
FBI takes down Cracked.to and Nulled.to in a global law enforcement operation
FBI has taken down Cracked.to, Nulled.to, and a few other hack sites cybercriminals use for dropping […]

What is Magecart? How this hacker group steals payment card data
Magecart definition Magecart is a consortium of malicious hacker groups who target online shopping cart systems, […]

American CISOs should prepare now for the coming connected-vehicle tech bans
In a groundbreaking shift in automotive supply chain regulation, the White House announced a new rule […]

5 teure Threat-Intelligence-Fehler
Fehlgeleitete Threat-Intelligence-Programme lassen (nicht nur) Ihr Security-Budget schmelzen. Vitalii Stock | shutterstock.com Ausgeprägte Fähigkeiten im Bereich […]
New Mirai botnet fires off DDoS attacks via compromised Mitel phones, notifies command & control when detected
A third variant of the Mirai-based Aquabot malware is apparently taking over Mitel phones to create […]

Threat actors using Google Gemini to amplify attacks: Report
Government-backed threat actors are currently using Google’s Gemini AI service to expand their capabilities, part of […]
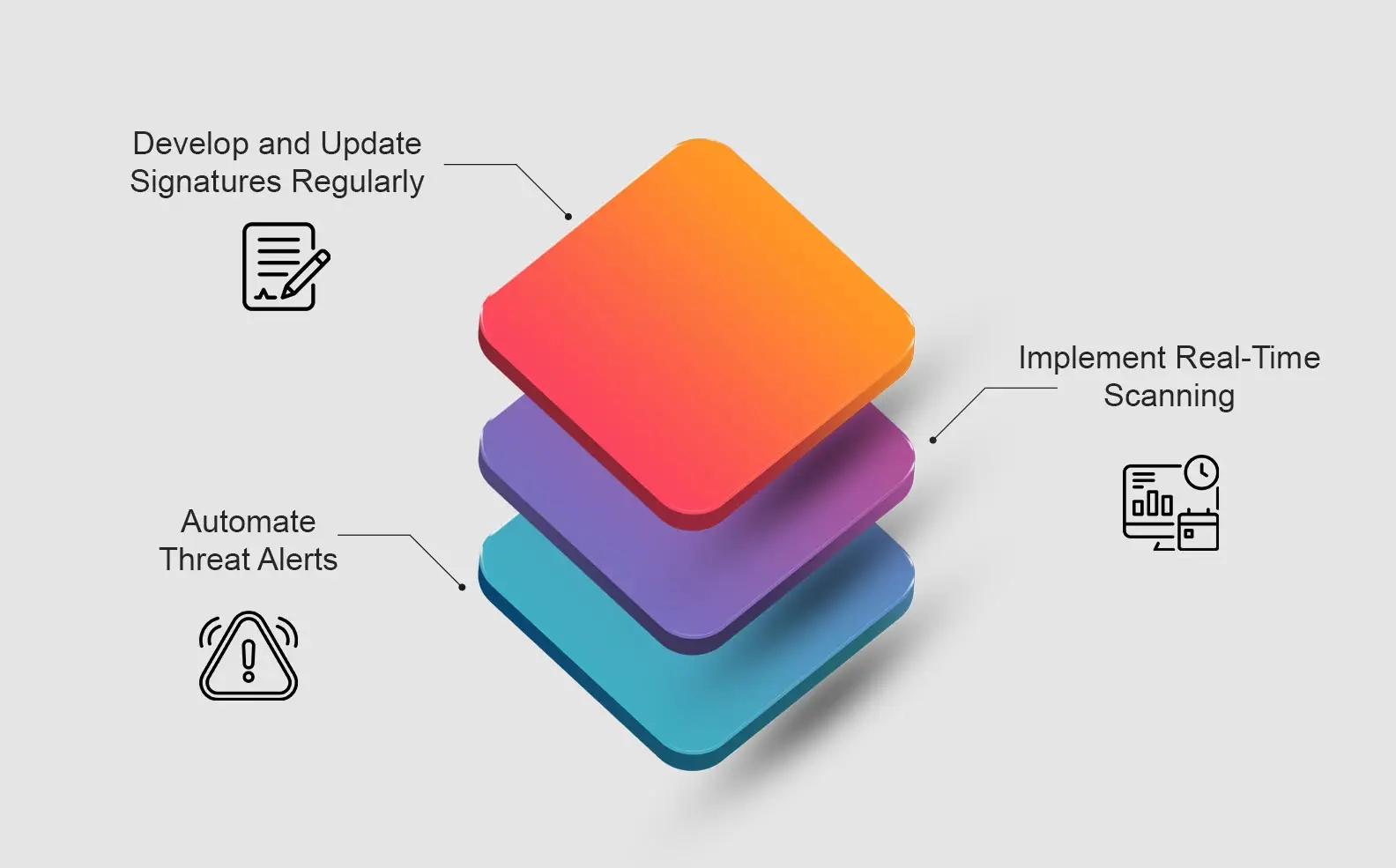
Breaking Down Signature-Based Detection: A Practical Guide
Nearly 90% of cyberattacks are known methods that proper systems can detect, but most organizations don’t […]

Ransomware: Schwere Versäumnisse in deutschen Unternehmen
Laut einer Umfrage benötigen deutsche Unternehmen im Vergleich zu anderen Ländern mehr Zeit und Geld, um […]

Download our security information and event management (SIEM) tools buyer’s guide
From the editors of CSO, this enterprise buyer’s guide helps IT security staff understand what SIEM […]

New phishing campaign targets users in Poland and Germany
An ongoing phishing campaign, presumably by an advanced persistent threat (APT) actor, is seen dropping a […]
