
Old threats, new consequences: 90% of cyber claims stem from email and remote access
Even as attackers are growing ever more sophisticated in their methods, it seems there’s no point […]

Zehntausende Exchange-Server in Deutschland gefährdet
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2626268707.jpg?quality=50&strip=all 6240w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2626268707.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2626268707.jpg?resize=768%2C431&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2626268707.jpg?resize=1024%2C575&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2626268707.jpg?resize=1536%2C863&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2626268707.jpg?resize=2048%2C1150&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2626268707.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2626268707.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

BlueNoroff reemerges with new campaigns for crypto theft and espionage
North Korea-aligned threat actor BlueNoroff, also known under aliases APT38 and TA444, has resurfaced with two […]

Ransomware-Attacke auf schwedischen Stromversorger
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2182279977.jpg?quality=50&strip=all 5474w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2182279977.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2182279977.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2182279977.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2182279977.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2182279977.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2182279977.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2182279977.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

Is your perimeter having an identity crisis?
For years, you’ve operated on a fundamental and fragile assumption that with enough training and the […]

Step-by-Step Guide to CNAPP Implementation: Securing Cloud-Native Applications
Key Takeaways CNAPP closes the security gaps traditional tools miss in dynamic cloud environments. It protects […]

Top 7 agentic AI use cases for cybersecurity
Agentic AI promises to revolutionize a wide range of IT operations and services, including cybersecurity. While […]
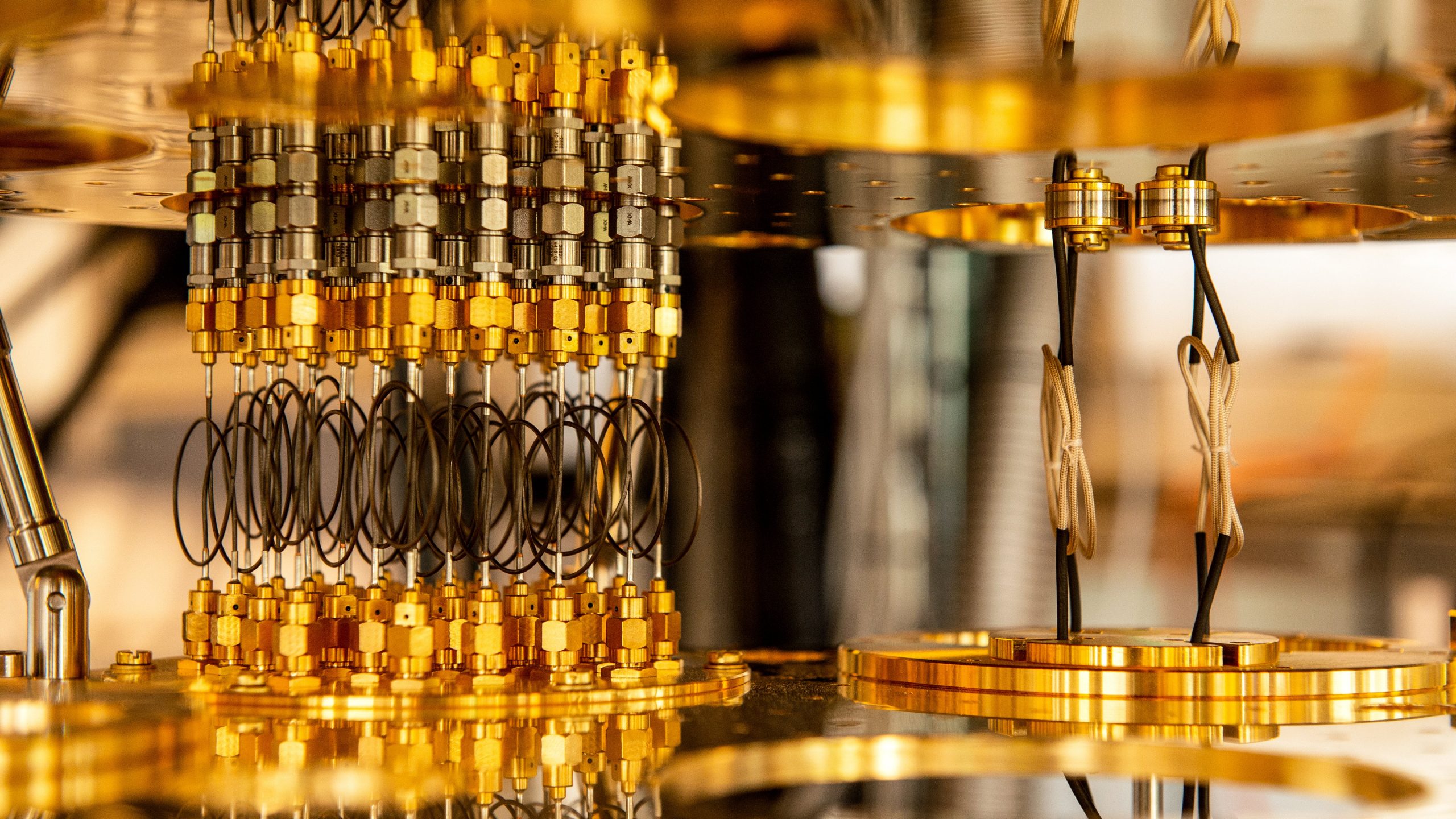
Notable post-quantum cryptography initiatives paving the way toward Q-Day
The point at which quantum computers will be capable of breaking existing cryptographic algorithms — known […]

Software Bill of Material umsetzen: Die besten SBOM-Tools
Nur wenn Sie wissen, was drinsteckt, können Sie sich sicher sein, dass alles mit rechten Dingen […]

Atroposia malware kit lowers the bar for cybercrime — and raises the stakes for enterprise defenders
Cybercrime is increasingly being commoditized, significantly lowering the bar for hackers and making things tougher for […]
