
10 best practices for vulnerability management according to CISOs
It was 2003, and I was giving my first cybersecurity presentation at an industry conference in […]
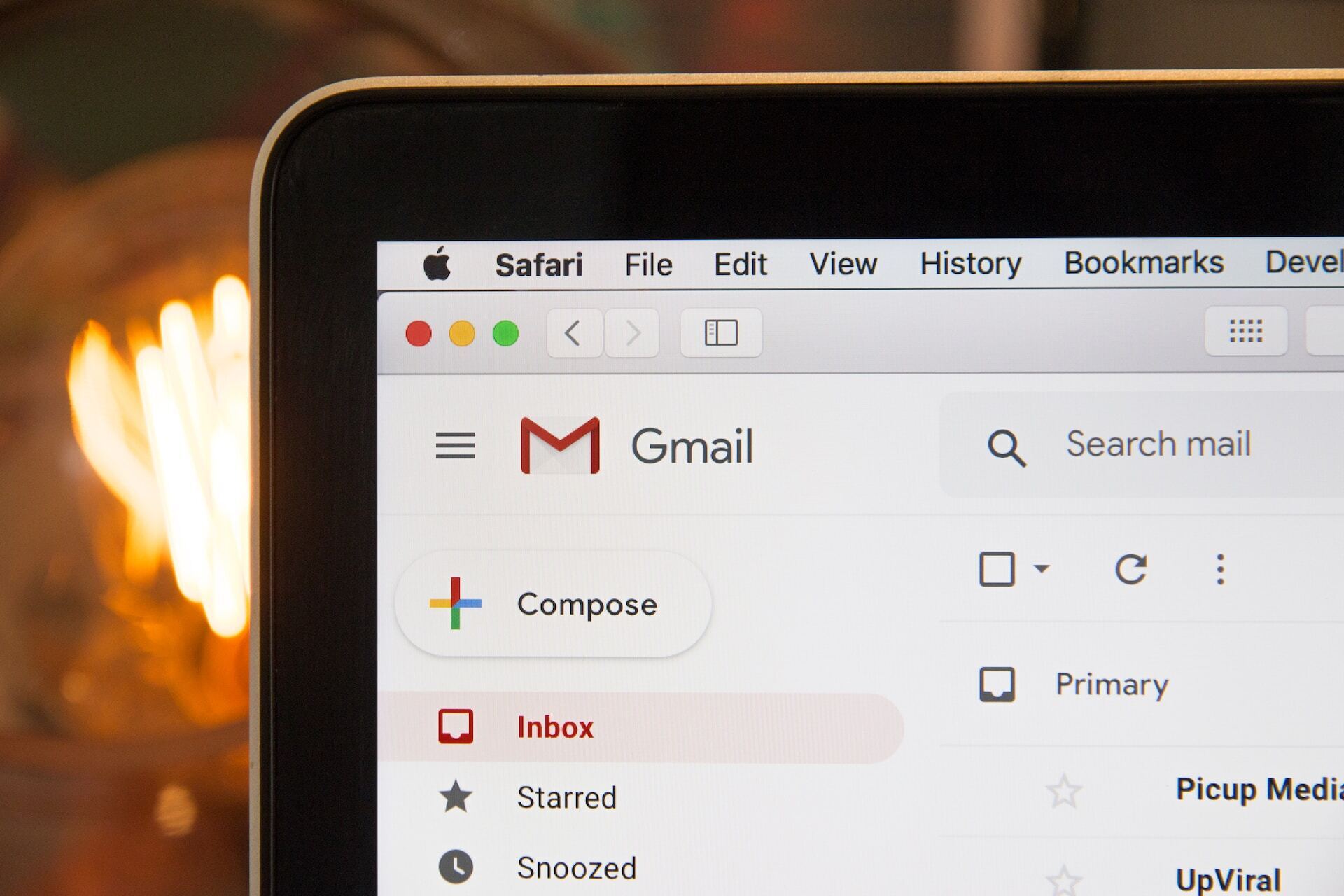
Google adds end-to-end email encryption to Gmail
Google has introduced a new end-to-end encryption (E2EE) feature in Gmail, enabling organizations to send encrypted […]

The UK’s Cyber Security and Resilience Bill will boost standards – and increase costs
If you’re a UK enterprise, this might not be good news: extra investment by infrastructure providers […]

The urgent reality of machine identity security in 2025
The importance of machine identity security has reached a critical juncture in 2025. With machine identities now far […]

How CISOs can use identity to advance zero trust
AI is the best thing that’s ever happened to cybercriminals. It allows them to weaponize trust […]

Download the Strategizing Data Analytics for AI Enterprise Spotlight
Download the April 2025 issue of the Enterprise Spotlight from the editors of CIO, Computerworld, CSO, […]

Altgeräte bedrohen Sicherheit in Unternehmen
width=”2500″ height=”1406″ sizes=”(max-width: 2500px) 100vw, 2500px”>Schwachstellen in alten Netzwerkgeräten stellen ein erhebliches Sicherheitsrisiko für Unternehmen dar. […]

Oracle warns customers of health data breach amid public denial
Oracle’s healthcare subsidiary, Oracle Health, has suffered a data breach, potentially exposing customers’ sensitive data, the […]

LLMs are now available in snack size but digest with care
As large language models (LLMs) gain mainstream, they are pushing the edges on AI-driven applications, adding […]

After fake employees, fake enterprises are next hiring threat to corporate data
Chinese companies are trying to cut Taiwan’s lead in semiconductor technology by hiring away its best […]
