
Access Management Systems sind offene Türen für Hacker
Wenn Hacker biometrische Zugangsdaten erbeuten, können Sie erhebliche Schäden anrichten. shuttertsock – itj aks zoone Fehler […]

60% of cybersecurity pros looking to change employers
Cybersecurity worker job satisfaction is mediocre with many staff actively considering a change. Only a third […]

The risks of standing down: Why halting US cyber ops against Russia erodes deterrence
The recent order directing US Cyber Command to halt all planning of offensive cyber operations against […]

Building Malware with Python: Writing Ransomware, Keyloggers & Reverse Shells from Scratch
Hey guys, Rocky here! So you’re curious how malware actually works? Maybe you’re wondering why ransomware […]

Building Malware with Python: Writing Ransomware, Keyloggers & Reverse Shells from Scratch
Hey guys, Rocky here! 👋 So you’re curious how malware actually works? Maybe you’re wondering why […]

Building Malware with Python: Writing Ransomware, Keyloggers & Reverse Shells from Scratch
Hey guys, Rocky here! 👋 So you’re curious how malware actually works? Maybe you’re wondering why […]

Ransomware goes postal: US healthcare firms receive fake extortion letters
In late February, healthcare organizations across the US started receiving extortion demands by mail claiming that […]

Polnische Raumfahrtbehörde kämpft mit Cyberattacke
Die polnische Raumfahrtbehörde POLSA wurde Ziel eines Cyberangriffs. BUTENKOV ALEKSEI – Shutterstock.com Wie die polnische Raumfahrtbehörde […]

So werden PV-Anlagen digital angegriffen und geschützt
Unternehmen setzen vermehrt auf Solaranlagen mit Batteriespeichern, um hohe Energiekosten und Netzstabilitätsrisiken zu minimieren. Diese Systeme […]
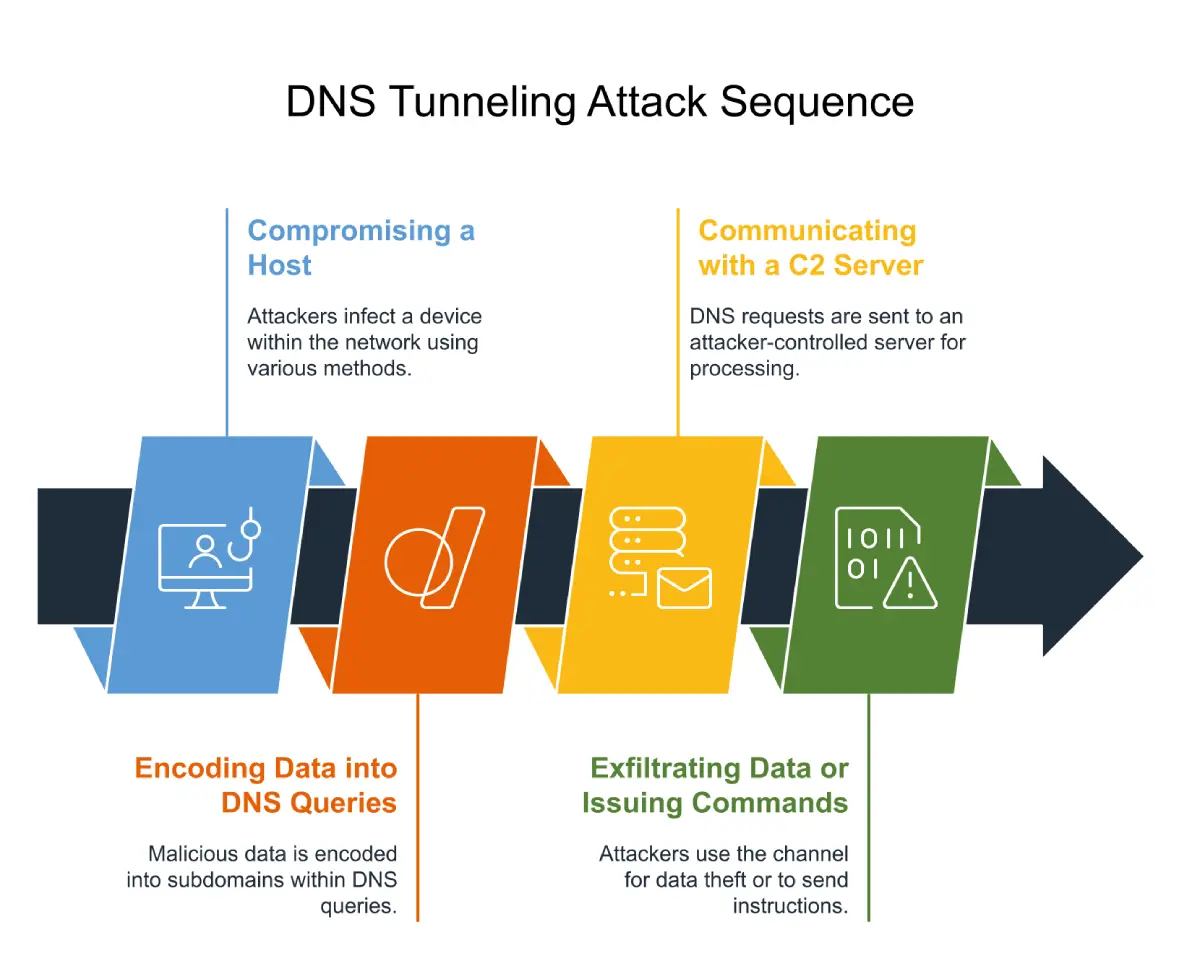
Detecting and Controlling Hidden DNS Tunnel Attacks
DNS is the backbone of the internet, translating domain names into IP addresses to facilitate communication […]
