
Worker distraction is on the rise. Digital employee experience (DEX) platforms can help
With the dramatic increase in remote work in the last few years, many of us are […]

Attackers hide malicious code in Hugging Face AI model Pickle files
Like all repositories of open-source software in recent years, AI model hosting platform Hugging Face has […]
What to Look for in an NDR Solution: A Buyer’s Guide to Cutting-Edge Features
As cyberattacks become more complex, network detection and response solutions have become essential for modern organizations. […]

Datenleck bei Vorwerk: Hacker stehlen Thermomix-Nutzerdaten
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2522798761.jpg?quality=50&strip=all 4400w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2522798761.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2522798761.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2522798761.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2522798761.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2522798761.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2522798761.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2522798761.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

Cisco’s ISE bugs could allow root-level command execution
Cisco is warning enterprise admins of two critical flaws within its identity and access management (IAM) […]

Mehr Cyberangriffe bei weniger Beute
Strengere Kontrollen bei Kryptobörsen zwingen Kriminelle, neue Wege zur Verschleierung ihrer Einnahmen zu finden. shutterstock.com – […]
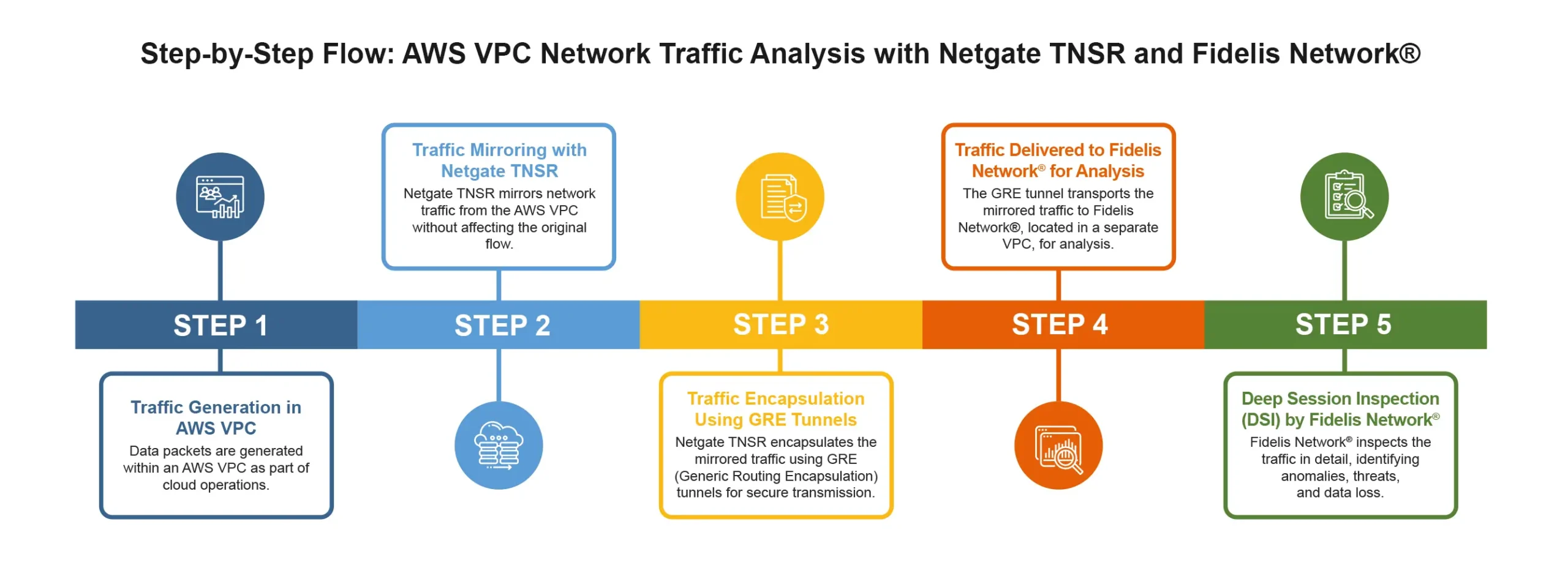
Fidelis Network® for Amazon VPC Traffic Mirroring
Over the last decade, cloud computing has become the backbone of modern business, transforming how organizations […]

CIOs and CISOs grapple with DORA: Key challenges, compliance complexities
In force since January, the Digital Operational Resilience Act (DORA) has required considerable effort from CIOs […]

Police arrest teenager suspected of hacking NATO and numerous Spanish institutions
Spain‘s National Police, in a joint operation with the Civil Guard, has arrested an 18-year-old suspected […]
Port Binding Shellcode Remote Shellcode
When a host is exploited remotely, a multitude of options are available to gain access to […]
