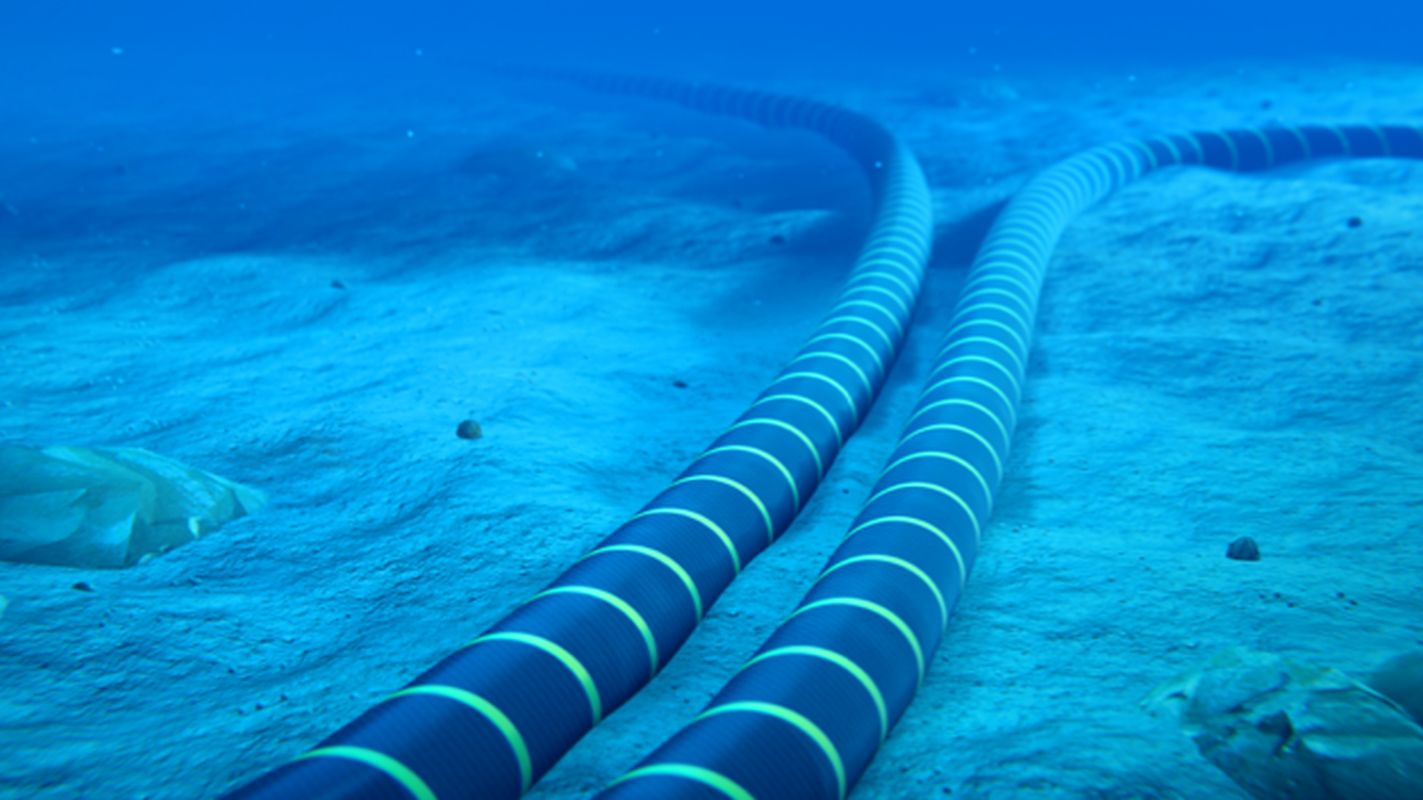
Submarine cable cybersecurity: protecting critical infrastructure
Between 95 and 99% of the world’s data traffic travels through submarine cables. An extensive network […]

Coach or mentor: What you need depends on where you are as a cyber leader
Renee Guttmann, a Fortune 50 CISO who has served at Time Warner, Coca-Cola, Royal Caribbean Cruises, […]

Wie Unternehmen sich gegen neue KI-Gefahren wappnen
KI ist nicht nur ein Tool für Hacker, sondern kann auch selbst zur Gefahr werden. inray27 […]

Developers urged to immediately upgrade React, Next.js
Developers using the React 19 library for building application interfaces are urged to immediately upgrade to […]

RCE flaw in OpenAI’s Codex CLI highlights new risks to dev environments
In a new example of how AI tools expand the attack surface of development machines, researchers […]

Hybrid 2FA phishing kits are making attacks harder to detect
Some 2FA-phishing attacks are becoming significantly harder to spot as threat actors blend two previously distinct […]

Get poetic in prompts and AI will break its guardrails
Poetry can be a perplexing art form for humans to decipher at times, and apparently AI […]

Neue bösartige Browser-Erweiterungen entdeckt
Cyberangreifer nutzen Chrome- und Edge-Add-ons zur Datenerfassung, Suchmanipulation und als Backdoor. Ascannio – shutterstock.com Forscher des […]

AI, automation, and integration: The foundation for cyber protection in 2026
Cyber protection grew more complex in 2025 as more threat actors turned to artificial intelligence (AI) […]

Cybersicherheit für viele Nebensache
Laut einer Umfrage informieren sich lediglich 54 Prozent der Deutschen regelmäßig über das Thema Cybersicherheit. Summit […]
