desirable role in business?
After nine years as CSO and senior vice president of IT at Sumo Logic, George Gerchow […]

Skills gaps send CISOs in search of managed security providers
A shortage of skilled cybersecurity professionals, combined with budget cuts, is fueling growth in the managed […]
